Large-scale website vulnerability scanning method and device and electronic equipment
A website vulnerability and vulnerability scanning technology, applied in the field of information security, can solve problems such as troublesome engine cluster expansion, waste of resources, and heavy workload of manual operation and maintenance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
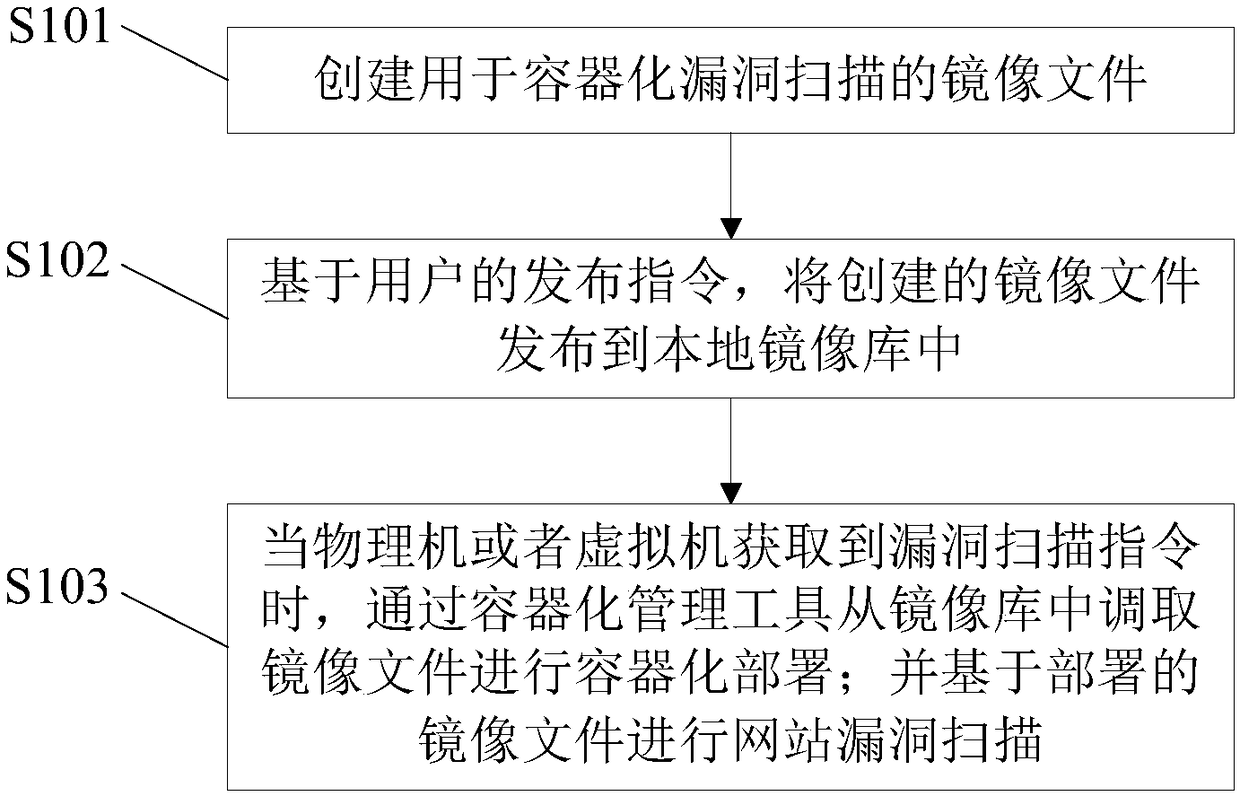
[0052] The embodiment of the present invention provides a large-scale website vulnerability scanning method, which is applied to physical machines or virtual machines, see figure 1 As shown, the large-scale website vulnerability scanning method includes the following steps:
[0053] S101: Create an image file for containerized vulnerability scanning.
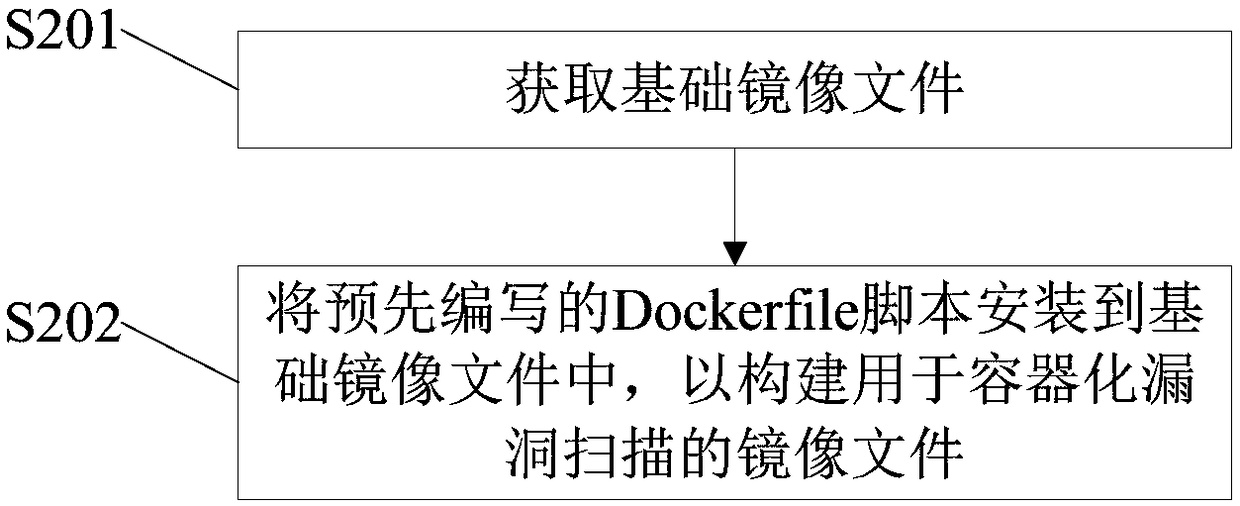
[0054] Before performing vulnerability scanning on the website, the existing vulnerability scanning engine needs to be containerized first. To realize the containerization of the vulnerability scanning engine, an image file for containerized vulnerability scanning needs to be created. The specific image file creation process includes the following steps, see figure 2 Shown:
[0055] S201: Obtain a base image file.
