Dynamic defense method of industrial control network with endogenous security
An industrial control network and dynamic defense technology, which is applied in the direction of program control, general control system, control/regulation system, etc., can solve the problems of data legality, insufficient integrity verification, lack of change, and defense effect to be improved, etc., to achieve improved The effect of security defense performance, avoiding security risks, and easy promotion and implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] The present invention will be further described in detail below in conjunction with the accompanying drawings, so that those skilled in the art can implement it with reference to the description.
[0058] It should be understood that terms such as "having", "comprising" and "including" as used herein do not entail the presence or addition of one or more other elements or combinations thereof.
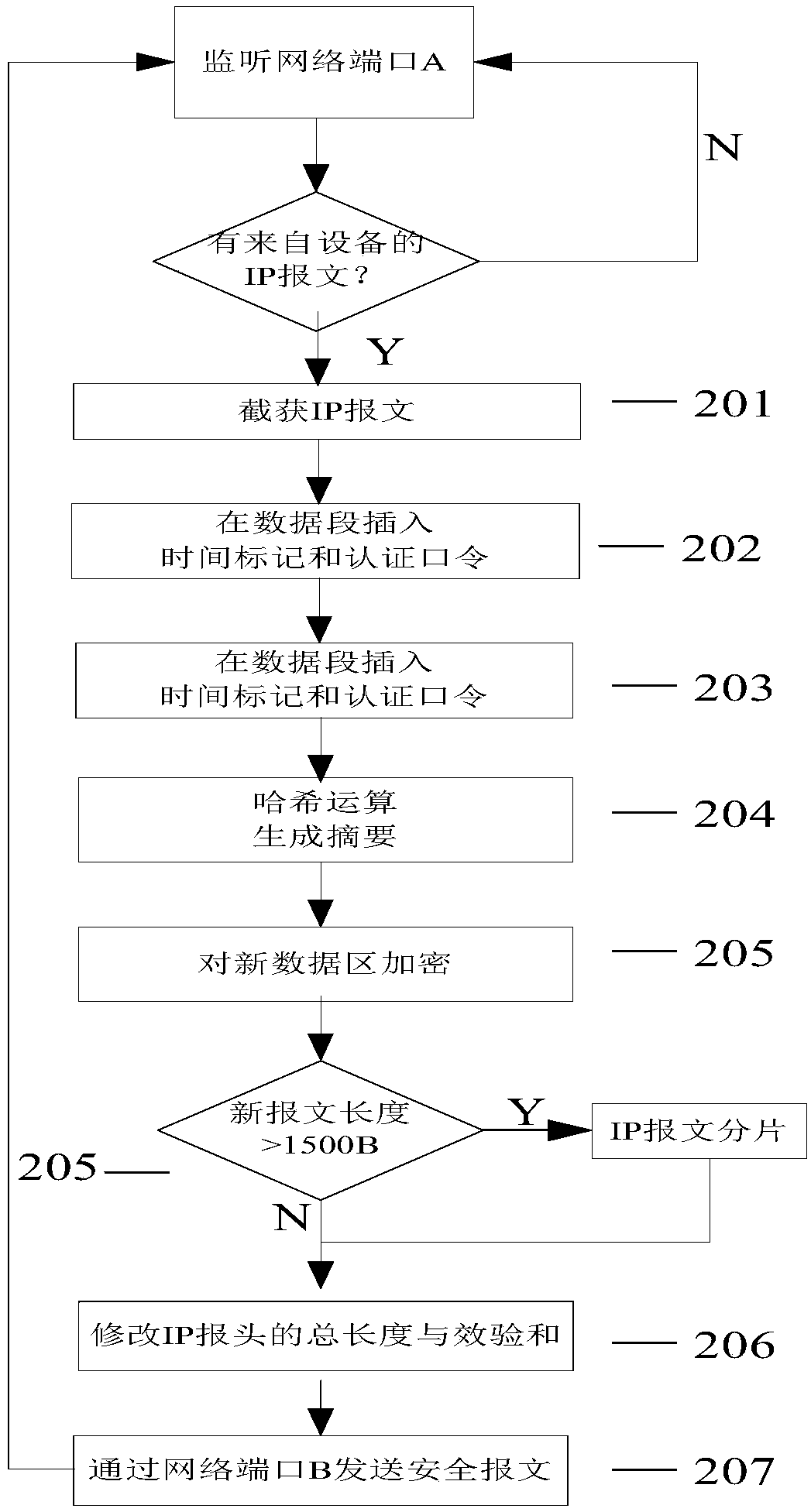
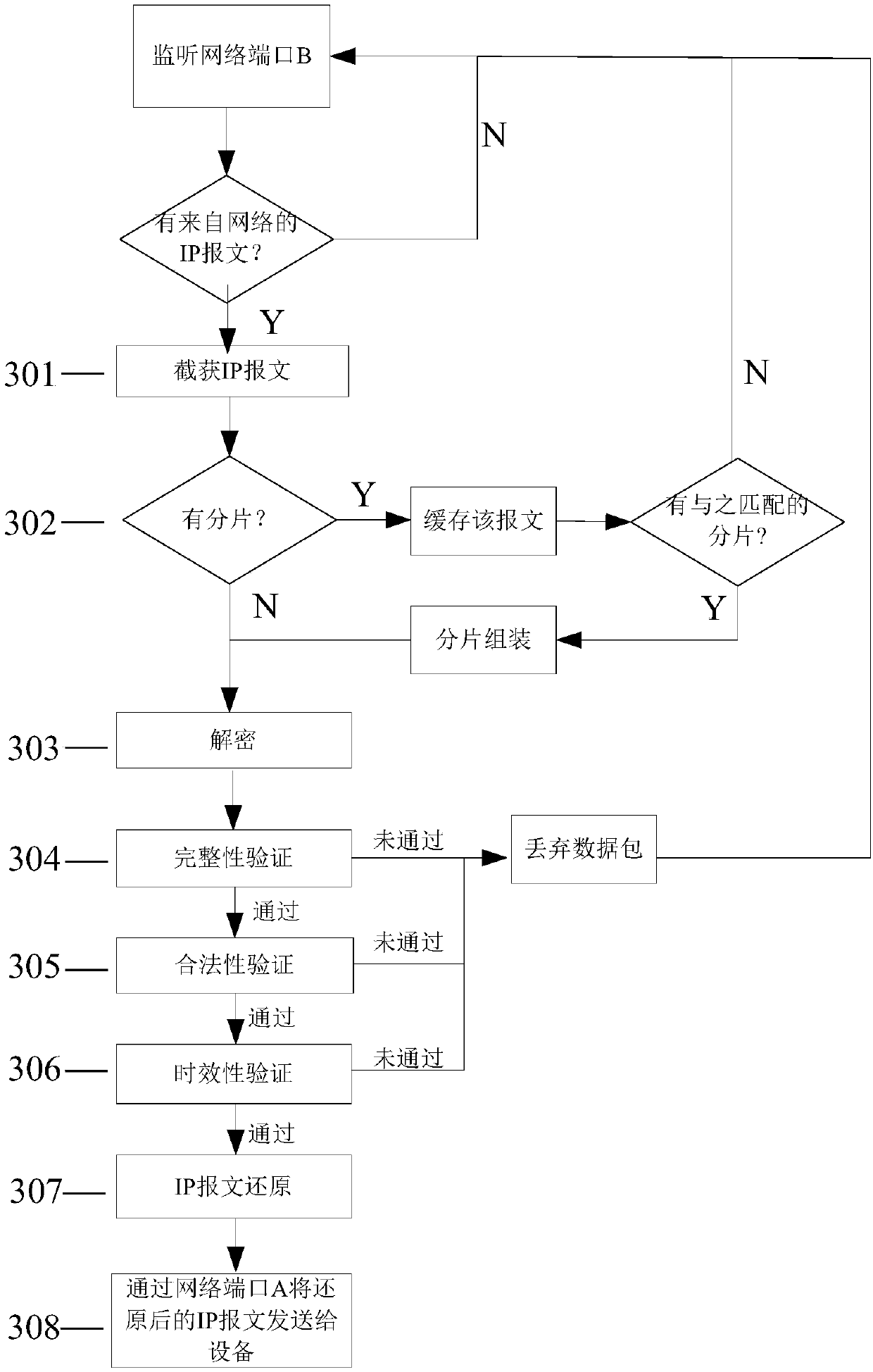
[0059] According to the implementation form of an endogenously secure industrial control network dynamic defense method of the present invention, the present invention will be further described in conjunction with the following six examples.
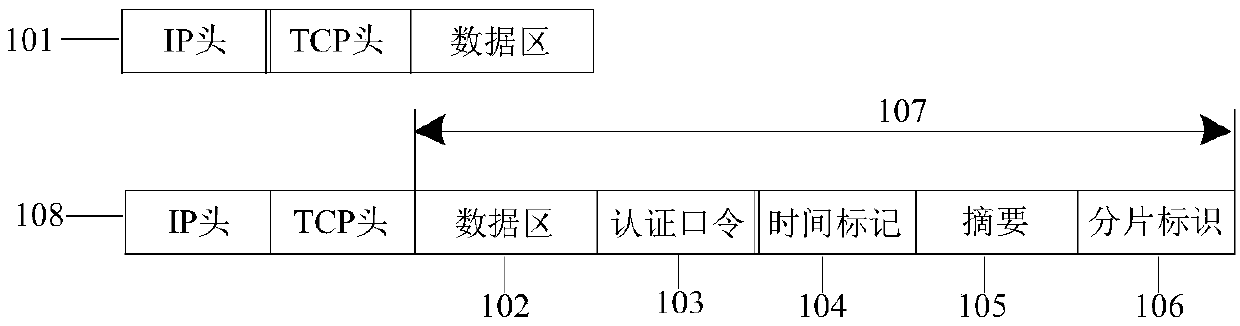
[0060] In Example 1, combined with figure 1 The security message format is given. Specifically, the security message is defined on the basis of the TCP / IP message 101, and the "authentication password" 103, "time stamp" 104, "time stamp" 104, " Additional information such as "summary" 105 and "fragment identification" 106 forms a new data...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com