Resource adaptation resolution server DDoS attack detection defense method in smart collaborative network
A smart collaborative network and analysis server technology, applied in the field of network security, can solve problems such as increased overhead and ineffective implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
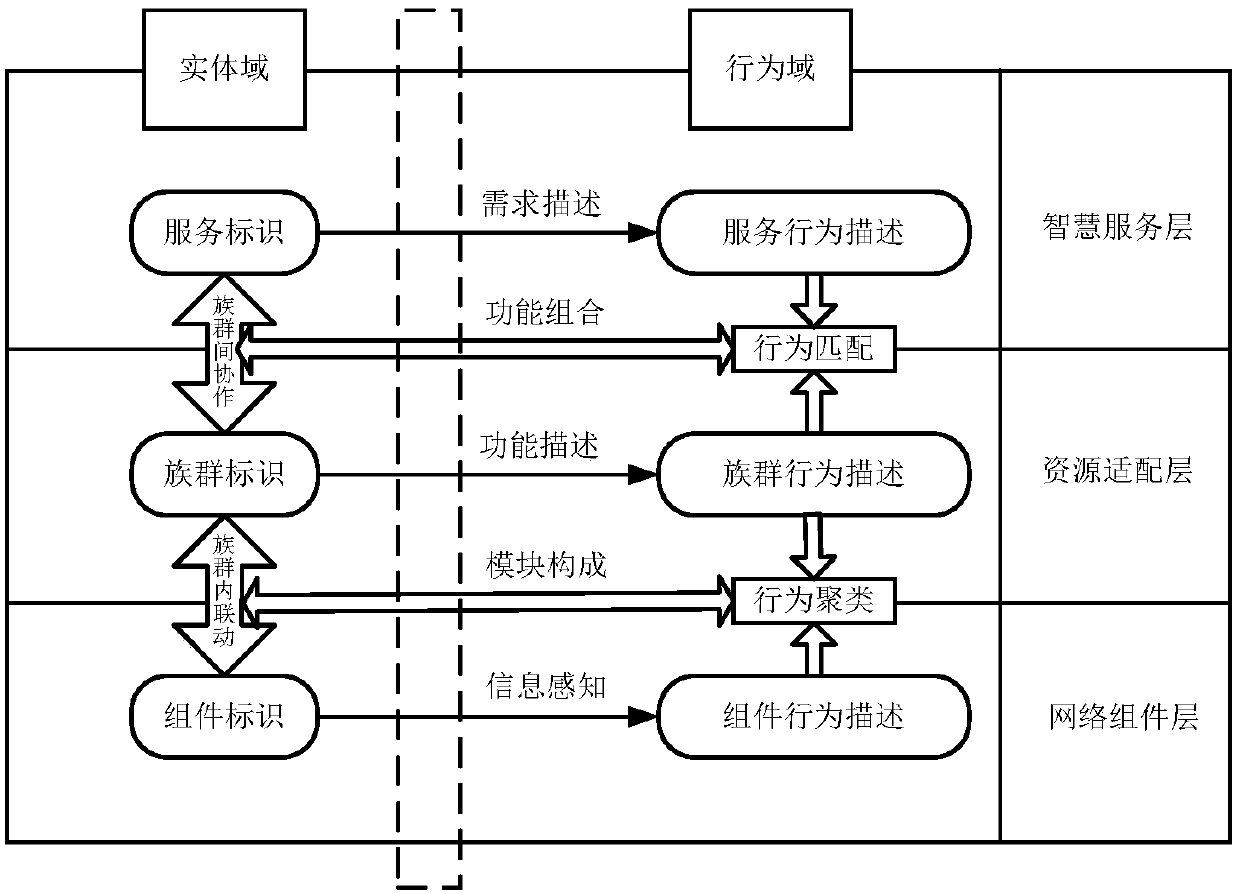
[0052] The embodiment of the present invention provides a method for detecting and defending DDoS attacks on resource adaptation analysis servers in a smart collaborative network. The attack situation is detected by using the decision tree algorithm, and the weight priority queue is used to respond to the attack to alleviate the attack. The impact of the attack provides security guarantee for the smart collaborative network and improves the security and reliability of the smart collaborative network.
