A hierarchical multi-domain visual security operation and maintenance method based on graph database
A database and domain security technology, applied in the field of security operation and maintenance, to improve agility, reduce development costs and modeling time, and improve query and analysis efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
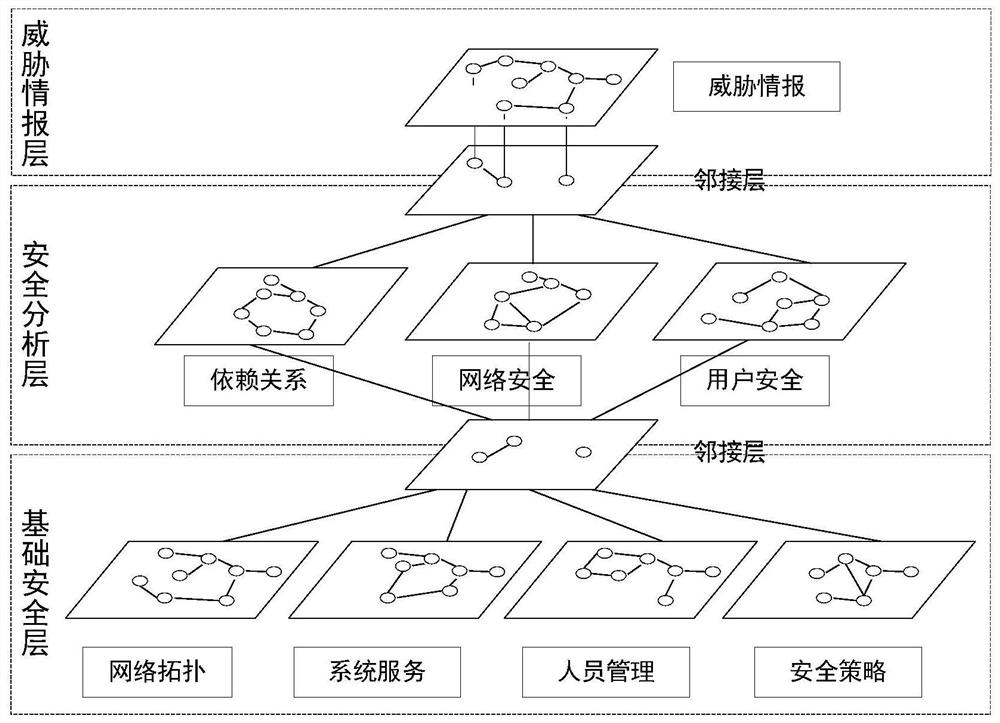
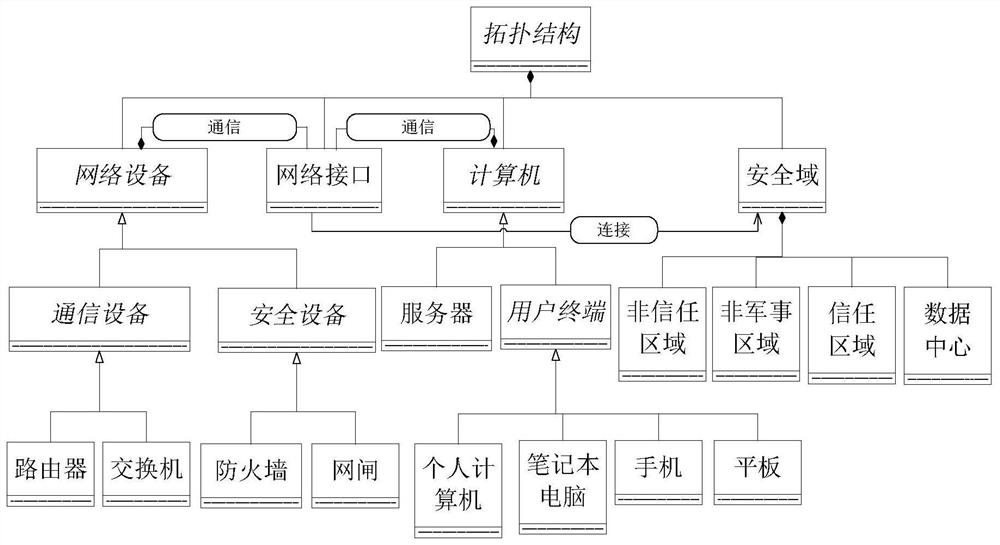
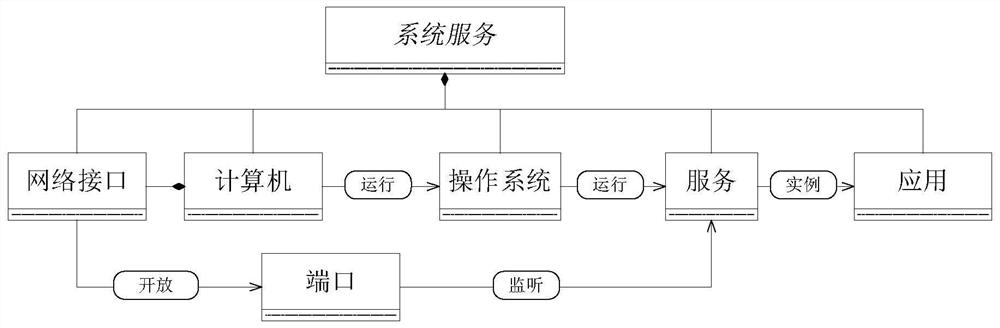
[0035] The invention divides security operation and maintenance into basic security layer, security analysis layer and threat intelligence layer, and at the same time divides the functions of each layer into single or multiple domains, wherein the basic security layer is divided into topology domain, system service domain, and personnel information domain And the security policy domain, the security analysis layer is divided into the dependency domain, the network security domain and the user security domain, and the threat intelligence layer is composed of the corresponding threat intelligence standard domain. The method converts the structural relationship and attribute characteristics of each domain into corresponding UML diagrams, and at the same time deploys sensors with corresponding functions at designated network locations to collect the data required by each domain, and completes the UML diagram-to-graph database through the corresponding API Mapping to realize visuali...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com