Block chain block building method for Byzantine fault tolerant algorithm of quartic communication
A blockchain and sub-communication technology, applied in computing, instruments, payment systems, etc., can solve problems such as Byzantine errors, data inconsistencies, waste of resources, etc., and achieve increased block building speed, expanded usage scenarios, and improved verification speed Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
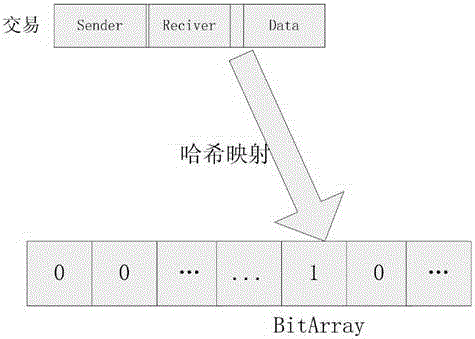
[0029] Assuming that there are 4 nodes (i.e. M=4) in the blockchain system, namely node A, node B, node C, and node D, when the method of the present invention is used to build a block, each node first maps the transaction to obtain a bitarray, such as figure 2 As shown, after getting the bitarray, the first communication is:
[0030] Node A: Map the received transaction to bitarray, get a bitarray and send it to nodes B, C, and D;
[0031]Node B: Map the received transaction to bitarray, get a bitarray and send it to nodes A, C, and D;
[0032] Node C: Map the received transaction to bitarray, get a bitarray and send it to nodes A, B, and D;
[0033] Node D: Map the received transaction to bitarray, get a bitarray and send it to nodes A, B, and C;
[0034] After the first communication, all nodes calculate the 2 / 3 intersection operation according to the obtained bitarray, and the operation result is recorded as ba, that is to say, if each bit has more than 2 / 3 of the bita...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com