Method and apparatus for reversible information hiding of a ciphertext image based on a urDEED algorithm
A technology of information hiding and ciphertext, which is applied in the field of reversible information hiding of ciphertext images, can solve problems such as difficulty, increased information hiding, and incomprehension, and achieve the effects of improving compatibility, ensuring safe transmission, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
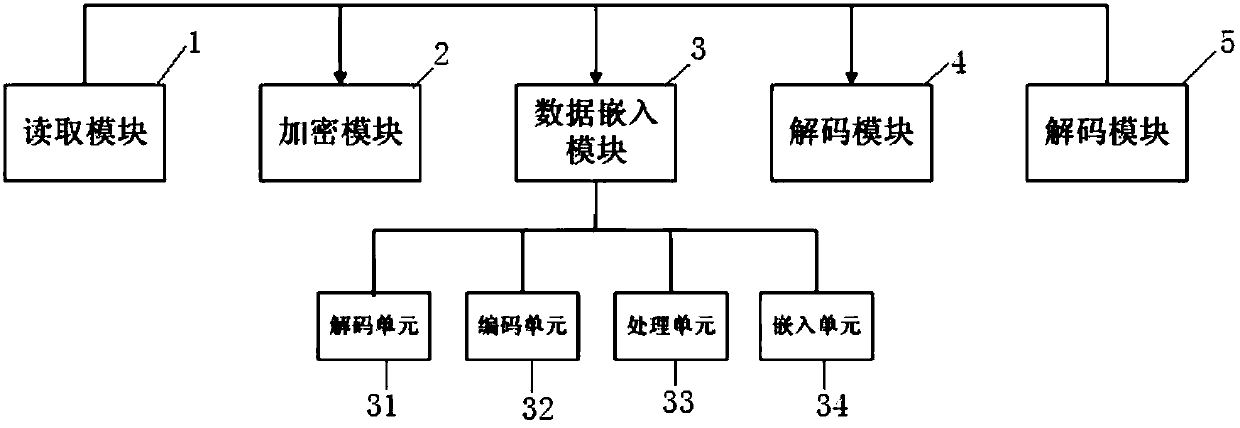
[0045] Such as figure 1 Shown is a functional block diagram of a ciphertext image reversible information hiding device based on the urDEED algorithm provided by the present invention, including a reading module 1, an encryption module 2, a data embedding module 3, a decoding module 4, and a decryption module 5.
[0046] The reading module 1 is used to read the pictures that initially need to be encrypted and hidden; the encryption module 2 is used to encrypt the pictures; the data embedding module 3 is used to embed the ciphertext; The decoding module 4 is used to extract embedded information; the decryption module 5 is used to restore the encrypted picture to its original state.
[0047] The encryption module 2 uses the AES algorithm to encrypt the picture, including: performing an AddRoundKey operation on the State, XORing the RoundKey and the State; for each round in the previous Nr-1 rounds, using S-BOX to replace the State once The operation is called SubBytes; replace t...
Embodiment 2
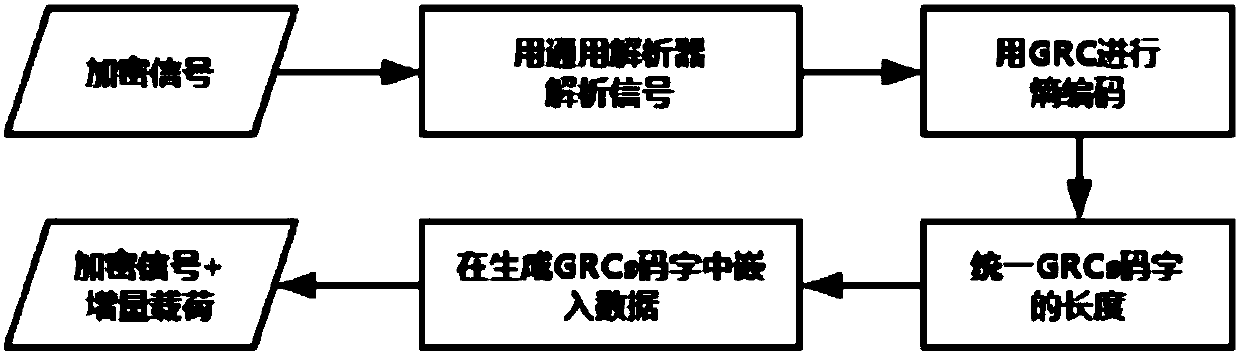
[0065] Such as image 3 As shown, it is a flow chart of a method for reversible information hiding of ciphertext images based on the urDEED algorithm of the present invention, and the method includes the following steps:
[0066] S1: Read pictures.
[0067] S2: Encrypt the picture with the AES algorithm.
[0068] S3: Use the urDEED algorithm to embed data in the ciphertext.
[0069] S4: This step is performed when the embedded information needs to be extracted, including the extraction of the payload and the restoration of the original host information, which is also called the decoding stage. In urDEED, this process is basically the reverse process of the encoding stage, so I won’t repeat it here.
