Clustering algorithm based financial terminal security protection method and system
A clustering algorithm and financial terminal technology, applied in the electronic field, can solve problems such as reducing efficiency and user experience, and achieve the effect of improving security performance, diversified operation experience, and friendly operation experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
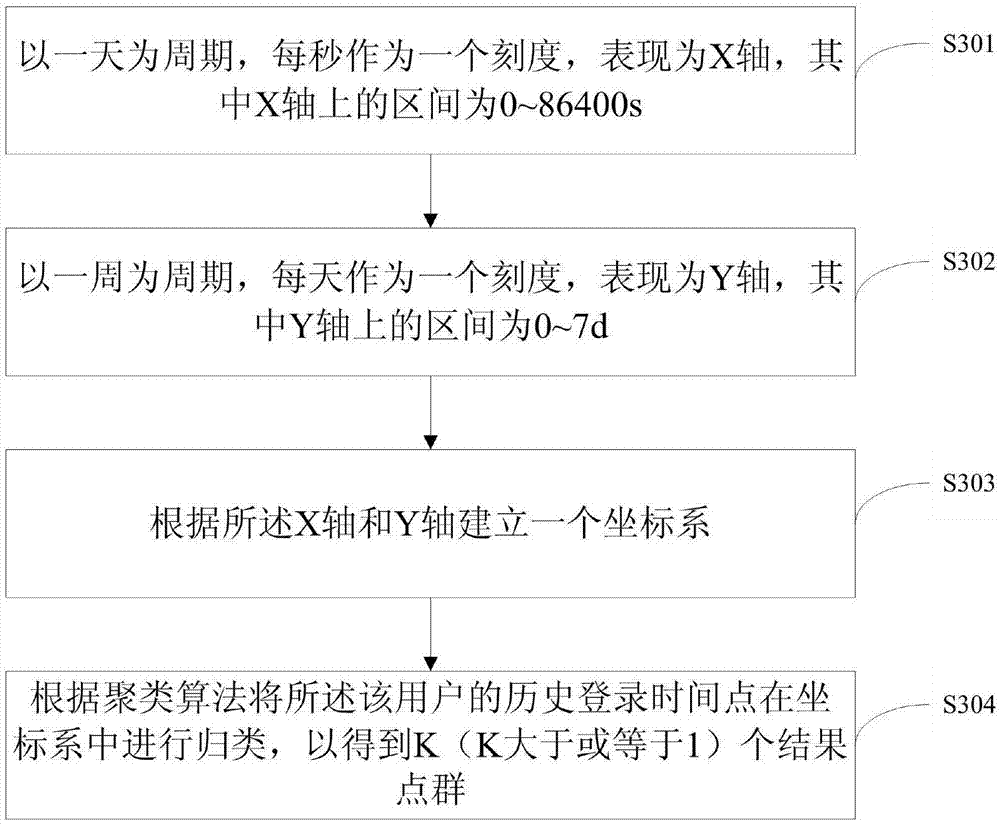
[0045] Below in conjunction with accompanying drawing and specific embodiment, the present invention will be further described:
[0046] See figure 1 , the embodiment of the present invention relates to a financial terminal security protection method based on a clustering algorithm, and its preferred implementation method includes:
[0047] Step S101 , when the number of login operations performed by the user using the financial terminal reaches a preset value, the historical feature data of the user is acquired.
[0048] Among them, in order to obtain enough sample data, it is required that the number of successful login operations by the user using the financial terminal reaches a preset value. Here, the user's historical feature data is sample data, that is, the user's behavioral operation feature data at each login, such as historical login time points, historical login locations, or historical login devices.
[0049] Step S102 , according to the number of login operatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com