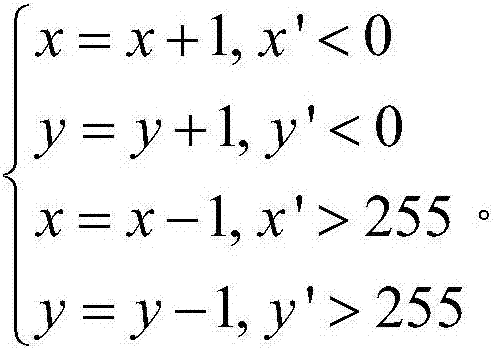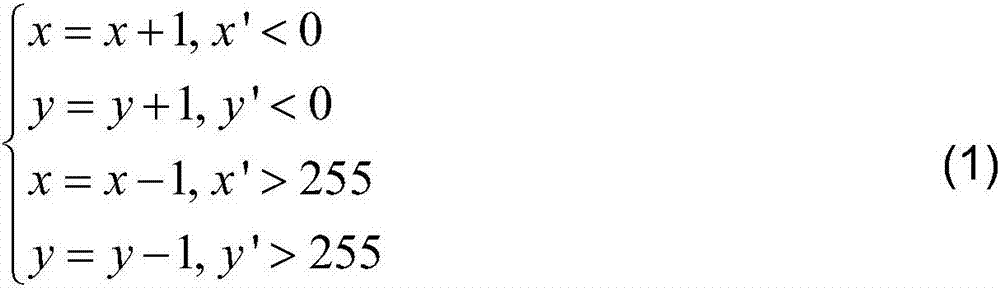Efficient information hiding method of introducing auxiliary pixels
An auxiliary pixel and information hiding technology, applied in the field of communication, can solve the problem that the maximum embedded capacity cannot be increased, and achieve the effect of increasing difficulty, improving efficiency and increasing security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] While high-speed data is being transmitted, other low-speed data or part of high-speed data is often transmitted at the same time. In addition to transmitting images, other sensor data may also be transmitted. The invention provides a method for data transmission using information hiding technology, which has the characteristics of large hidden capacity, high performance and low complexity, and is practical in spacecraft engineering, ground information carrying transmission systems, and various image transmission systems. value.
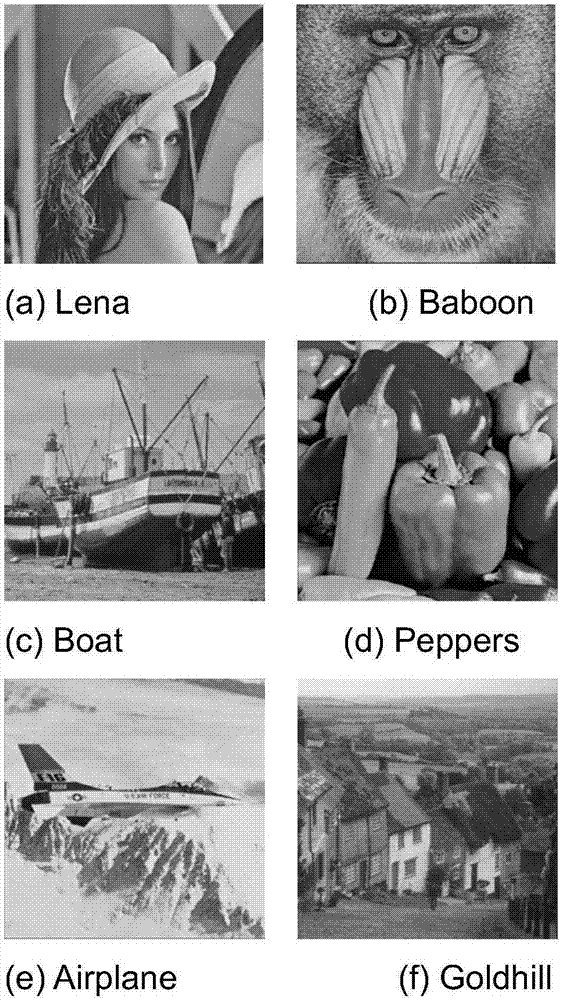
[0035] The experiment uses the MATLAB2013a platform, and the carrier data uses six standard grayscale images of 512×512, such as figure 1 As shown, the secret information is generated by a pseudo-random number generator. If the algorithm needs to have higher security, the carrier can be preprocessed with chaotic sequences or some encryption algorithms.
[0036] The present invention introduces an efficient information hiding method of auxil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com