A bypass blocking method, device, system, and electronic device
A blocking device and device technology, applied in the network field, can solve the problems of reduced blocking success rate, increase in maintenance cost and equipment cost, long transmission distance of firewall equipment, etc., to improve the blocking success rate, meet the delay requirements, Optimizing the effect of the transmission path
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
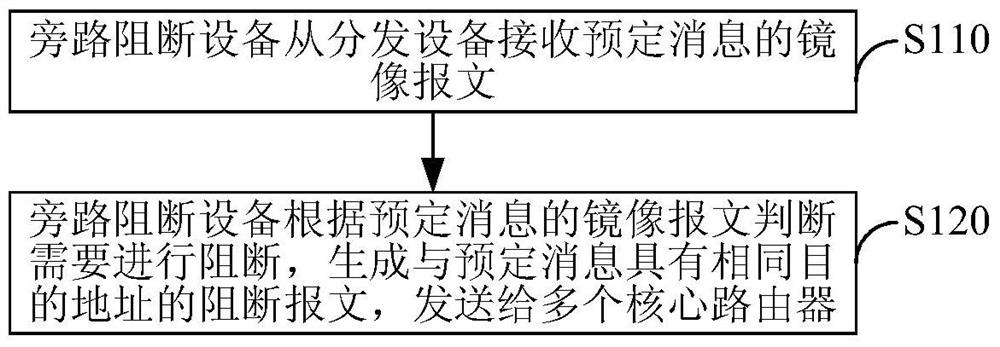
[0068] Embodiment 1. A bypass blocking method, such as image 3 As shown, including steps S110-S120:
[0069] S110. The bypass blocking device receives a mirror message of a predetermined message from the distribution device; wherein the distribution device is a device for distributing downlink data of an Internet service provider (ISP) network;
[0070] S120. The bypass blocking device judges that blocking needs to be performed according to the mirror message of the predetermined message, generates a blocking message having the same destination address as the predetermined message, and sends it to multiple core routers.
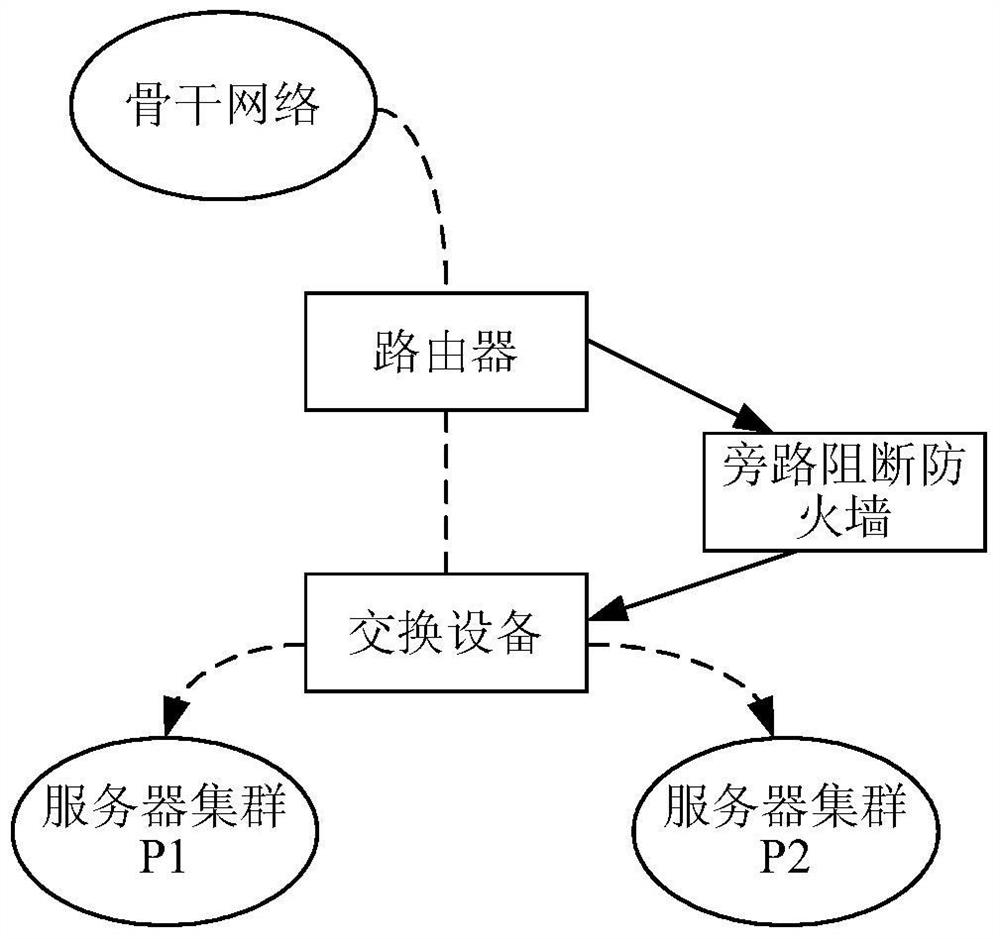
[0071] In this embodiment, the bypass blocking device directly receives the mirrored message from the distribution device, which is equivalent to moving the bypass blocking device from the position close to the server in the IDC room to the entrance position of the public network (that is, the ISP network) (or It is called the access entrance position), tha...
