Identity authentication method and system based on digital signature of token
A digital signature and identity authentication technology, applied in the field of Internet security, can solve problems such as performance degradation, session ineffectiveness, memory space consumption, etc., and achieve the effects of improving efficiency and security, simple structure, and wide application prospects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
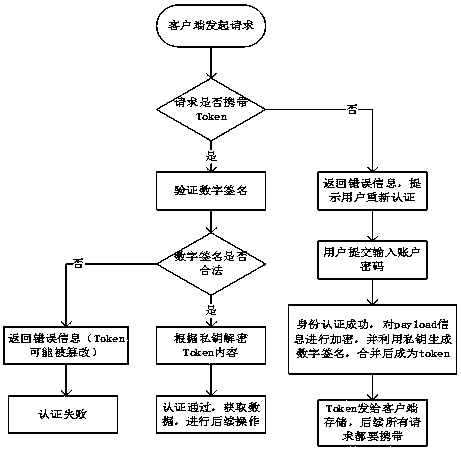
[0063] Embodiment 2 provides a token-based digital signature authentication system, including
[0064] The client input module is used for the client to initiate a request;
[0065] The server-side detection module is used to detect whether the request information input by the input module carries a token;
[0066] When the server-side detection module detects that the received request information does not carry a token, the return module is used to return an error message and prompt the user to re-authenticate;
[0067] The verification module is used to verify the digital signature;
[0068] The server decryption module is used to decrypt the token content;
[0069] The verification module is used to verify the legitimacy of the token content.
[0070] The system also includes a confirmation module and an encryption module;
[0071] The confirmation module is used to determine the original information data for generating the token;
[0072] The encryption module is used...
Embodiment 3
[0077] Embodiment 3, when the customer logs in for the first time, he needs to provide a user name and password for the first identity verification. After the server receives the user name and password information, it detects, and if the authentication passes, it prepares to generate a Token; after the user passes the first authentication, it needs to determine the original information data used to generate the token, which is called payload, which can be regarded as a key-value The object can save some non-critical basic information such as user name and email address. After building the payload data, choose an encryption method and determine a unique private key to encrypt the payload. The encrypted data is called Token, and then use the private key to sign the Token. Finally, the combination of token and signature All the data is sent to the client, and the client can choose multiple ways to cache this data. In this way, the server does not save any identity information an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com