Method, equipment and system for positioning controlled host in internal network
An intranet host and intranet technology, applied in the field of network security, can solve problems such as low efficiency, poor compatibility, and poor real-time performance, and achieve the effects of high processing efficiency, good real-time performance, and large degrees of freedom
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
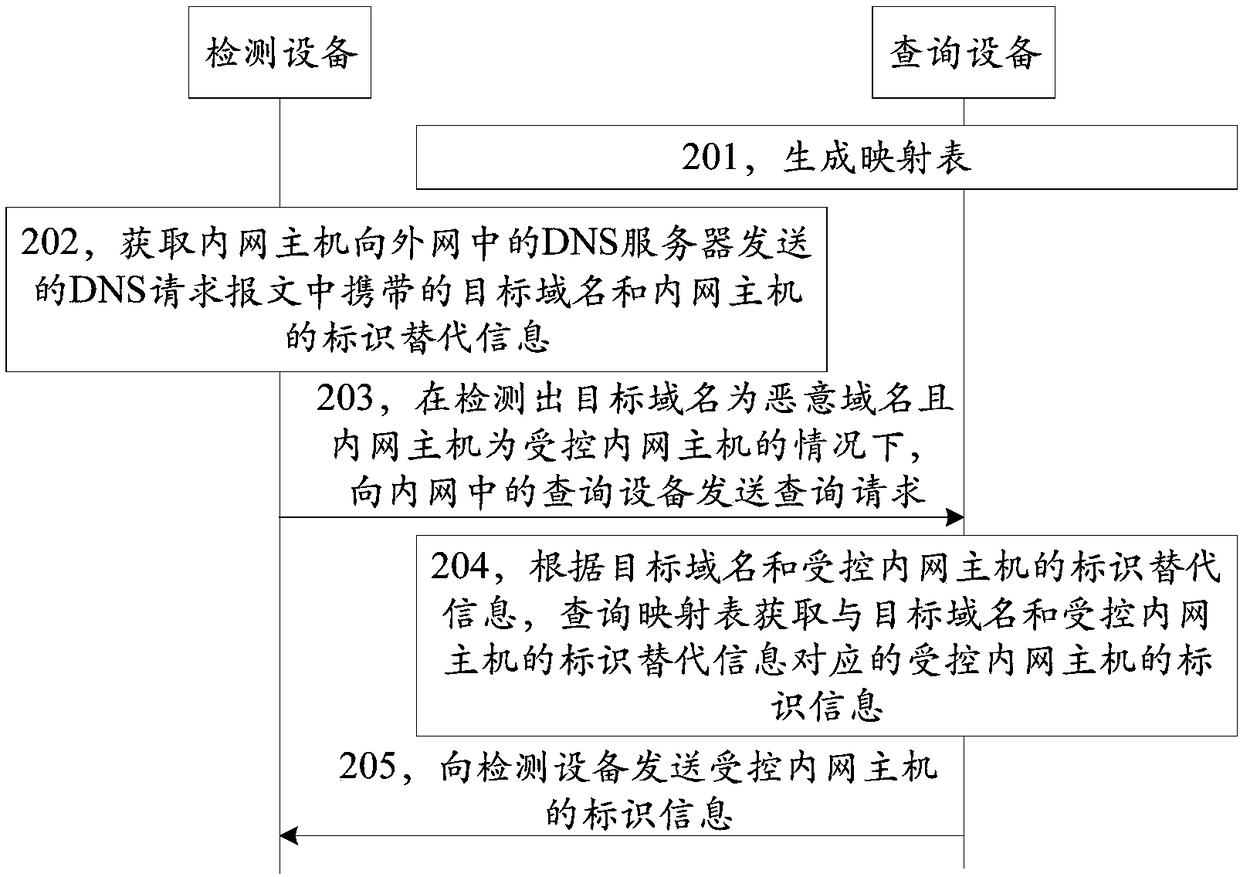
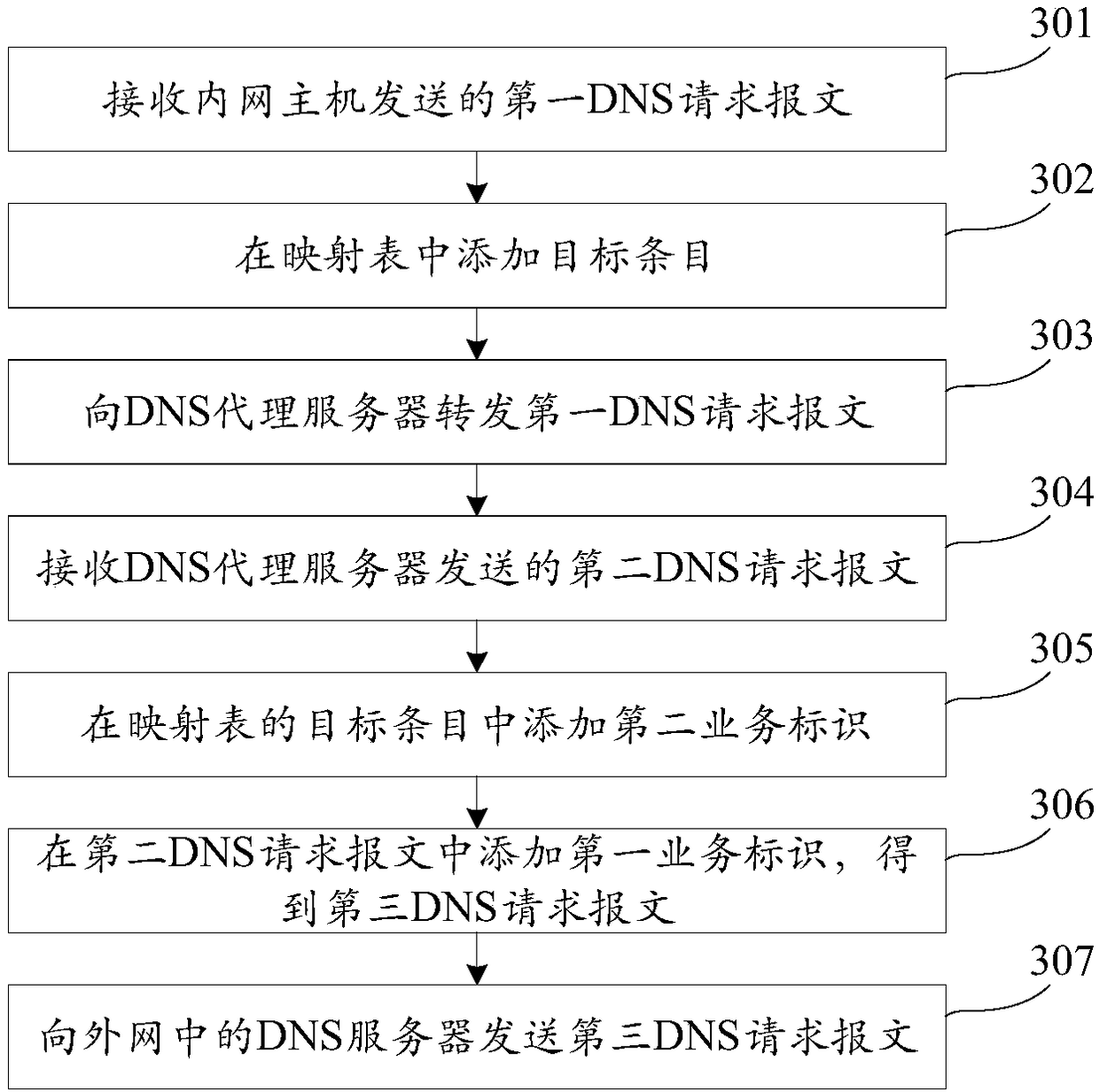
[0039] In order to make the purpose, technical solutions and advantages of the present application clearer, the technical solutions in the embodiments of the present application will be described below in conjunction with the accompanying drawings.
