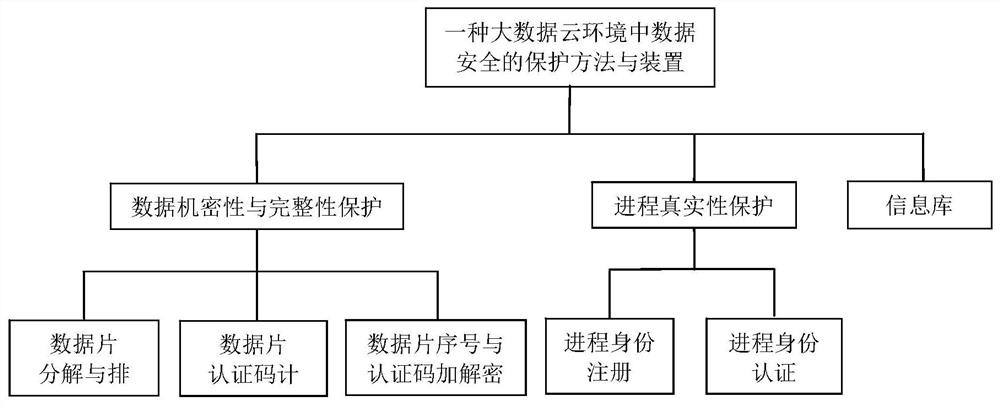
A data security protection method and device in a big data cloud environment
A data security and big data technology, applied in the field of network security, can solve problems such as data error correction, and achieve the effect of ensuring confidentiality and integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
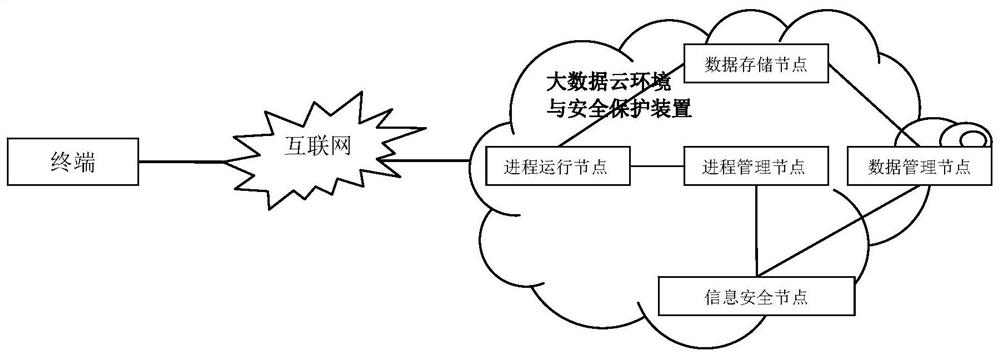
[0078] see figure 1 and 2 A method for protecting data security in a big data cloud environment provided by the present invention, comprising the following steps:
[0079] A. The process in the process running node safely writes the big data in the data storage node;
[0080] B. The process in the process running node safely reads the big data in the data storage node;
[0081] C. Process security creation and migration in a process running node to another process running node;
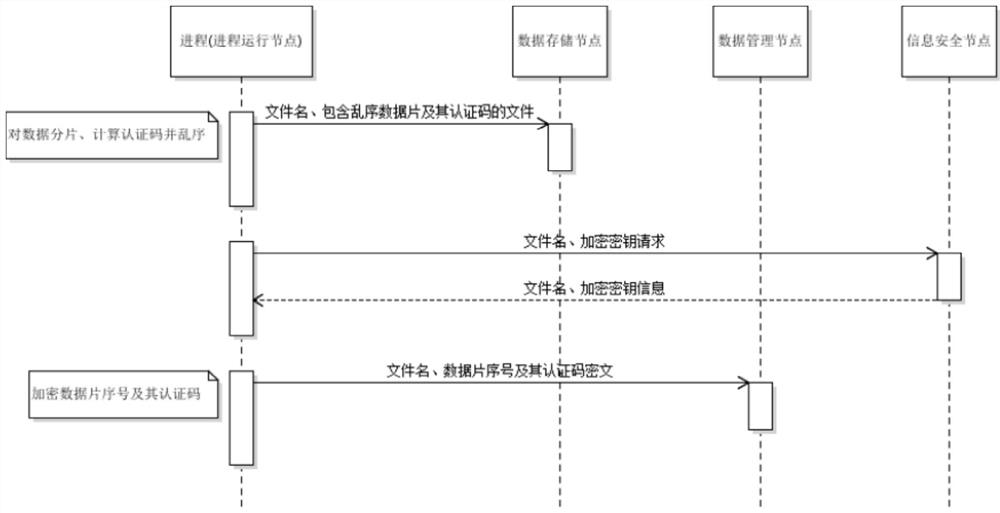
[0082] Such as image 3 As shown, the step A includes:
[0083] A1. The process in the process running node is to store data slices, calculate the authentication code of the data slices, and perform out-of-order processing;
[0084] A2. The process in the process running node sends the processed file containing the out-of-sequence data slice and its authentication code to the data storage node;
[0085] A3. The process in the process running node applies for an encryption key to the information ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap