A Fault-Tolerant Method for Checkpoint-Based Computers
A checkpoint and computer technology, applied in the computer field, can solve the problems of inability to meet the I/O bandwidth requirements of fast rewinding parallel file systems, snatch computing resources and memory resources, and fail to use them effectively, so as to reduce I/O access. and bandwidth requirements, speeding up the rollback, and improving the effect of resource utilization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] In order to make the objectives, technical solutions, design methods and advantages of the present invention clearer, the present invention will be further described in detail below through specific embodiments in conjunction with the accompanying drawings. It should be understood that the specific embodiments described herein are only used to explain the present invention, but not to limit the present invention.
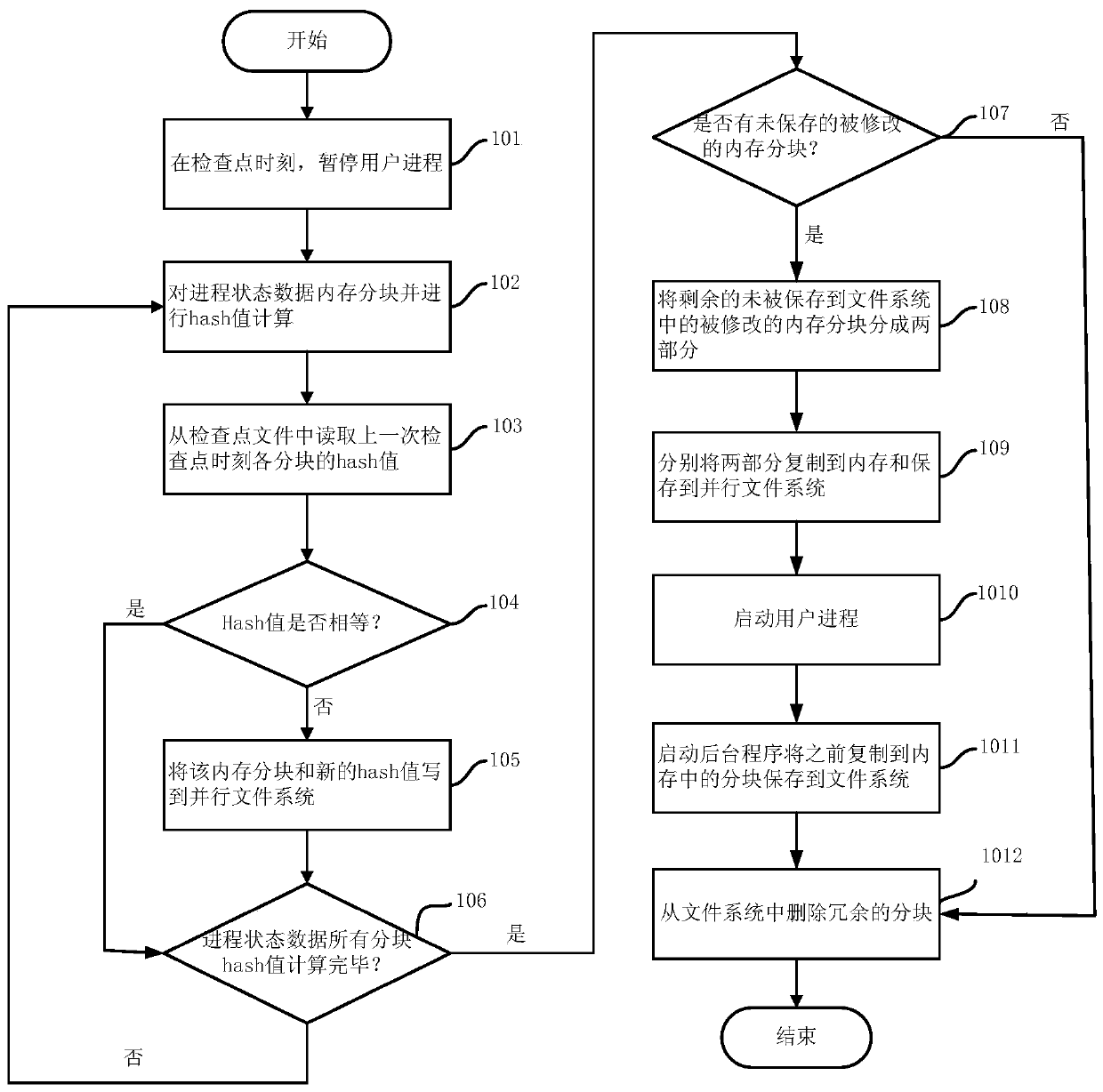
[0027] figure 1 A flow chart of performing a checkpoint according to one embodiment of the present invention is shown. In short, the checkpoint mechanism refers to setting a checkpoint at an appropriate time when the process is running normally, saving the process state data (or checkpoint file) to the stable storage, and if a failure occurs during the subsequent running process, the process state data is saved. Read from memory to perform rewind / restore operations of the process. Specific steps are as follows:
[0028] Step 101: At the checkpoint moment, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com