Card reader for access control system and working method thereof
A technology of access control system and working method, which is applied in the direction of reading instruments, time registers, memory record carriers, etc., can solve the problems of not having the function of preventing IC card copying, obtaining card number capacity limitations, and burning equipment, etc., to achieve a long-term solution The problem of unstable power supply from a distance, the improvement of the voltage input range, and the effect of eliminating the behavior of cloning tags
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
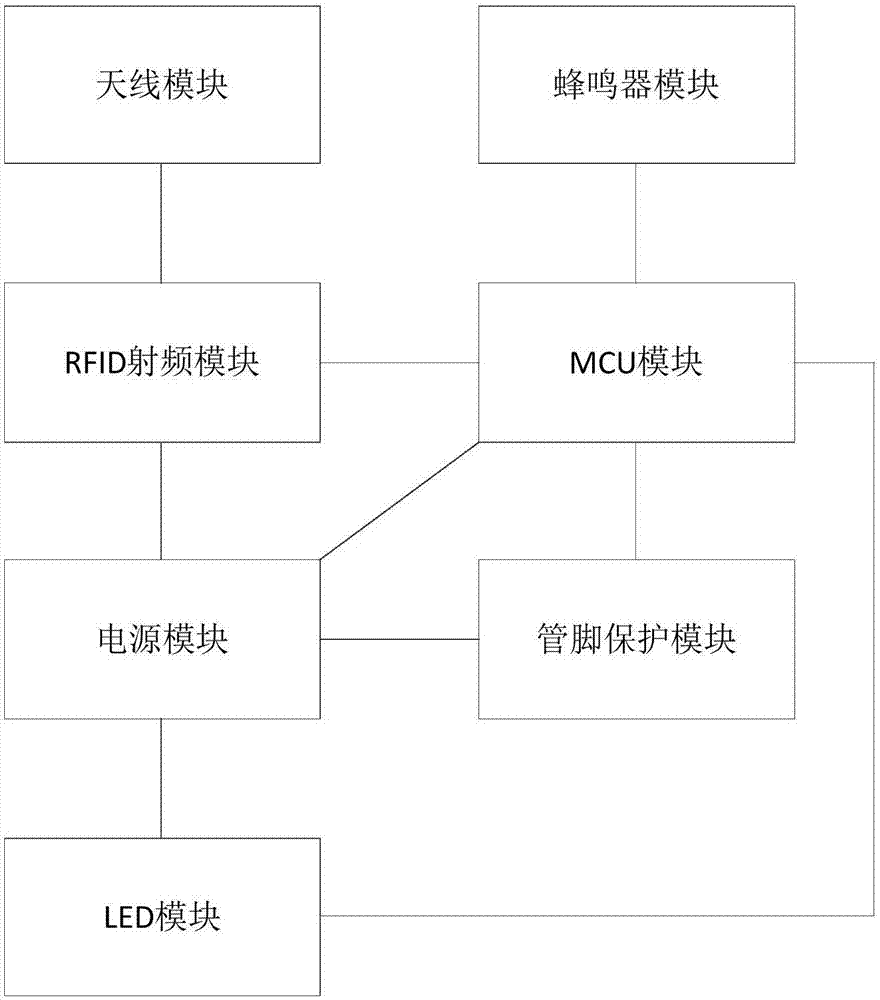
[0033] This embodiment discloses a card reader for an access control system, the block diagram of which is attached figure 1 As shown, it specifically includes: MCU module, RFID radio frequency module, buzzer module, pin protection module, LED module, power supply module, antenna module, wherein, the MCU module and the RFID radio frequency module, the buzzer The device module, the pin protection module and the LED module are connected, and the instructions issued by the RFID radio frequency module, the buzzer module, the pin protection module and the LED module are managed, and at the same time, receiving The feedback information of the power supply module, the RFID radio frequency module and the pin protection module.