[0056] The above-mentioned basic image file can adopt various versions of CentOS. As a preferred implementation mode, the basic image file in this embodiment is CentOS7.2.
[0057] S202: Install the pre-written ...
Embodiment 2
[0079] An embodiment of the present invention provides a large-scale website vulnerability scanning device, which is applied to a physical machine or a virtual machine, see Figure 5 As shown, the device includes: an image creation module 51 , an image distribution module 52 , and a vulnerability scanning module 53 .
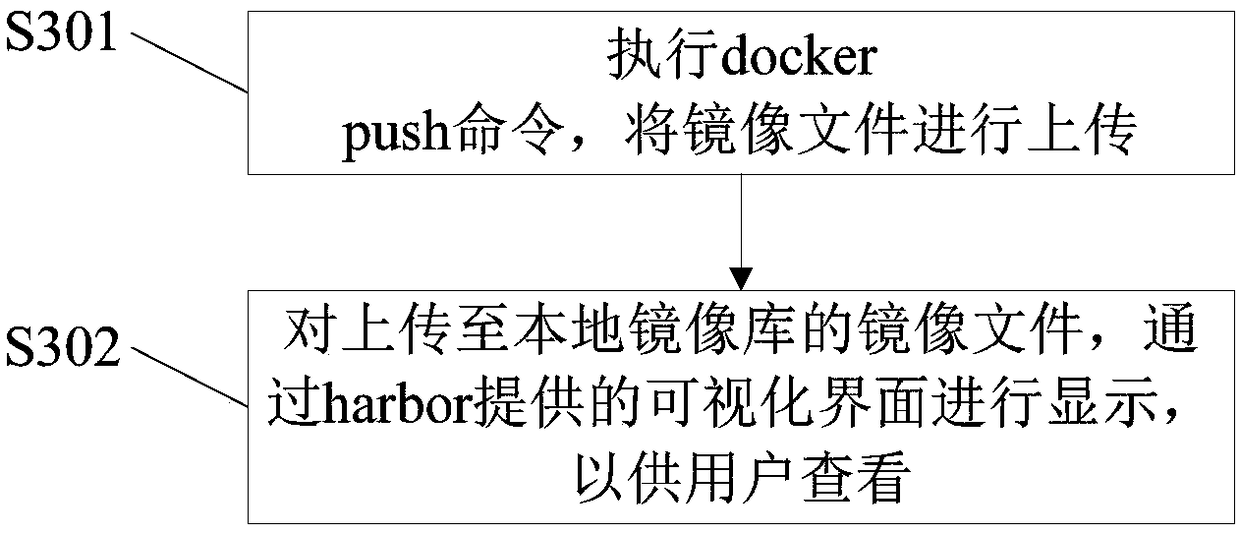
[0080] Wherein, the image creation module 51 is used to create an image file for containerized vulnerability scanning; the image release module 52 releases the created image file to the local image library based on the user's issuing instruction; the vulnerability scanning module 53 is used for When the physical machine or virtual machine obtains the vulnerability scanning instruction, the containerized management tool is used to call the image file from the image library for containerized deployment; and the website vulnerability scan is performed based on the deployed image file.
[0081] In the large-scale website vulnerability scanning device provided by the...
Embodiment 3
[0083] The embodiment of the present invention also provides an electronic device, see Figure 6 As shown, the electronic device includes: a processor 60, a memory 61, a bus 62 and a communication interface 63, and the processor 60, the communication interface 63 and the memory 61 are connected through the bus 62; the processor 60 is used to execute the data stored in the memory 61 Executable modules, such as computer programs. When the processor executes the computer program, the steps of the methods described in the method embodiments are realized.
[0084] Wherein, the memory 61 may include a high-speed random access memory (RAM, RandomAccessMemory), and may also include a non-volatile memory (non-volatile memory), such as at least one disk memory. The communication connection between the system network element and at least one other network element is realized through at least one communication interface 63 (which may be wired or wireless), and the Internet, wide area net...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com