DES encryption algorithm based encryption method
An encryption method and encryption algorithm technology, applied to encryption devices with shift registers/memory, key distribution, can solve the problems of high probability of ciphertext being cracked, low efficiency, and special symbols of ciphertext are not suitable for network transmission, etc. Achieve the effects of increased difficulty in cracking, high efficiency, and convenient updates and upgrades
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
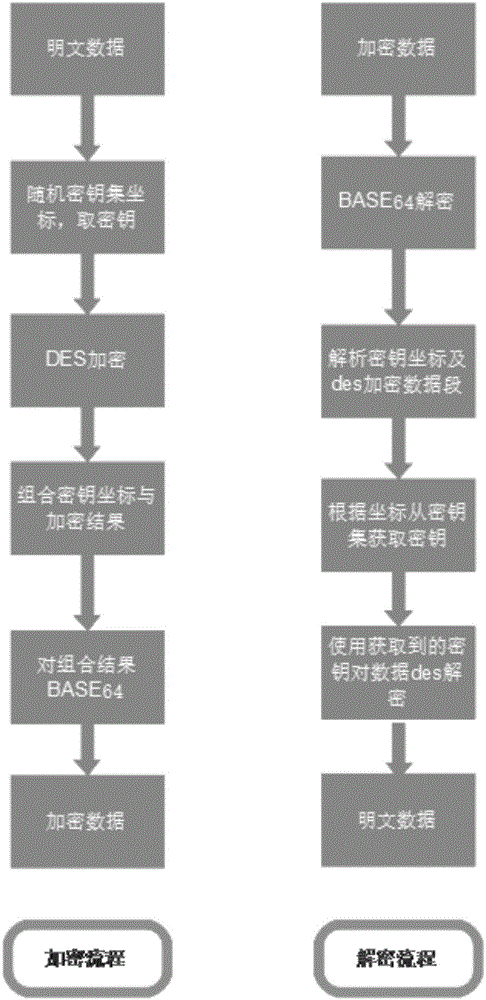
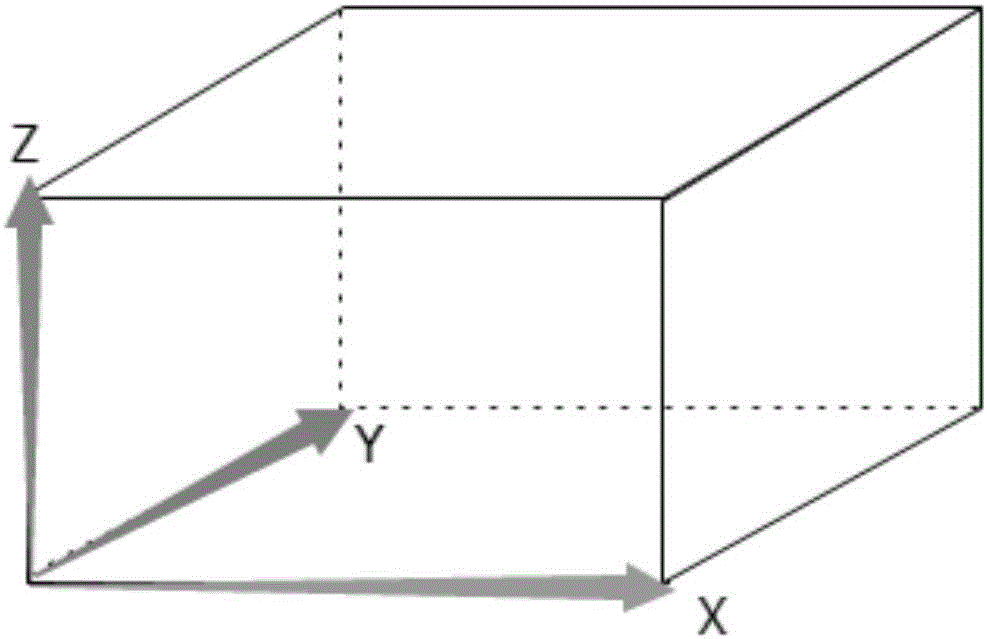
[0044] Step A, set up the key set file, the key set file is a cuboid three-dimensional model composed of three mutually perpendicular directions X, Y, Z, X, Y are key distribution coordinates, Z is a group of keys, and the key The total number of keys is equal to the product of X and Y; if X=2, Y=4, the total number of keys is 8;
[0045] Step B. The server side randomizes a coordinate within the effective value range of 2 and 4 in step A, determines a set of keys 3 and 6, and uses the key to perform DES encryption on the original data to be sent;
[0046] Step C, converting the values of 2 and 4 selected in step B into 4-digit hexadecimal numbers, and combining with the DES encryption result in step B;
[0047] Step D, encrypting the combination result of step C with BASE64 and sending it to the client;
[0048] Step E, after the client receives the BASE64 encrypted data sent in step D, it decrypts the BASE64 data, and then obtains the key from the key set according to the...
Embodiment 2
[0058] Step A, set up the key set file, the key set file is a cuboid three-dimensional model composed of three mutually perpendicular directions X, Y, Z, X, Y are key distribution coordinates, Z is a group of keys, and the key The total number of keys is equal to the product of X and Y; if X=1, Y=4, the total number of keys is 4;
[0059] Step B. The server side randomizes a coordinate within the effective value range of 1 and 4 in step A, determines a set of keys 2 and 3, and uses the key to perform DES encryption on the original data to be sent;
[0060] Step C, converting the 4 values selected in step B into 4 hexadecimal numbers, and combining with the DES encryption result in step B;
[0061] Step D, encrypting the combination result of step C with BASE64 and sending it to the client;
[0062] Step E, after the client receives the BASE64 encrypted data sent in step D, it decrypts the BASE64 data, and then obtains the key from the key set according to the XY coordinate ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com