[0070] S5: AES decryption: the structure of the AES decryption algorithm is the same as that of the encryption algorithm, and the transformation is the inverse transformation of the encryption algorithm transformation, and the key expansion strategy is slightly different.
Embodiment 3
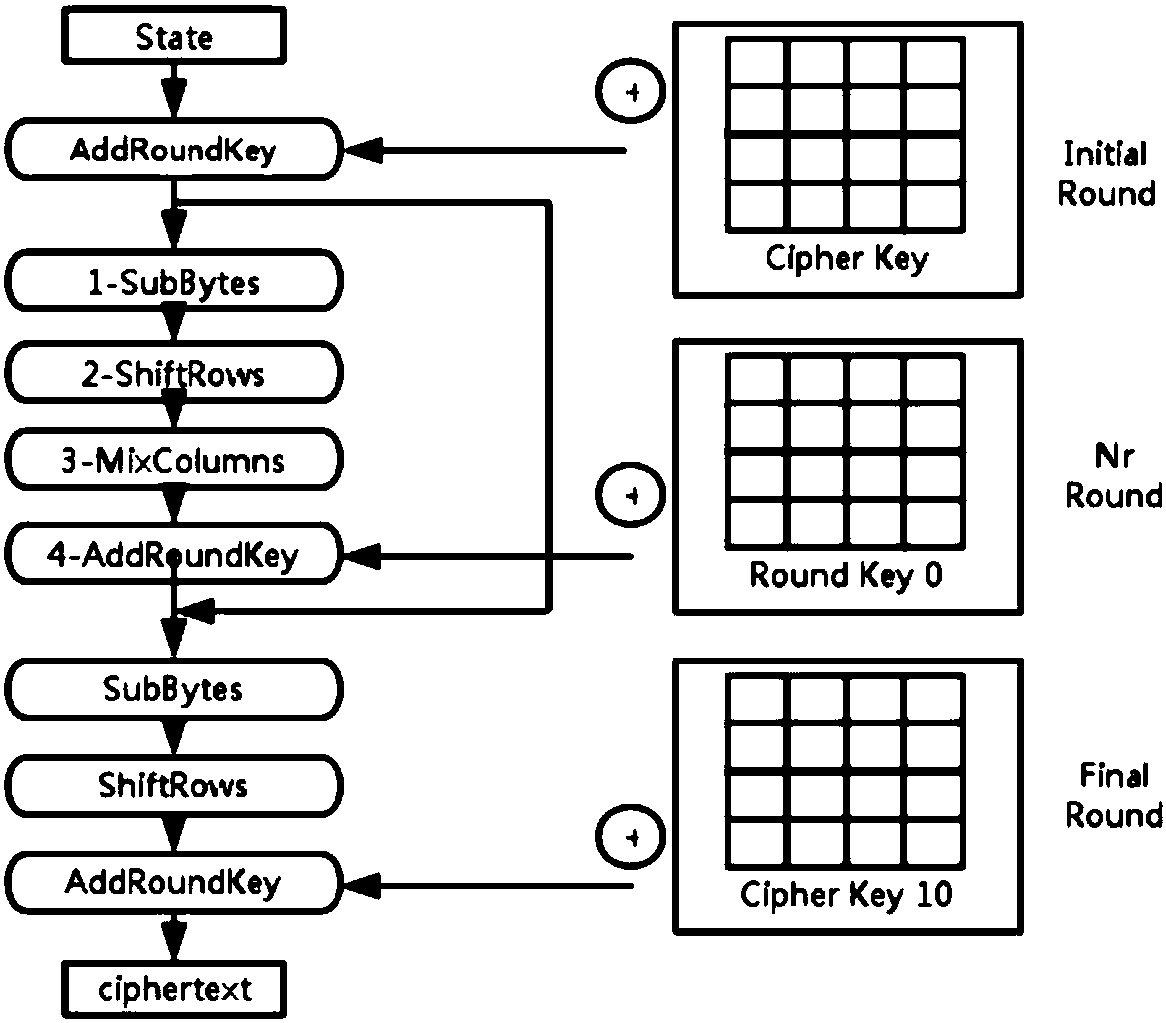
[0072] In said step S2, AES is an encryption algorithm issued by the National Institute of Standards and Technology (NIST), which is an efficient and safe symmetric encryption algorithm. The specific steps for encrypting a picture with the AES algorithm are as follows (eg figure 2 As shown, it is the flow chart of AES encryption):
[0073] S2-1: First, perform the AddRoundKey operation on the State, and XOR the RoundKey with the State;
[0074] S2-2: For each of the previous Nr-1 rounds, use S-BOX to perform a substitution operation on State, called SubBytes;
[0075] S2-3: Do a replacement ShiftRows for State;
[0076] S2-4: Do another operation on State MixColumns;
[0077] S2-5: Then perform the AddRoundKey operation;
[0078] S2-6: Finally, perform SubBytes, ShiftRows, and AddRoundKey operations in sequence, and the data becomes ciphertext.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com