[0034] The power supply module supplies power to the connected MCU module, the RFID radio frequency module, the buzzer module and the LED module respectively.
[0035] The buzzer module is used for prompting and alarming when the card reader swipes a card.
...
Embodiment 2
[0045] This embodiment discloses a working method of a card reader in an access control system, the flow chart of which is shown in the attached figure 2 As shown, it specifically includes the following steps:
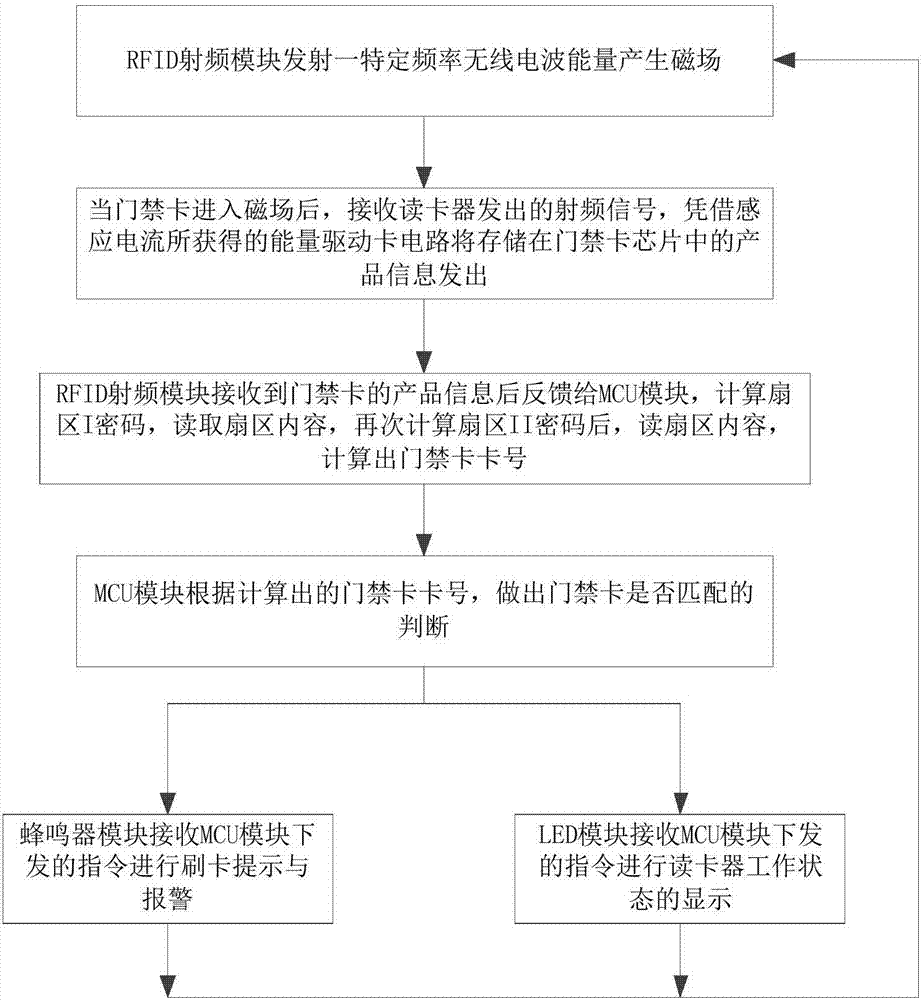
[0046] The RFID radio frequency module emits a specific frequency radio wave energy to generate a magnetic field;
[0047] When the access control card enters the magnetic field, it receives the radio frequency signal sent by the card reader, and the energy obtained by the induced current drives the card circuit to send out the product information stored in the access control card chip;
[0048] After receiving the product information of the access control card, the RFID radio frequency module feeds back to the MCU module, calculates the password of sector I, reads the content of the sector, calculates the password of sector II again, reads the content of the sector, and calculates the card number of the access control card;
[0049]The MCU module judges whether the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com