Method and device for detecting horizontal permission vulnerabilities
A detection method and permission technology, applied in the computer field, can solve problems such as low execution efficiency, reduce the false detection rate and false negative rate, improve the detection performance, and ensure the efficiency of vulnerability detection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
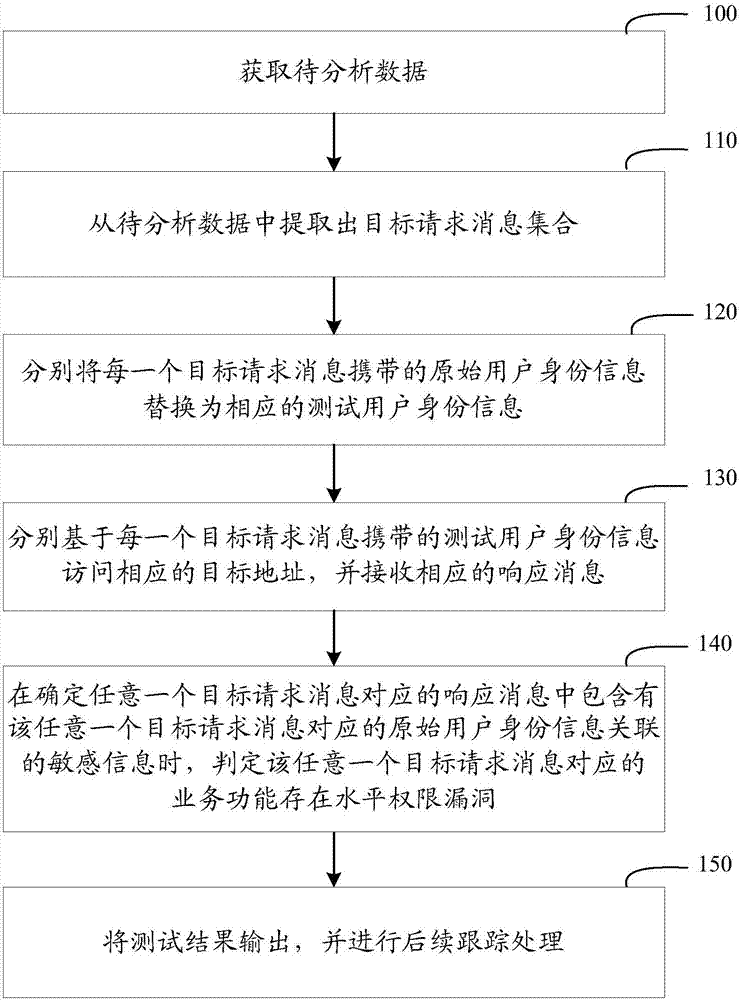
[0049] In order to improve the detection accuracy of horizontal authority loopholes and improve detection efficiency, in the embodiment of the present application, a new detection method for horizontal authority loopholes is designed. The specified parameters in the scanned uniform resource locator (Uniform Resource Locator, URL) are replaced by preset rules, and whether there is a horizontal authority vulnerability is judged according to the returned result.
[0050] Preferred embodiments of the present application will be described in further detail below in conjunction with the accompanying drawings.
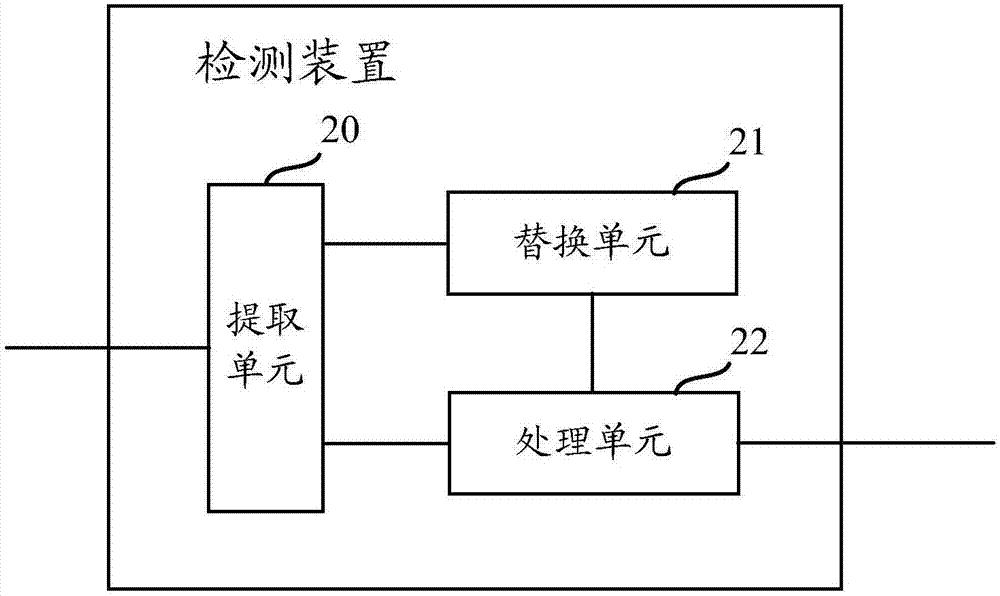
[0051] In the embodiment of the present application, the detection device used to detect the level authority vulnerability can be a centralized server specially used for testing, or a server cluster built with a distributed architecture, as long as it can realize the technology of the embodiment of the present application All the devices in the scheme can be adopted. In the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com