A virtualization platform security monitoring method and system
A virtualization platform and security monitoring technology, applied in the security monitoring method and system of the virtualization platform, and the security field of the virtualization platform, can solve the problems of monitoring and protection of the virtual machine monitor, inability to perform security monitoring, and high cost, and achieve the application wide range of effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments, but the scope of the present invention is not limited in any way.
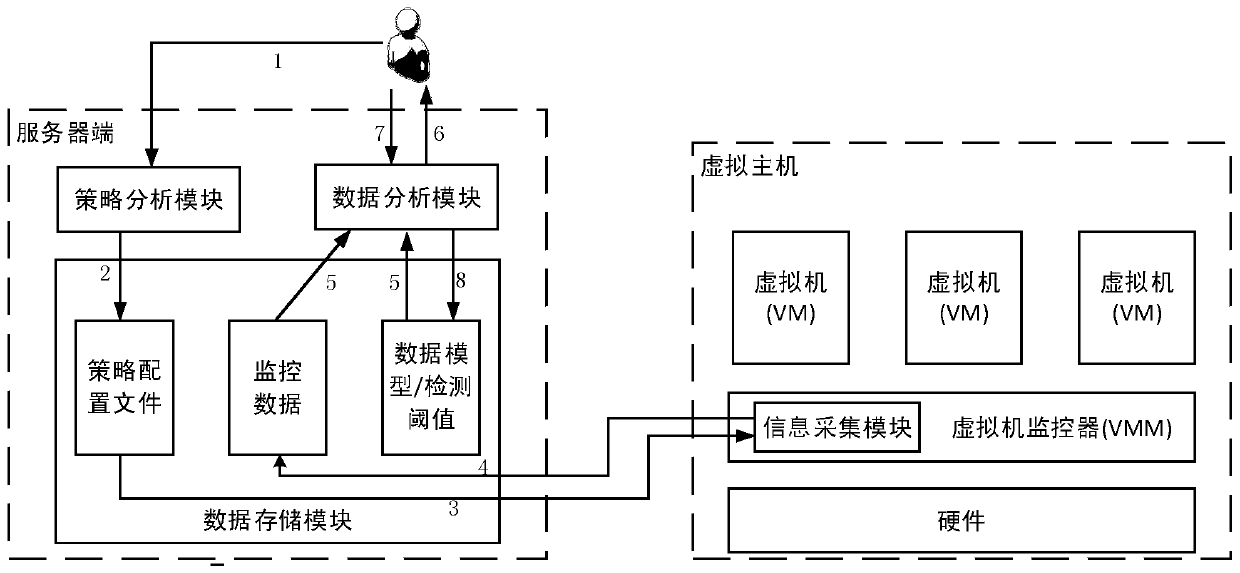
[0033] This embodiment adopts as figure 1 In the system structure shown, the server is installed on a separate host, and the client is deployed on the monitored virtual machine host.
[0034] Step 1: First, the user logs in to the system webpage and customizes his own security requirements as follows:
[0035] 1) Monitoring granularity: function level
[0036] 2) Virtual host IP network segment: 192.168.10.1--192.168.10.5
[0037] 3) Virtual host model: dell rack server R730,
[0038] 4) Virtual host VMM model: KVM (Kernel-Based Virtual Machine)
[0039] Step 2: The policy analysis component parses the above security requirements into an XML file conf.xml, and stores it in the data storage module (local file system). Afterwards, the server sends SSH requests to eac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com