Network port traffic abnormality detection method and system
A technology for traffic anomalies and network ports, which is applied in the field of network port traffic anomaly detection, and can solve problems such as website and equipment loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0076] In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail in conjunction with the accompanying drawings and specific embodiments.
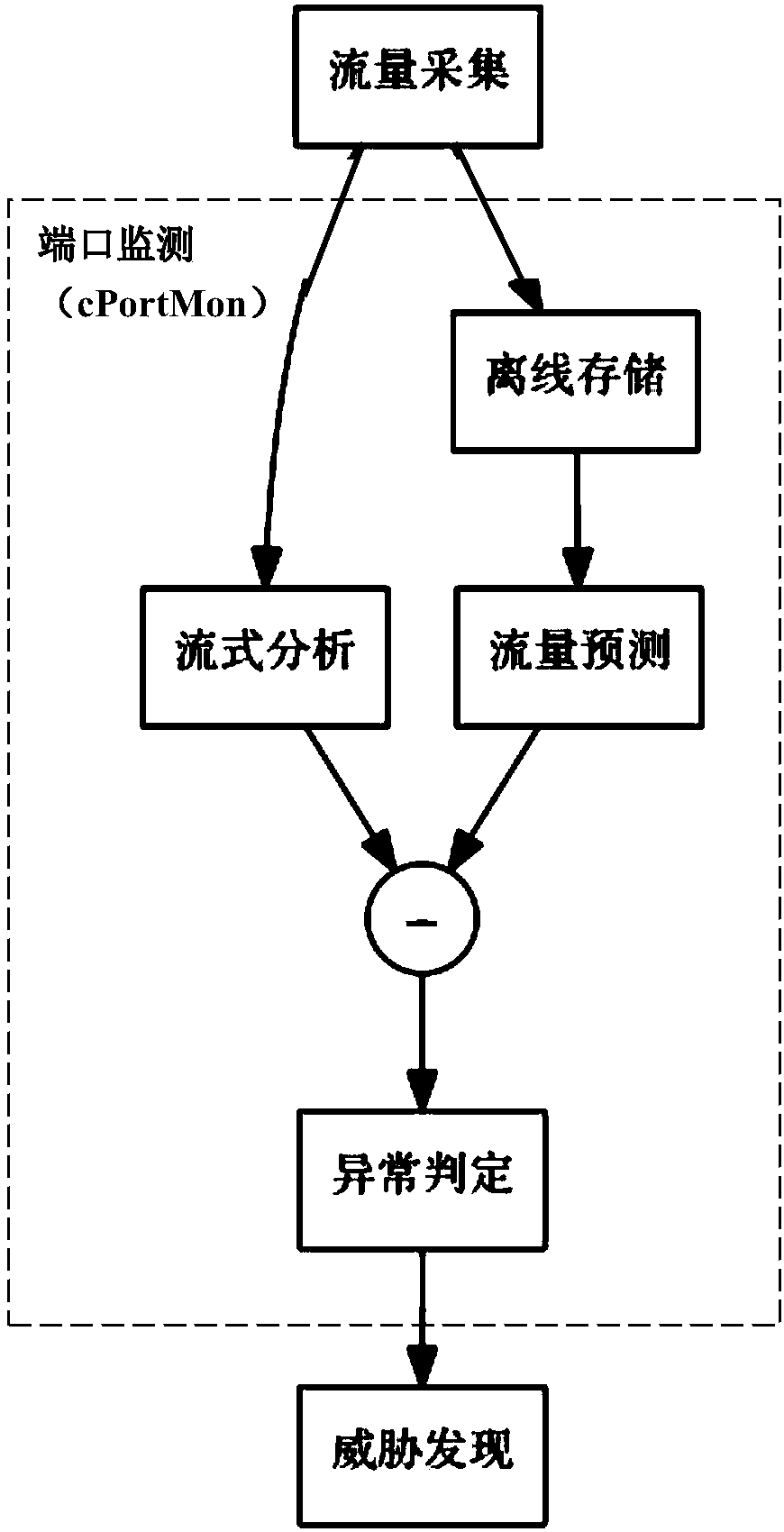
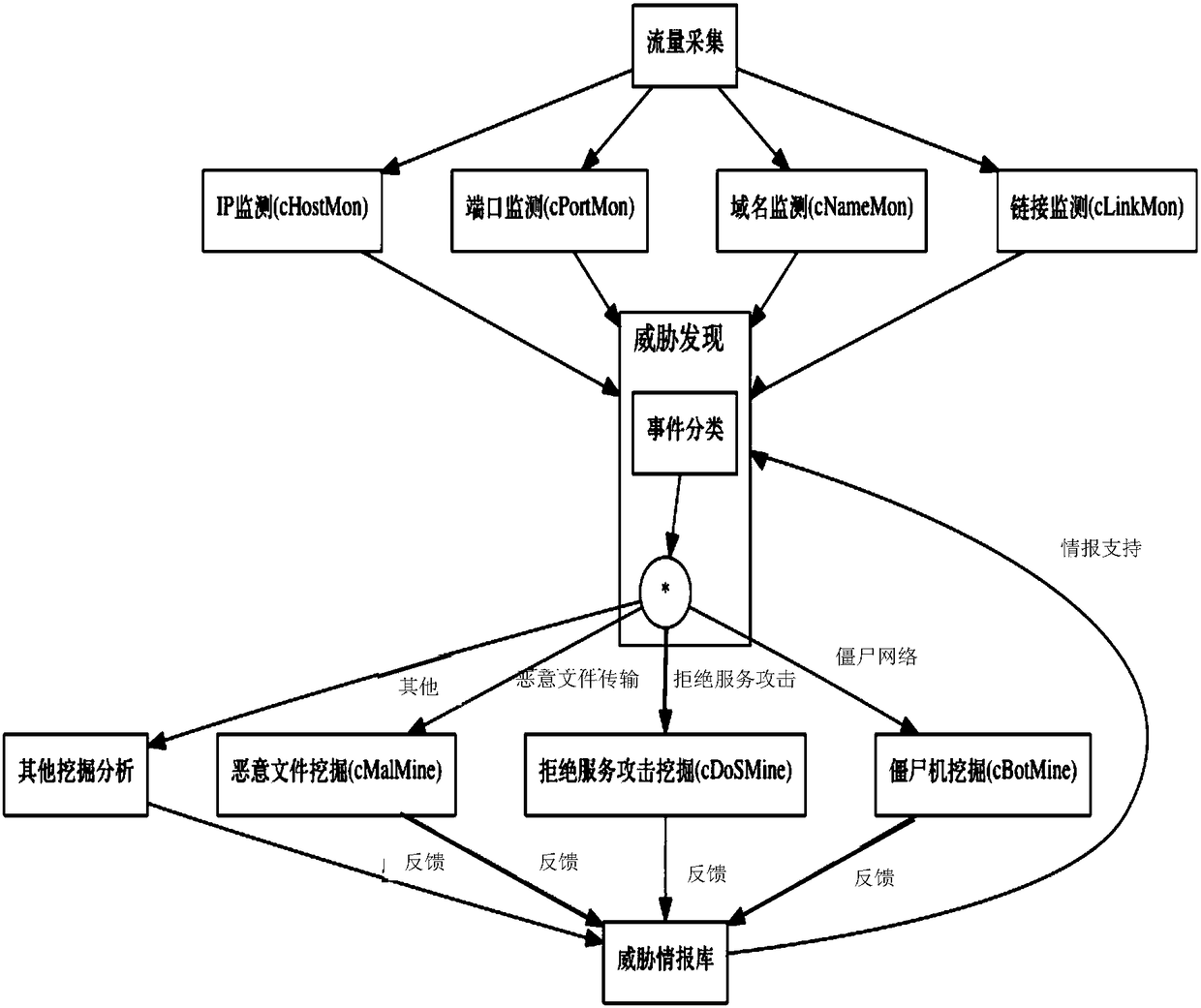
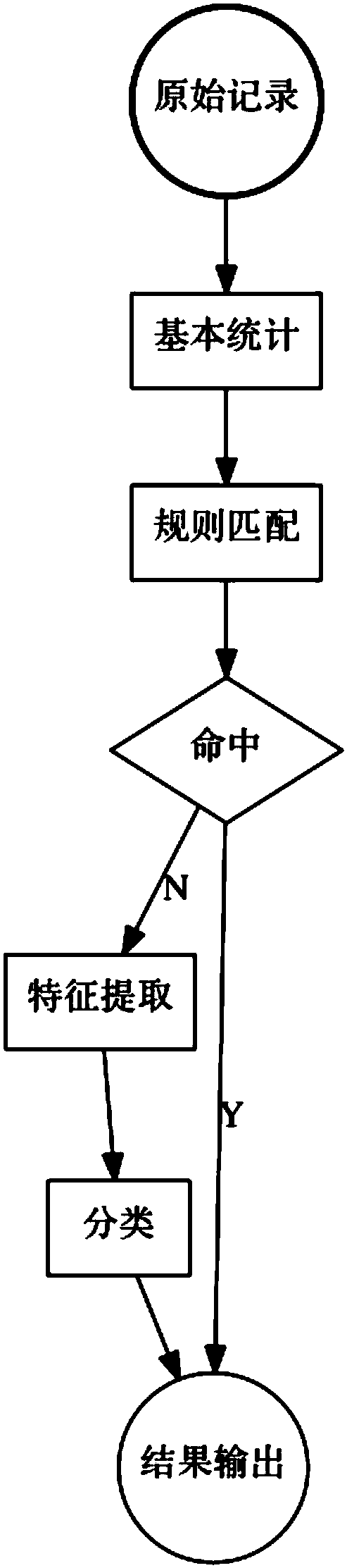
[0077] The traffic collection module of cNetS is implemented by a high-performance server, loaded with multiple 10 network cards, and runs the DPDK framework to realize high-speed traffic collection. The network traffic is exported by the backbone network router and imported through mirroring. The traffic collection module summarizes the traffic into a NetFlow summary format and outputs it to the cPortMon and cHostMon modules, exports summary fields such as the domain name, source and destination IP, and timestamp for the DNS response packet and outputs them to the cNameMon module, and exports URL, source and destination IP and other summaries for the HTTP request packet The information is output to the cLinkMon module.
[0078] The su...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com