Privacy protection method based on user cooperation
A privacy protection and user technology, applied in the field of privacy protection, can solve the problems of susceptibility to location-related attacks, also known as continuous query attacks, difficulty in ensuring the privacy of collaborative users, and inability to guarantee service quality, so as to save query time and reduce communication overhead , enhancing the effect of possibility and feasibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] specific implementation plan
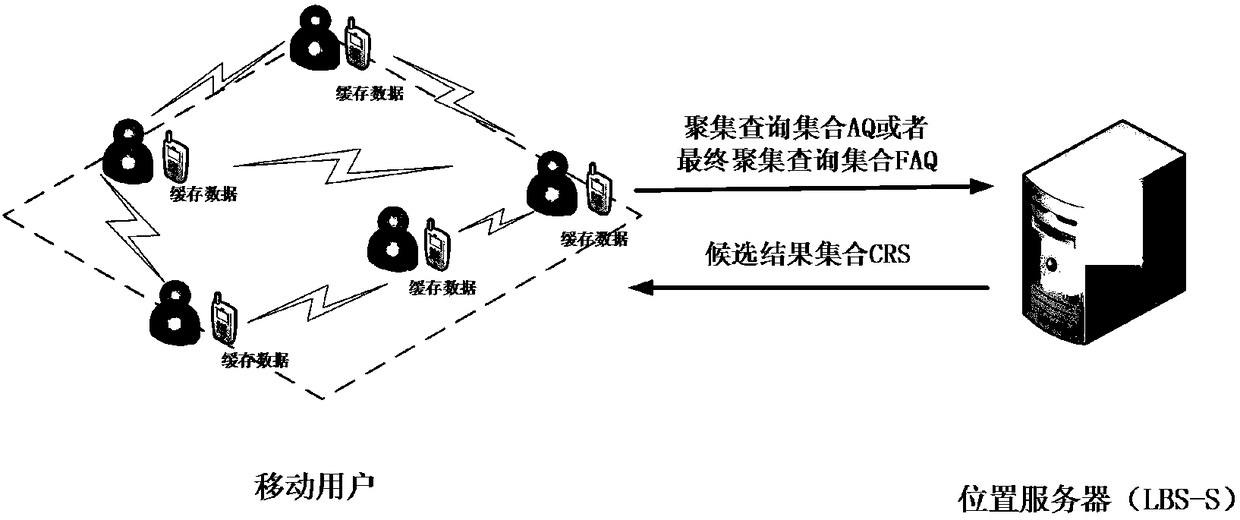
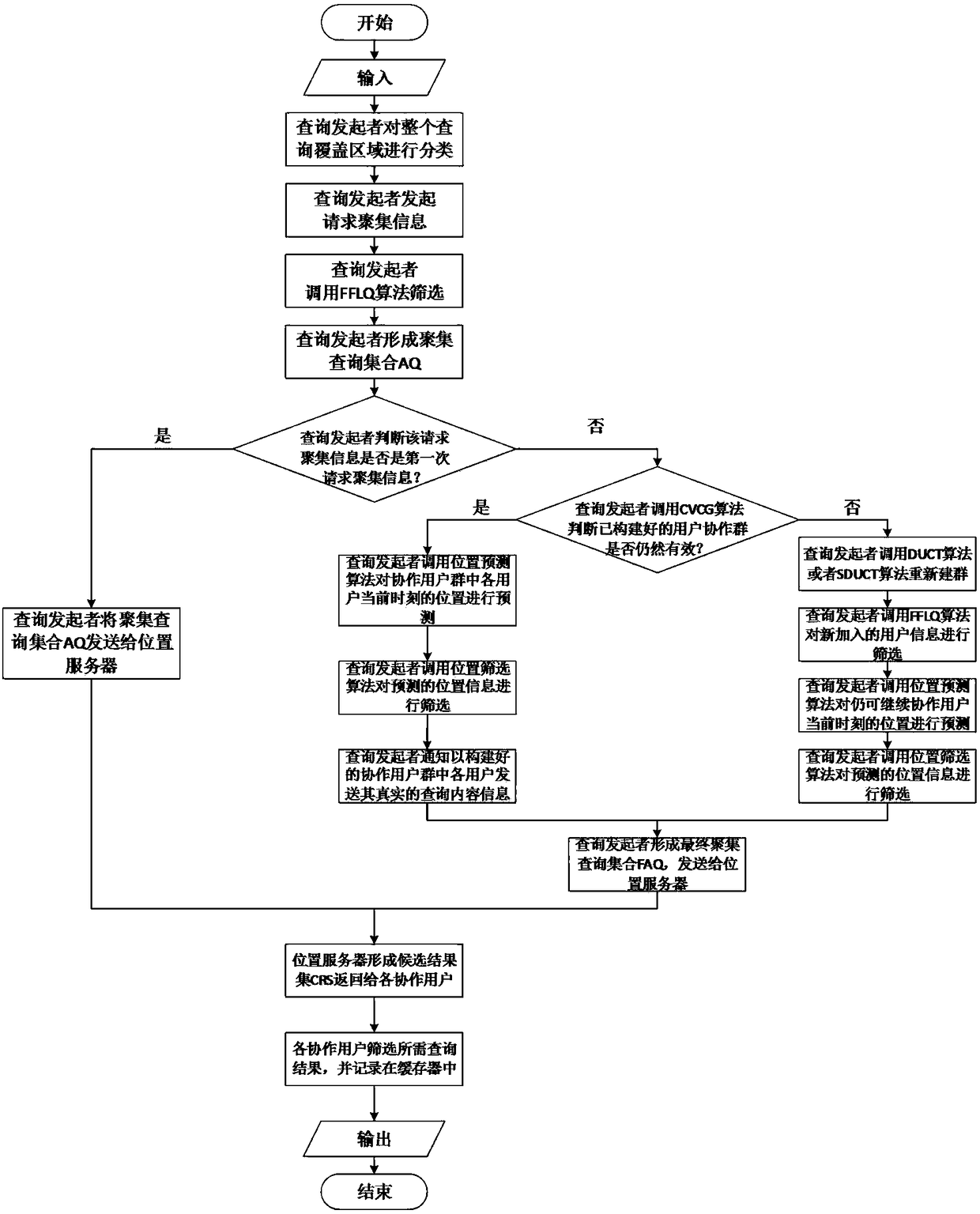
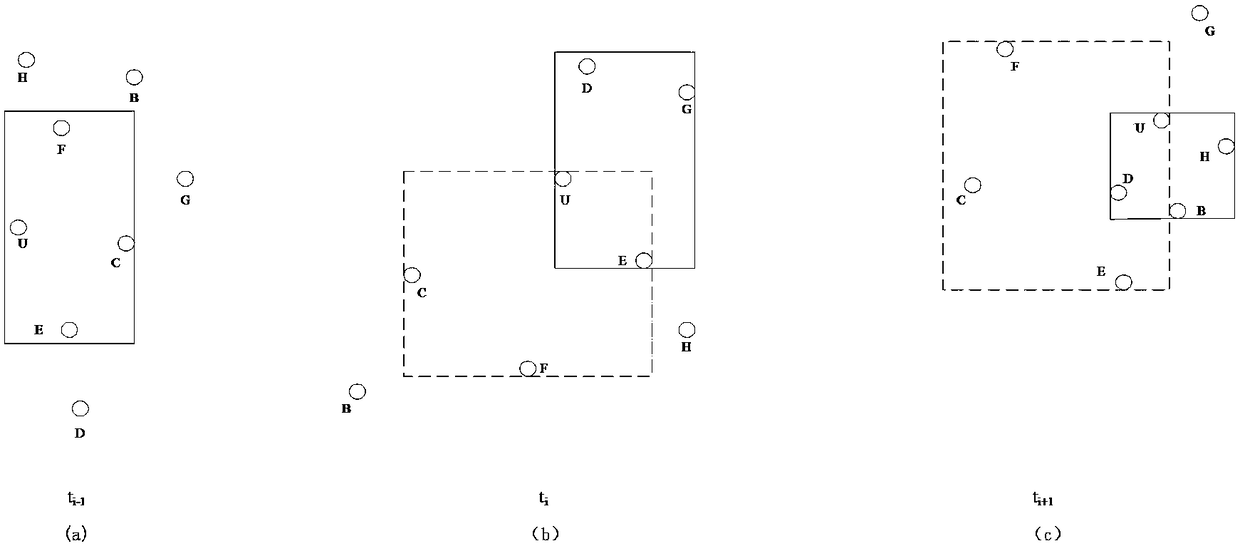
[0042] The central idea of the present invention is to adopt figure 1 A distributed privacy protection architecture based on user collaboration, which mainly sends out a collaborative group building request by the query initiator and broadcasts it; other users who can receive the collaborative group building request and are willing to cooperate with it reply the corresponding information to the query Initiator, and then the query initiator screens or predicts the returned information according to the number of queries and its privacy protection needs, and finally the query initiator sorts and summarizes to form an aggregated query set AQ or a final aggregated query set FAQ, and send it to the location server. The location server searches the database according to the received content, forms a corresponding candidate result set CRS and returns it to each user. Each cooperating user who receives the candidate result set filters the cand...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com