A secure transmission method based on statistical QoS guarantee in cognitive wireless network
A cognitive wireless network and secure transmission technology, applied in the field of secure transmission based on statistical QoS, can solve the problems of reduced system throughput due to reliability and security, insufficient flexibility of evaluation performance indicators, and insufficient flexibility of QoS
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0127] The present invention will be described in further detail below in conjunction with the accompanying drawings.
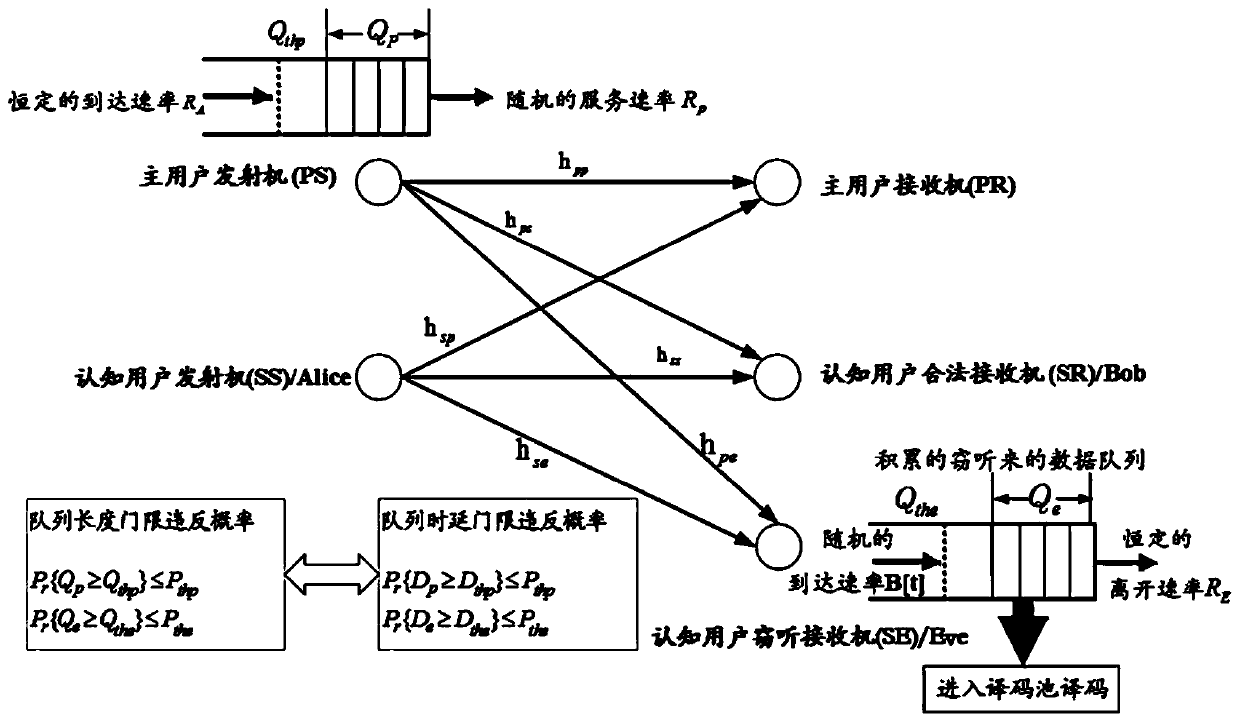
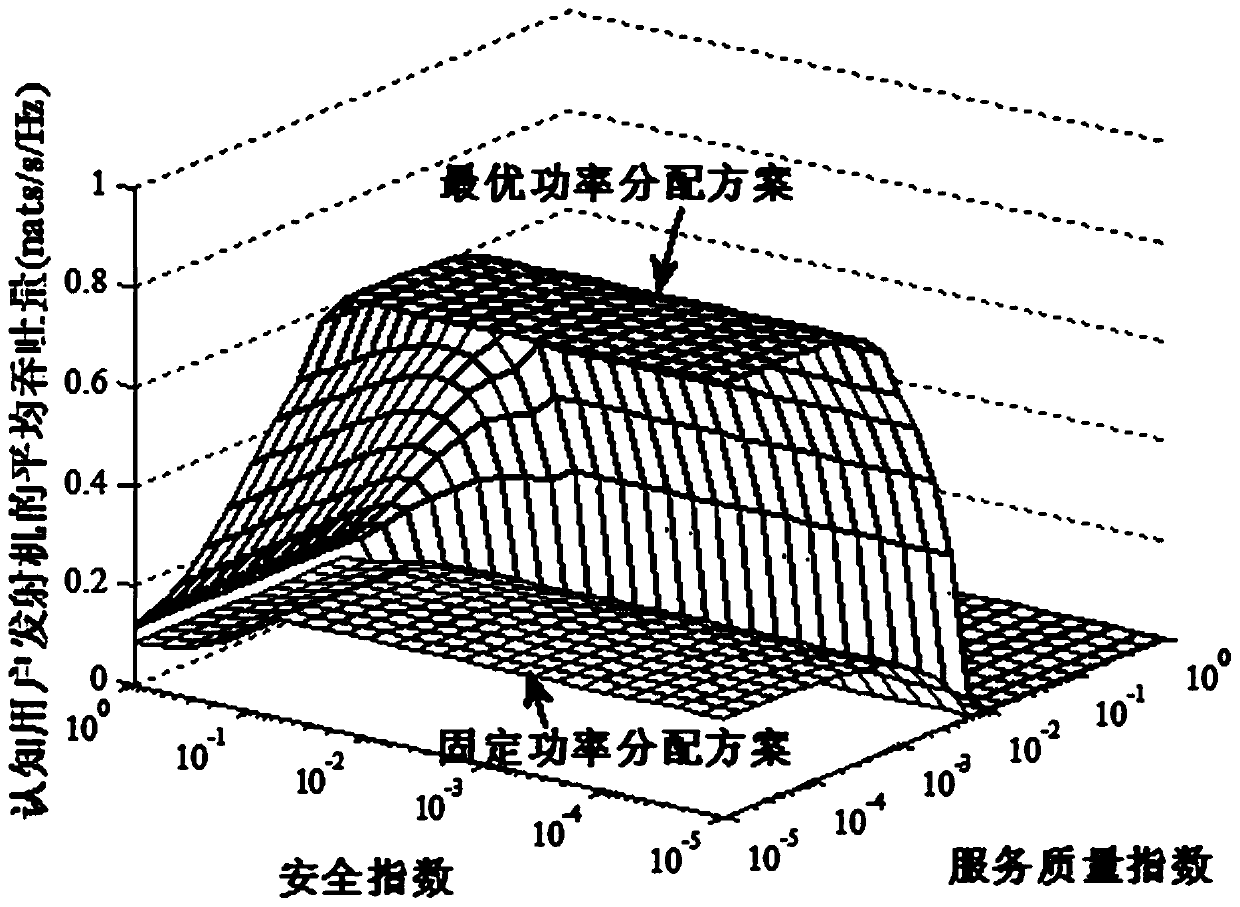
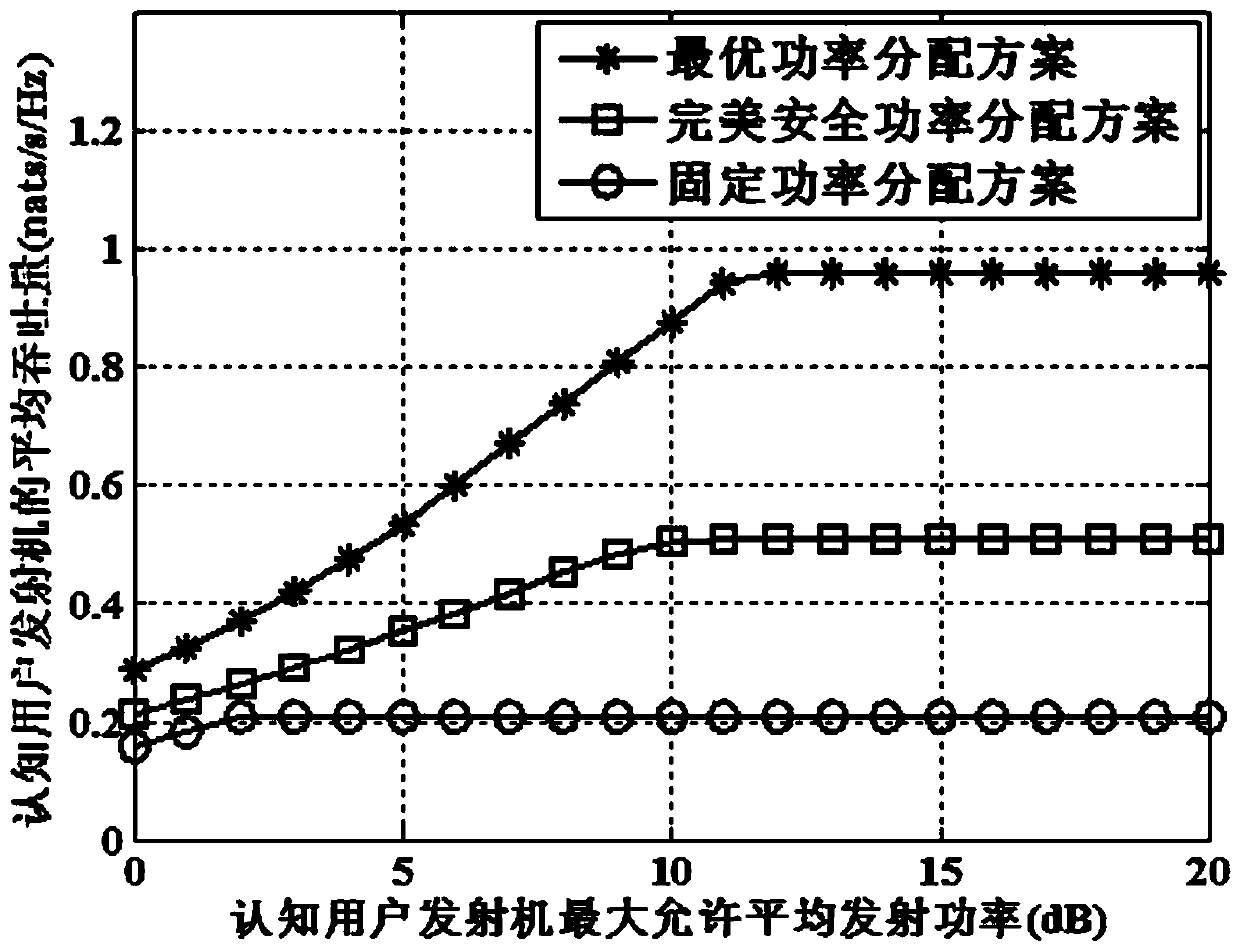
[0128] The security transmission method based on the statistical QoS guarantee in the cognitive wireless network of the present invention uses the statistical delay QoS guarantee framework to guarantee the statistical delay QoS of the PU. The framework is described by PS's queue delay threshold violation probability. Different from the currently widely used QoS protection methods, the adopted framework can quantitatively and accurately describe the fine-grained delay requirements of the primary user transmitter through a single parameter called PS delay QoS index. Secondly, the framework of security transmission guarantee is used to guarantee the statistical security of cognitive users. The framework can control the reliability and security functions separately for delay-sensitive systems to meet the constraints of various security requirements. Based on th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com