Embodiment 2
[0107] Embodiment 2. A bypass blocking device, such as Figure 9 shown, including:
[0108] The receiving module 91 is configured to receive a mirror message of a predetermined message from a distribution device; wherein the distribution device is a device for distributing downlink data of an Internet service provider (ISP) network;
[0109] The blocking module 92 is configured to generate a blocking message with the same destination address as the predetermined message and send it to multiple core routers when judging that blocking is required according to the mirror message of the predetermined message.
[0110] In this embodiment, the receiving module 91 is a part of the device responsible for receiving mirrored messages, which may be software, hardware or a combination of both.
[0111] In this embodiment, the generation module 92 is a part in the device responsible for generating and sending the blocking message, which may be software, hardware or a combination of both. ...
Embodiment 3
[0121] Embodiment 3. A network system, comprising:
[0122] Distribution equipment, used to distribute the downlink data of the ISP network of the Internet service provider;
[0123] Multiple core routers for forwarding received downlink data;
[0124] Bypass blocking device;
[0125] The bypass blocking device is used to receive the mirrored message of the predetermined message from the distribution device; when it is judged that blocking needs to be performed according to the mirrored message of the predetermined message, generate a reset with the same destination address as the predetermined message The message is sent to the multiple core routers.
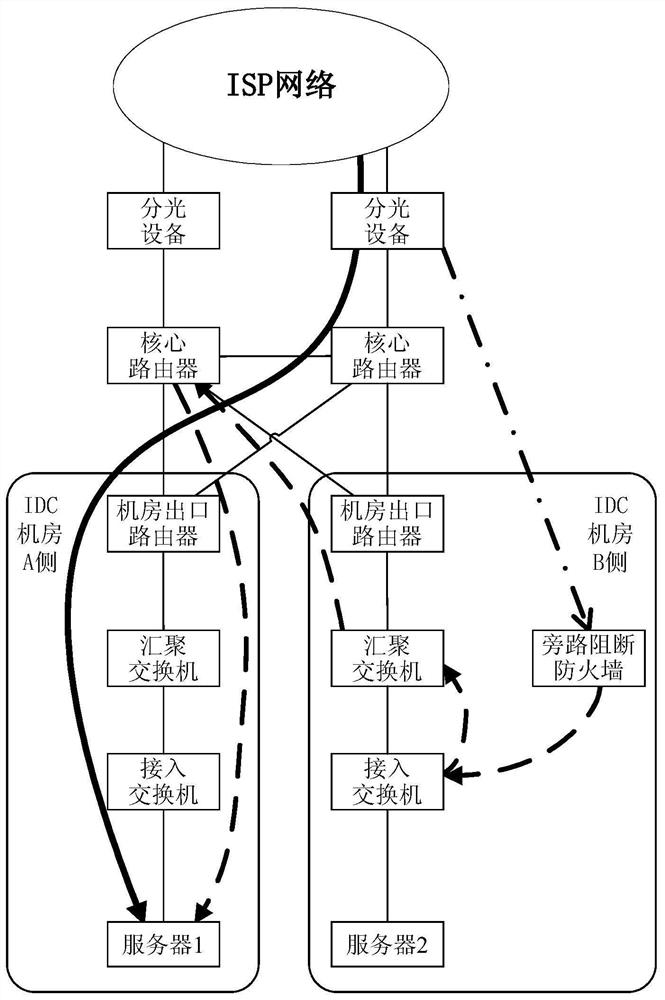
[0126] The network system in this embodiment can be regarded as, but not limited to, a cloud service data center; or in other words, it can be regarded as including Figure 5-8 In addition to the ISP network part of the system.
[0127] In this embodiment, the bypass blocking device can be regarded as the bypass blocking de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com