Point burying testing method, device and system
A test method and test-end technology, applied in the computer field, can solve the problems of wasting time comparison, reducing system bandwidth, database resource utilization, etc., and achieve the effect of saving packet capture operations and shortening comparison time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
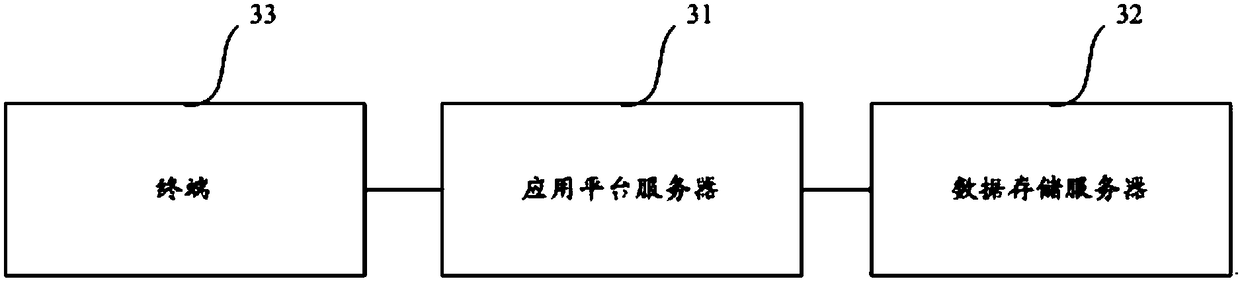
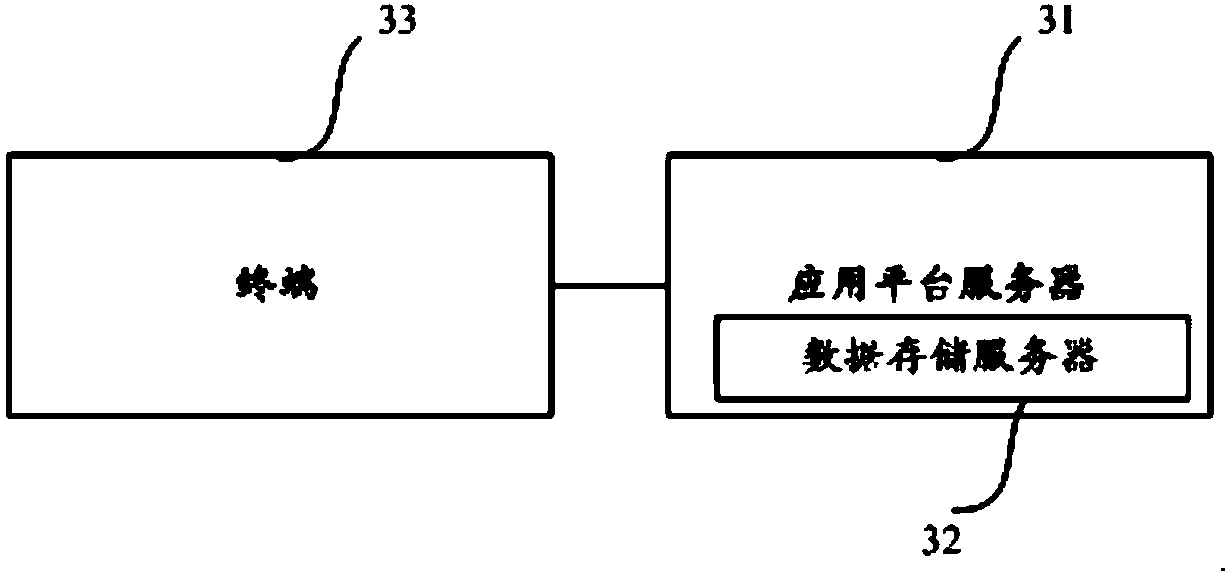
[0073] The first aspect of the embodiment of the present application shows a buried point test system, please refer to Picture 1-1 , and 1-2, the system includes:
[0074] Application platform server 31, a data storage server 32 connected to the application platform server 31, the data storage server 32 is set inside the platform server 31 or independently, and the application platform server 31 communicates with the terminal through the Internet 33 phase connection;
[0075] The terminal 33 is configured to send the exposed buried point data to the application platform server;
[0076] The terminal 33 shown in the embodiment of the present application is the most peripheral device in the computer network, and is mainly used for inputting user information and outputting processing results. The mobile terminals shown in the prior art, such as mobile phones and PADs, are all within the scope of protection of the embodiments of the present application.
[0077] The applicatio...
Embodiment 2
[0088] In the buried point testing method shown in the prior art, after the test manually triggers the buried point, the data captured by charles is compared with the pre-stored requirement document. The entire test process needs to compare the data captured by charles with the pre-stored requirement documents one by one, which wastes a lot of time in the test process, resulting in a long-term waiting state for the buried point detection system, which reduces the system bandwidth. , database and other resource utilization.
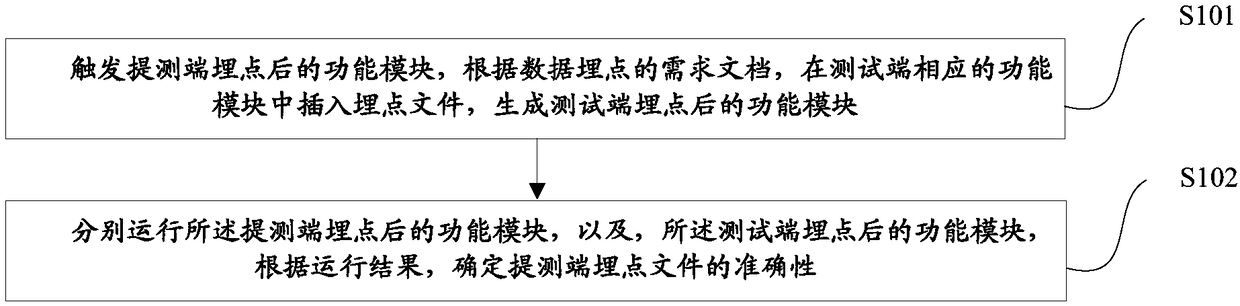
[0089] In order to solve the above problems, the second aspect of the embodiment of the present application shows a buried point test method, please refer to figure 2 , the method includes:
[0090] S101 triggers the function module after the embedded point of the test terminal, inserts the embedded point file into the corresponding function module of the test end according to the requirement document of the data embedded point, and generates the function...
Embodiment 3
[0099] In order to further shorten the testing time, the embodiment of this application shows a method for comparing buried point files. For details, please refer to image 3 , Embodiment 3 has similar steps to Embodiment 2, and the only difference is that step S102 in the technical solution shown in Embodiment 2 includes:
[0100] S10211 Run the functional module after the point-buying of the testing terminal to generate a point-burying file of the testing side, run the functional module after the point-burying of the testing terminal, and generate the point-buying file of the testing side;
[0101] S10212 Compare the buried point file of the testing end with the buried point file of the testing end, and determine the accuracy of the buried point file of the testing end according to the comparison result.
[0102] In the method shown in the embodiment of the present application, the embedded point file of the testing terminal is generated by running the functional module of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com