Graph theoretical method for quickly and accurately detecting zero-day malicious software
A malware and graph theory technology applied in the computer field to achieve low overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
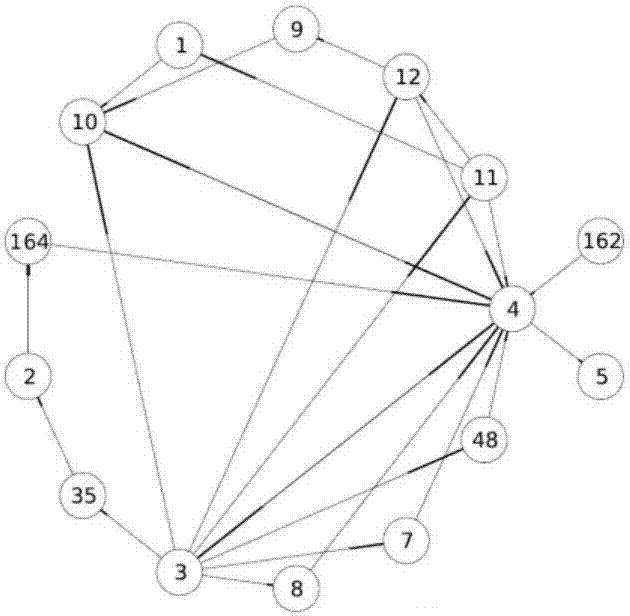
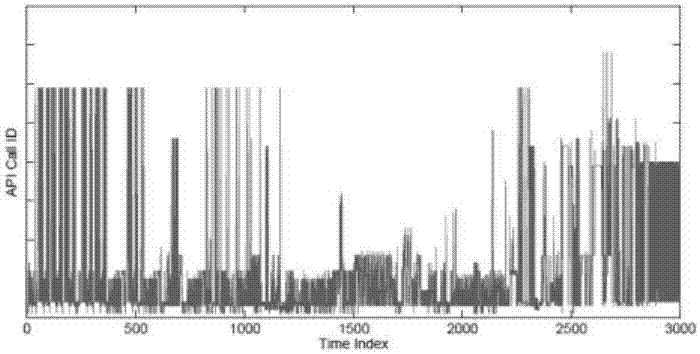
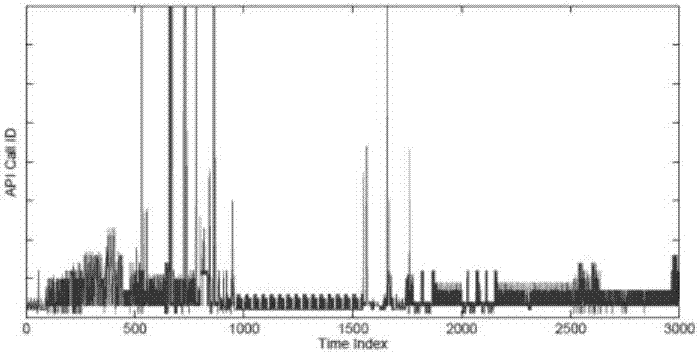
[0023] This embodiment uses a behavioral graph called an API (or system call in Linux terminology) call graph [5]. Given a sequence of API calls for a program, a unique API call is represented by a fixed point, vertex v 1 and v 2 An edge exists between if and only if the sequence of API calls includes a subsequence of API calls and between. Our key understanding is that the API call graphs of benign and malware have different graph-theoretic properties, and this property can be exploited to distinguish benign from malware. To illustrate this understanding, Figures 1-4 show the time-series and radial layouts of API call graphs for benign and malware, respectively. We visually observe interesting patterns of benign and malware in time-series and radial layouts. exist figure 1 and figure 2 In the time series of both benign and mal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com