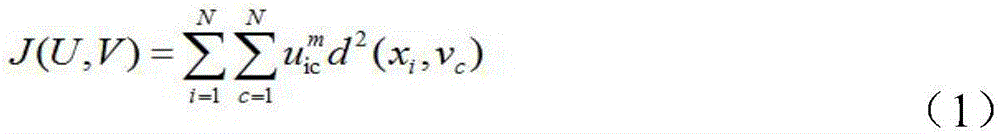Method for attacking software protection virtual machine based on fuzzy clustering
A technology of software protection and fuzzy clustering, which is applied in the computer field, can solve problems such as lack of versatility, time-consuming and labor-intensive, and inoperability, and achieve the effect of improving efficiency and strong versatility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] In order to make the object, technical solution and advantages of the present invention more clear, the present invention will be further described in detail below in conjunction with the examples. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
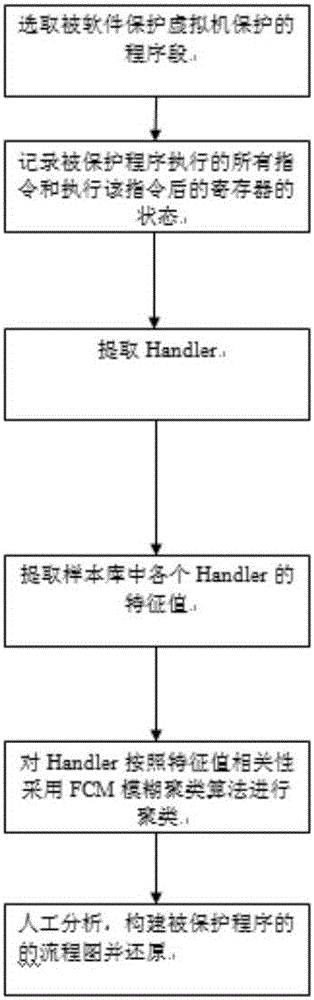
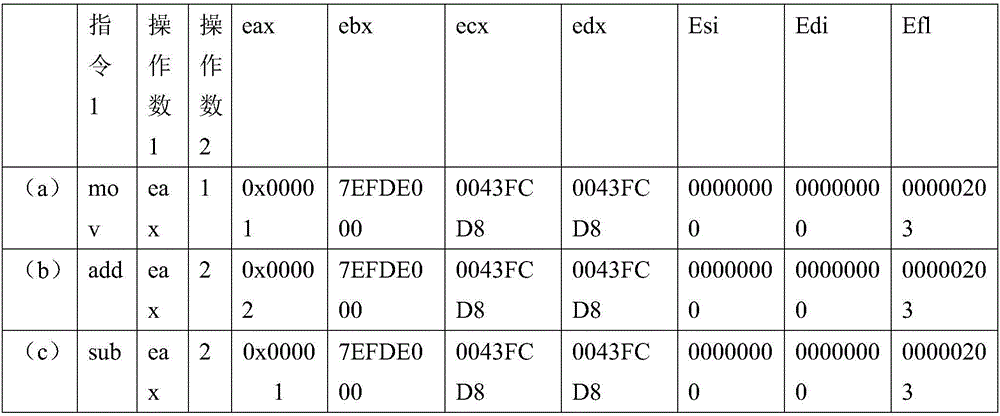
[0021] The software protection virtual machine attack plan test of the present invention, this test case adopts the program segment after being protected by VMP2. The flow chart is used to observe and compare the procedures before and after processing. The computer system platform used is Windows 7 64-bit Ultimate; CPU: Intel I5 4200M; memory: DDR3 8G; The input speed is 270M / s.
[0022] The present invention is based on fuzzy clustering software-protected virtual machine attack scheme, which enables the attack scheme of software-protected virtual machine to realize automatic processing to a certain extent, and provides a ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap