Method and system for detecting zombie, trojan and worm networks
A botnet and botnet technology, applied in the field of Internet security, can solve problems such as botnet threats, and achieve the effects of extensive tracking, traffic reduction, and accurate topology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be described more fully hereinafter with reference to the accompanying drawings, in which exemplary embodiments of the invention are illustrated.
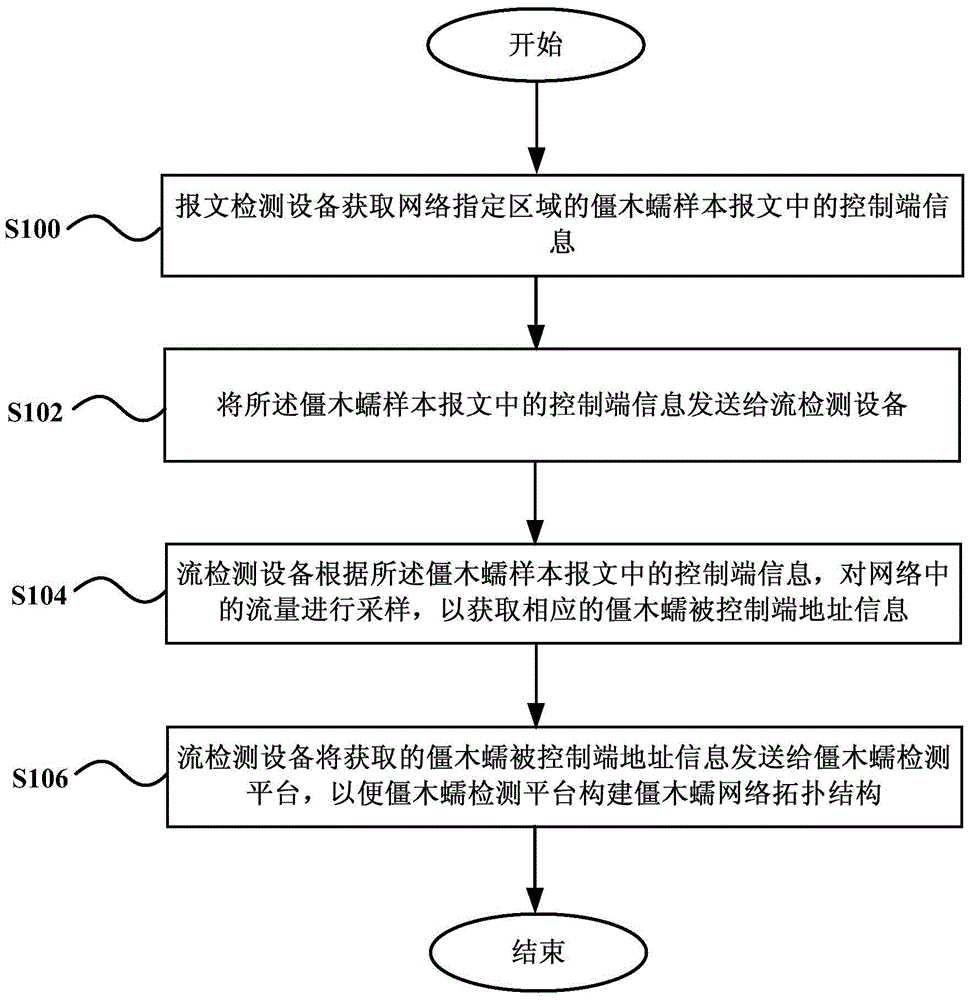
[0023] figure 1 A flowchart showing a method for detecting zombies and worms according to an embodiment of the present invention. Such as figure 1 As shown, the method mainly includes:
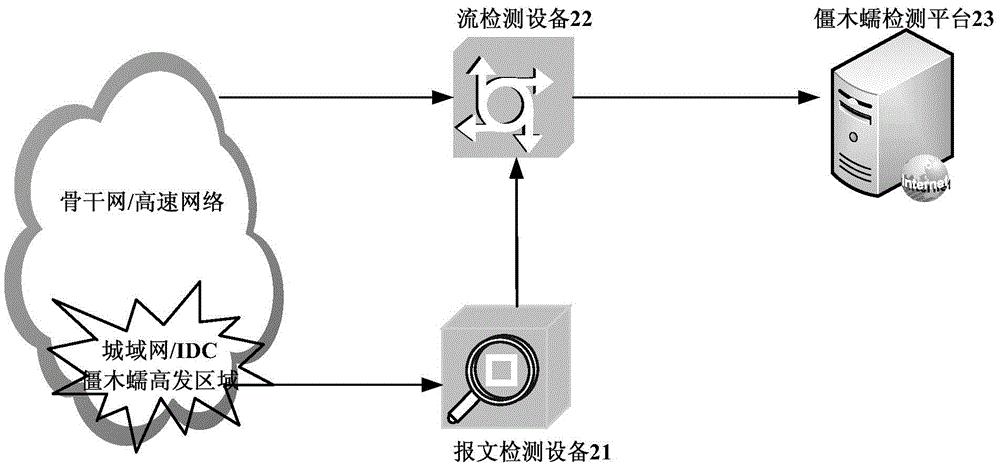
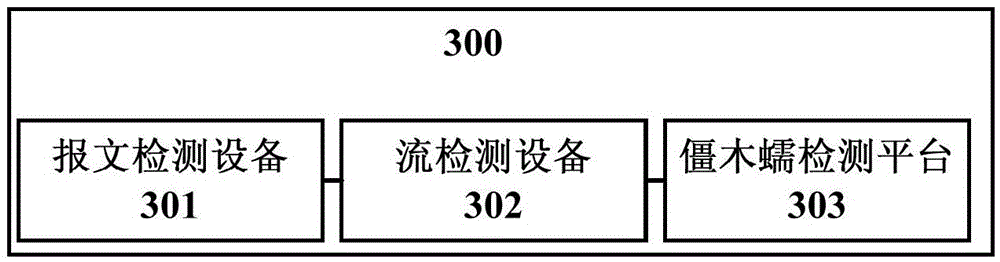
[0024] Step 100, the packet detection device obtains the control terminal information in the zombie worm sample packets in the designated area of the network.
[0025] Step 102, sending the control terminal information in the zombie worm sample message to the flow detection device.
[0026] Step 104, the flow detection device samples the traffic in the network according to the control terminal information in the zombie worm sample message, so as to obtain the corresponding address information of the zombie worm controlled terminal.
[0027] Step 106 , the flow detection device sends the acquired address infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com