Dynamic risk access control method of cloud platform
A dynamic risk and access control technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as poor scalability, inability to dynamically match rules, fixed risk assessment index weights, and inability to adapt ABAC strategies to cloud environments.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
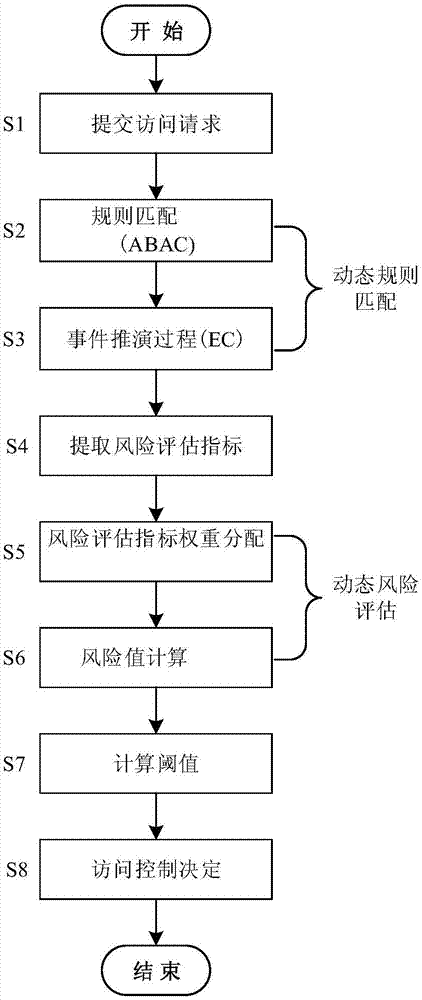
[0047] The cloud platform dynamic risk access control method provided by the present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0048] Such as figure 1 As shown, the cloud platform dynamic risk access control method provided by the present invention includes the following steps carried out in order:
[0049] Step 1) Submit access request phase: the user submits the current access request req i (i=1,2,...), the current access request req i Contains four attributes: subject, object, access activity and access context;
[0050] Step 2) Rule matching strategy stage: use attribute based access control (ABAC) strategy to formulate the corresponding rule base, and match the rules in the rule base with the above-mentioned current access request req one by one i Match, if the match is successful, record the rule that matches successfully as the current rule rule j (j=1,2,...); if the match is unsuccessful, t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com