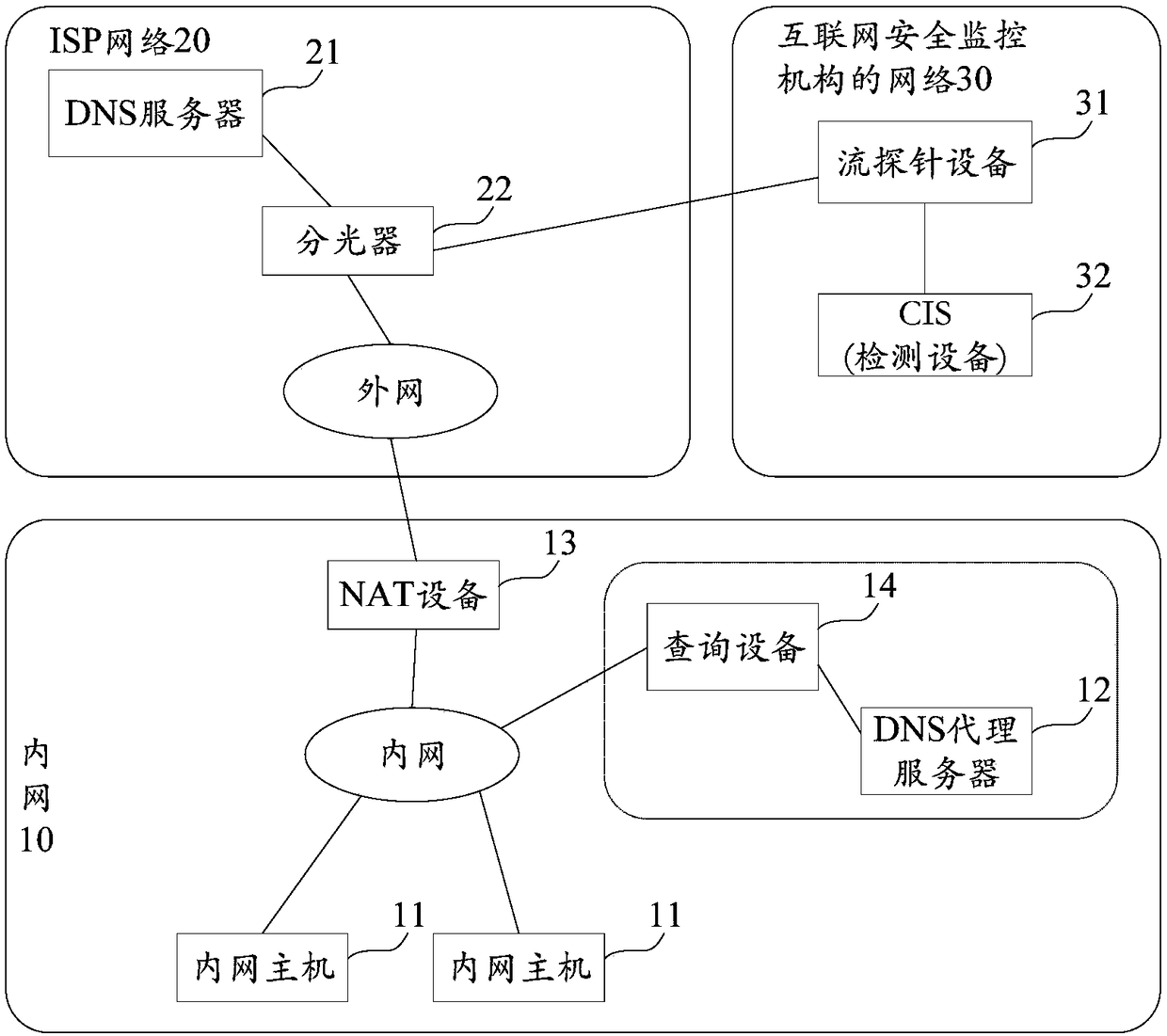
[0040] Before introducing and explaining the technical solution provided by this application, a brief introduction to "external network" and "intranet" is firstly made. The extranet is also called the public network, which refers to the wide area network, also known as the Internet (Internet). Intranet is also called a private network, which refers to a local area network. Compared with a wide area network, a local area network mainly refers to a small-scale computer interconnection network, such as the internal network established by governments, enterprises, government agencies, universities, shopping malls, and families. The external network and the internal network can use different address spaces. Generally speaking, the pack...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com