Android application program protection method based on dual ARM instruction virtualization
An application and instruction technology, applied in the field of Android application protection based on dual ARM instruction virtualization, can solve problems such as affecting program performance, weak operability, and no application, achieving strong scalability, high flexibility, and increased attack costs. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
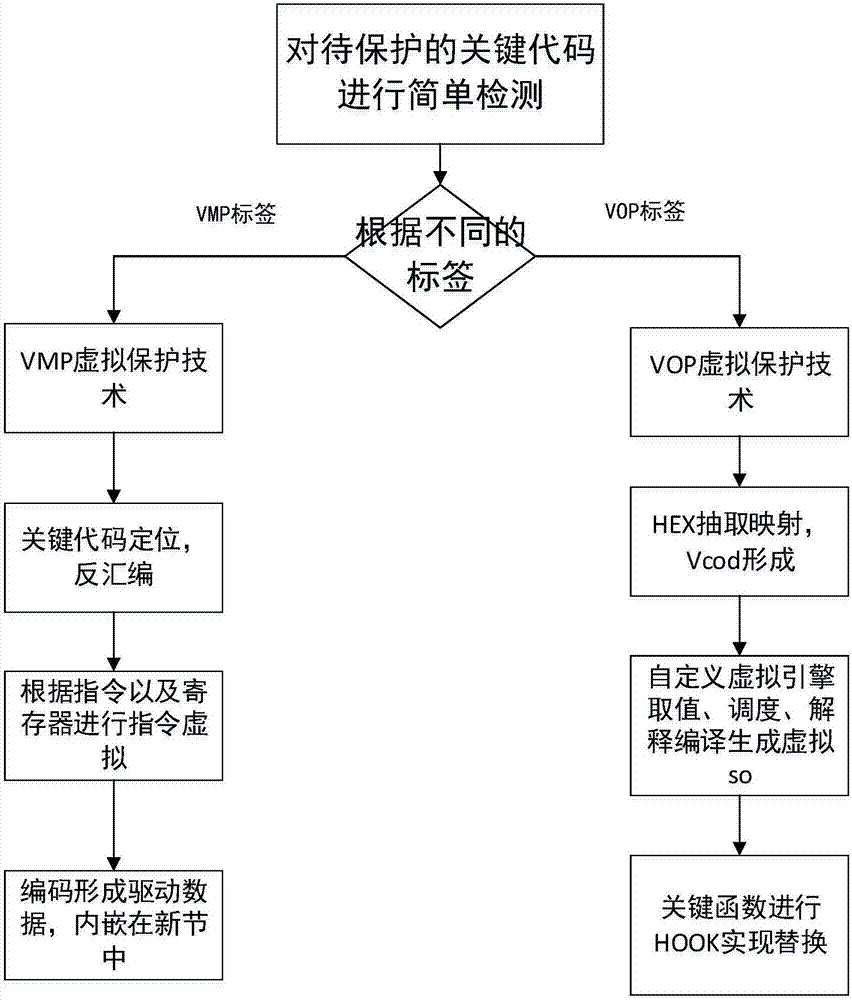
[0029] The present embodiment proposes a virtual Android application program protection method based on dual ARM instructions, comprising the following steps:
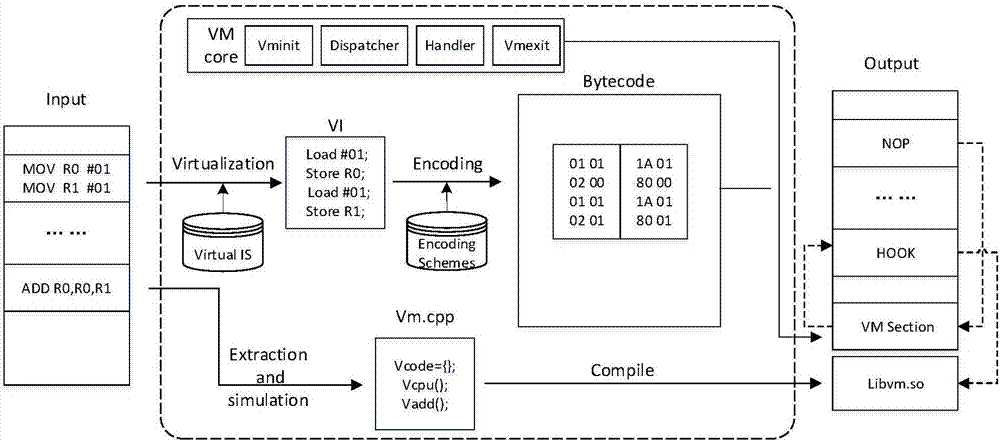
[0030] Step 1, input the Android local layer dynamic link library file to be protected, usually in the .so file format, called the so file; find the key code segment that needs to be protected in the so file, and the key code segment that needs to be protected includes the need to Critical code segments protected by VOP and critical code segments requiring VMP protection;
[0031] Step 2, perform Hex extraction and virtual mapping on the key code segment that needs VOP protection to form a VOP virtual machine so file; encrypt the key code segment that needs VOP protection, and then use the Cydia Substrate framework to encrypt the encrypted code segment that needs VOP protection The key code segment is replaced by Hook so that the virtual instruction code in the VOP virtual machine so file replaces the encrypted code in t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com