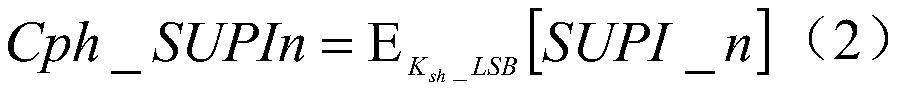A User Identity Renewal Method with Encrypted Transmission
A technology of user identity and update method, which is applied in the field of user identity update in encrypted transmission, which can solve the problems of user permanent identity leakage and inability to prevent user billing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
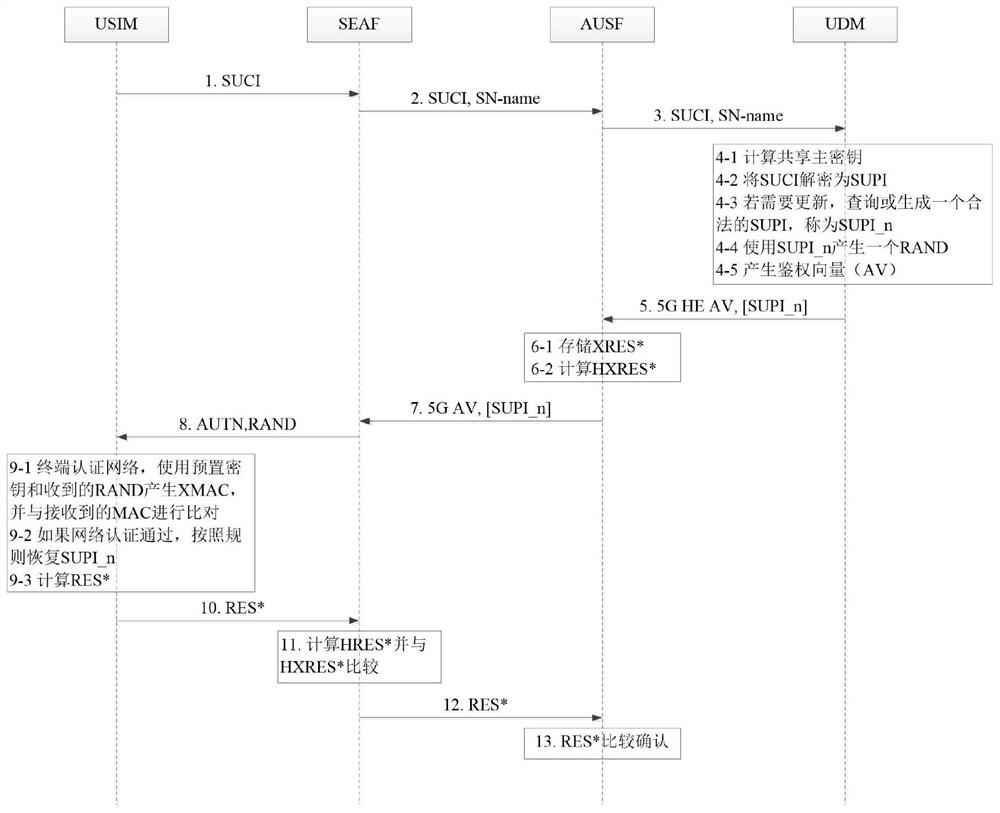
[0057] An embodiment 1 of the present invention discloses a user identity update method for encrypted transmission. The method is applied to the network side, and the network elements involved include SEAF (SEcurity Anchor Function, network security anchor function), AUSF (Authentication Server Function , authentication service function) and UDM (Unified Data Management, unified data management platform). Such as figure 1 shown, including the following steps:
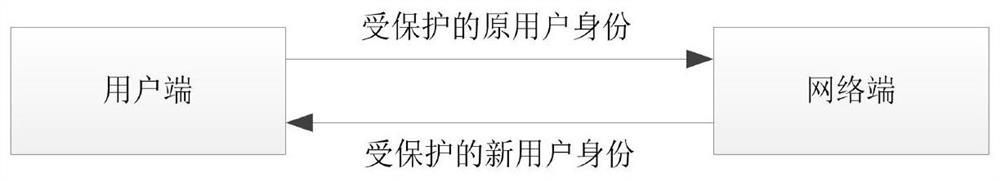
[0058] Step S1, receiving the user concealed identity SUCI (SUbscriber Concealed Identity) sent by the client;
[0059] This step includes:
[0060] According to the 3GPP standard process, when attaching, receive the user hidden identity SUCI sent by the user end;
[0061] According to the 3GPP standard procedure, SEAF initiates an authentication request and starts the authentication process. Send information such as SUCI and network name (SN-name) to the AUSF of the home network;
[0062] According to the 3GPP sta...
Embodiment 2
[0103] In this embodiment, the feedback information calculated by the user terminal is RES*, such as figure 2 Shown, step 1-step 5 is identical with embodiment 1;
[0104] Step S6-2. Compare the RES* and XRES* sent by the user end, and if they are consistent, the authentication is passed.
[0105] This step includes:
[0106] SEAF receives the RES* sent by the client, SEAF calculates HRES* and compares it with HXRES*;
[0107] SEAF sends RES* to AUSF;
[0108] AUSF compares the RES* sent by the user end with the XRES*, if they are consistent, the authentication is passed, and the user identity SUPI is updated to SUPI_n. If not, the authentication fails, and the user identity is not updated successfully, and the authentication and authentication process is required to be initiated again.
Embodiment 3
[0110] In this embodiment, the feedback information calculated by the client is AUTS, and steps S1-S5 are the same as in Embodiment 1;
[0111] Step S6-3: The UDM receives the AUTS sent by the user end, and verifies the SQN in the AUTS in the UDM. If the verification is passed and the MAC-S in the AUTS is consistent with the MAC in the AUTN, the authentication is passed.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com