[0053] In order to defend against the DDoS attack faced by the resource adaptation analysis server in the intelligent collaborative network, the embodiment of the present invention proposes a solution of connection migration, decision tree-based detection and weight priority queue defense.
[0054] The processing flow of a DDoS attack defense method for a resource adaptation analysis server in a smart collaborative network provided by an embodiment of the present invention is as ...
Embodiment 2
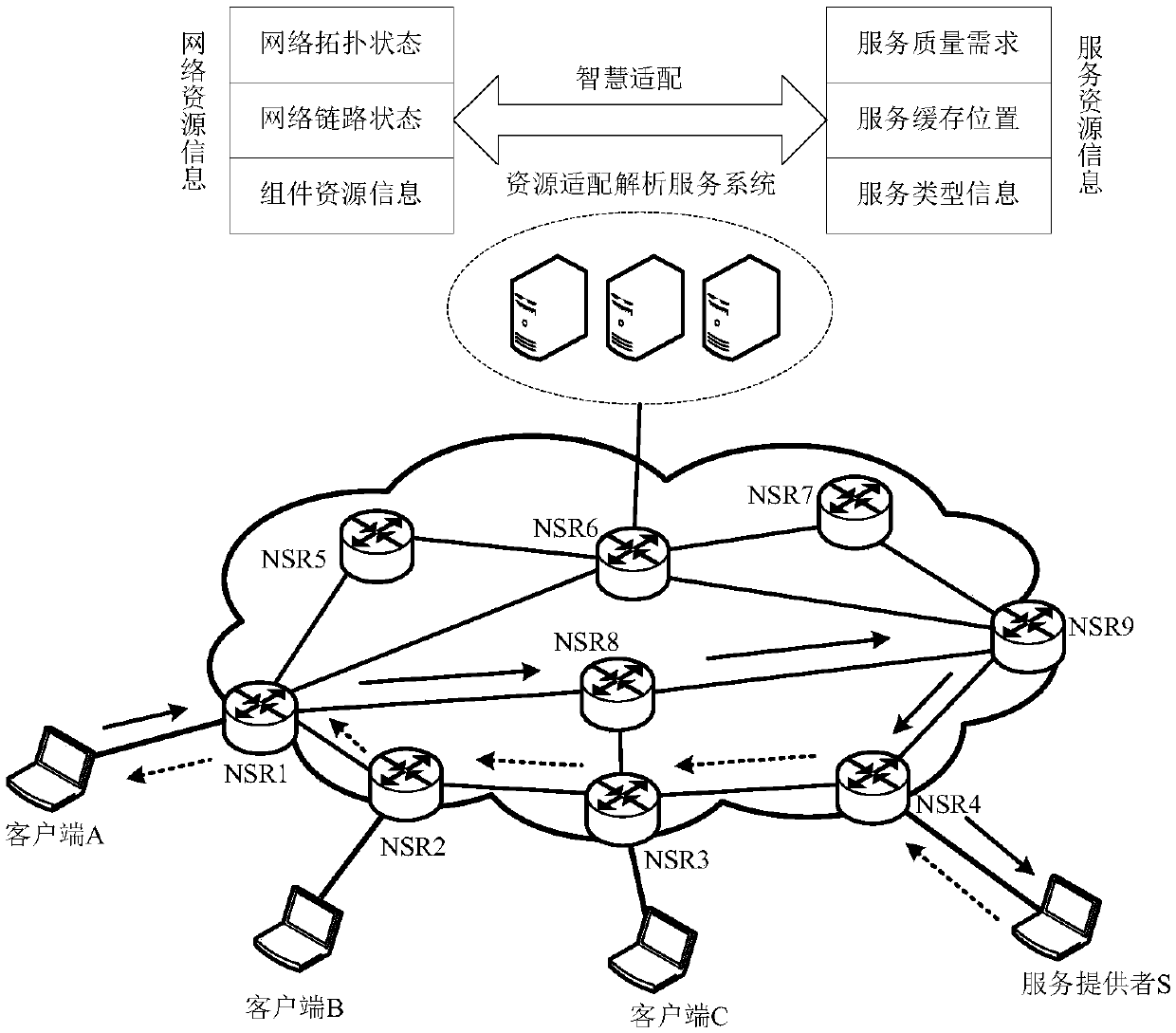
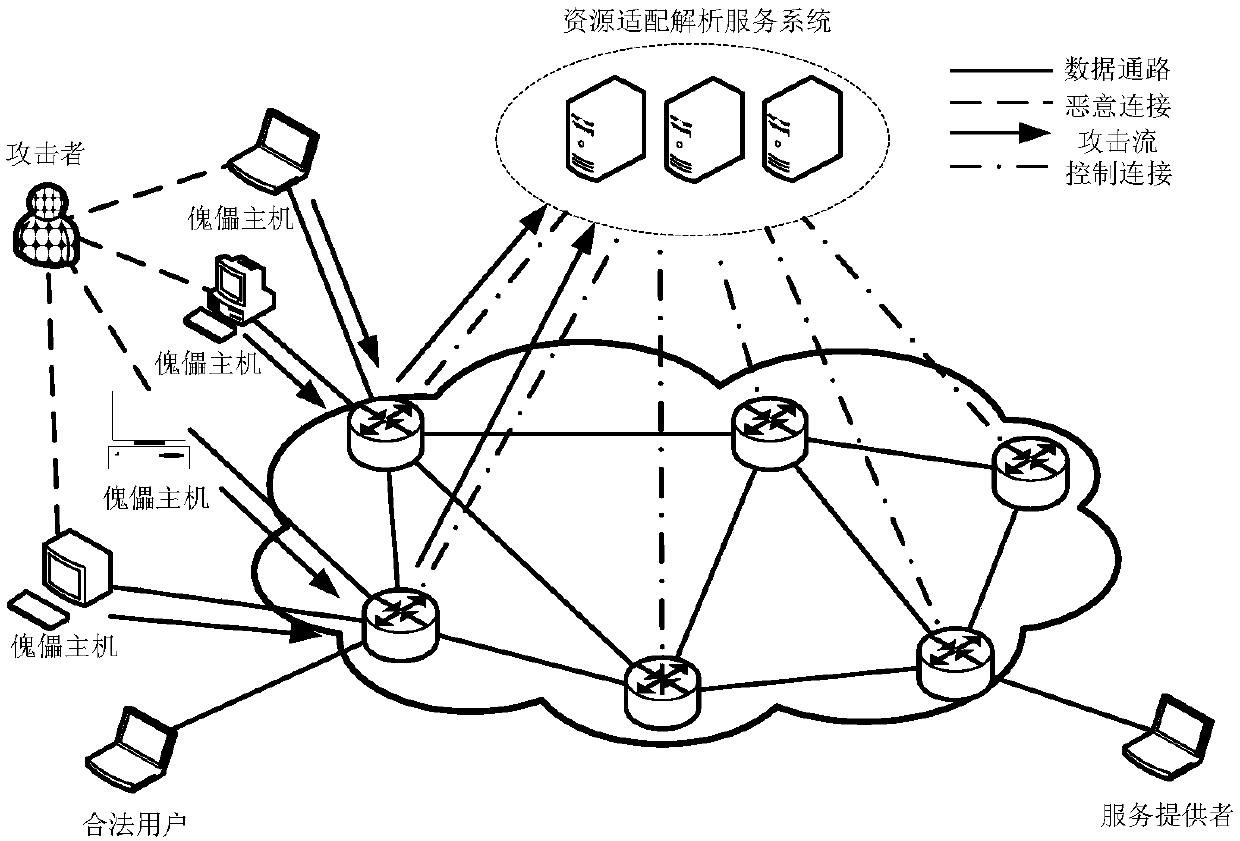
[0092] A schematic diagram of an example of DDoS attack detection and defense performed by a resource adaptation analysis server in a smart collaborative network provided by this embodiment is as follows Figure 6 As shown, the legitimate user is the service requester and normally initiates the service request, while the attackers A, B, and C forge a large amount of unknown traffic to launch DDoS attacks on the resource adaptation analysis server. In the DDoS defense of the resource adaptation analysis server, the present invention is divided into three stages in total. The first stage is the resource adaptation analysis server protection stage, applying the connection migration method, using the cache server as a proxy, caching and forwarding request packets, and limiting the forwarding rate; Judgment; the third stage is attack defense, differentiated forwarding request packets, and improving the service rate for legitimate users. These functions could have been completed on...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com