Confrontation learning-based method and system for generating image confrontation verification codes
A learning method and captcha technology, applied in the field of image adversarial captcha generation based on confrontational learning, can solve the problem of failing to deceive cracker classifiers, failing to meet the needs of anti-captcha defense, and failing to understand the captcha cracker model in advance Parameters and other issues to achieve the effect of improving security, enhancing security, and adapting
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] The present invention will be further described in detail below with reference to the accompanying drawings and embodiments. It should be noted that the following embodiments are intended to facilitate the understanding of the present invention, but do not limit it in any way.
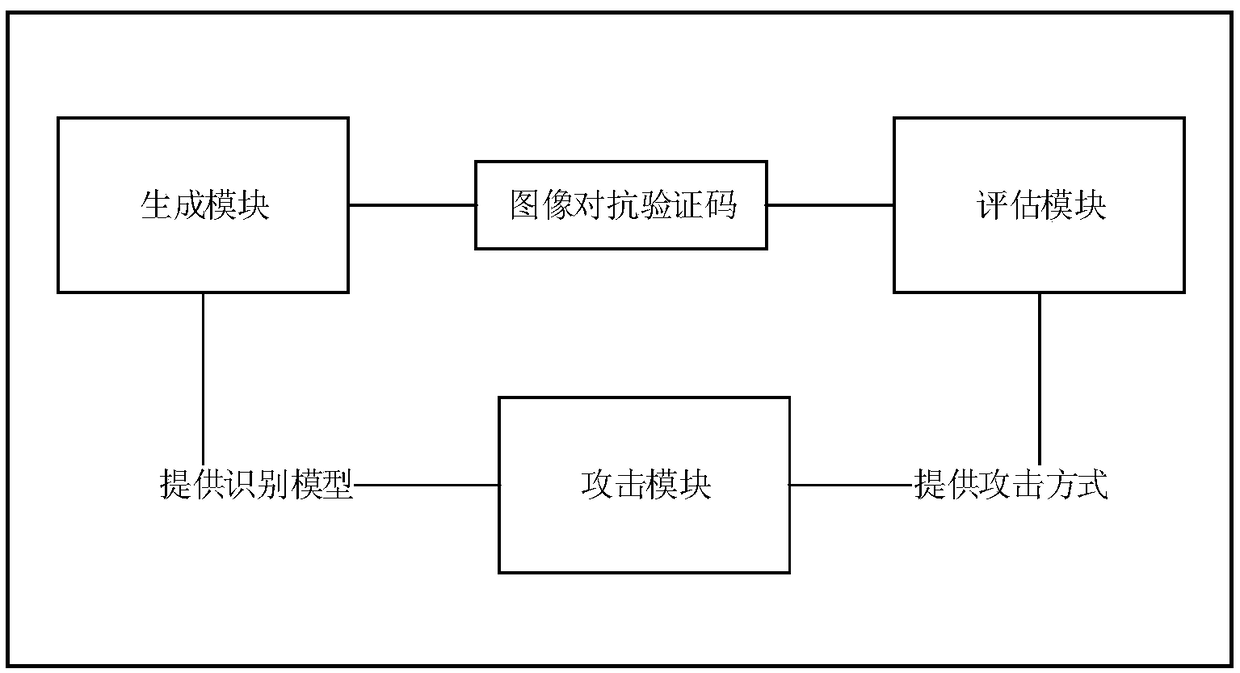
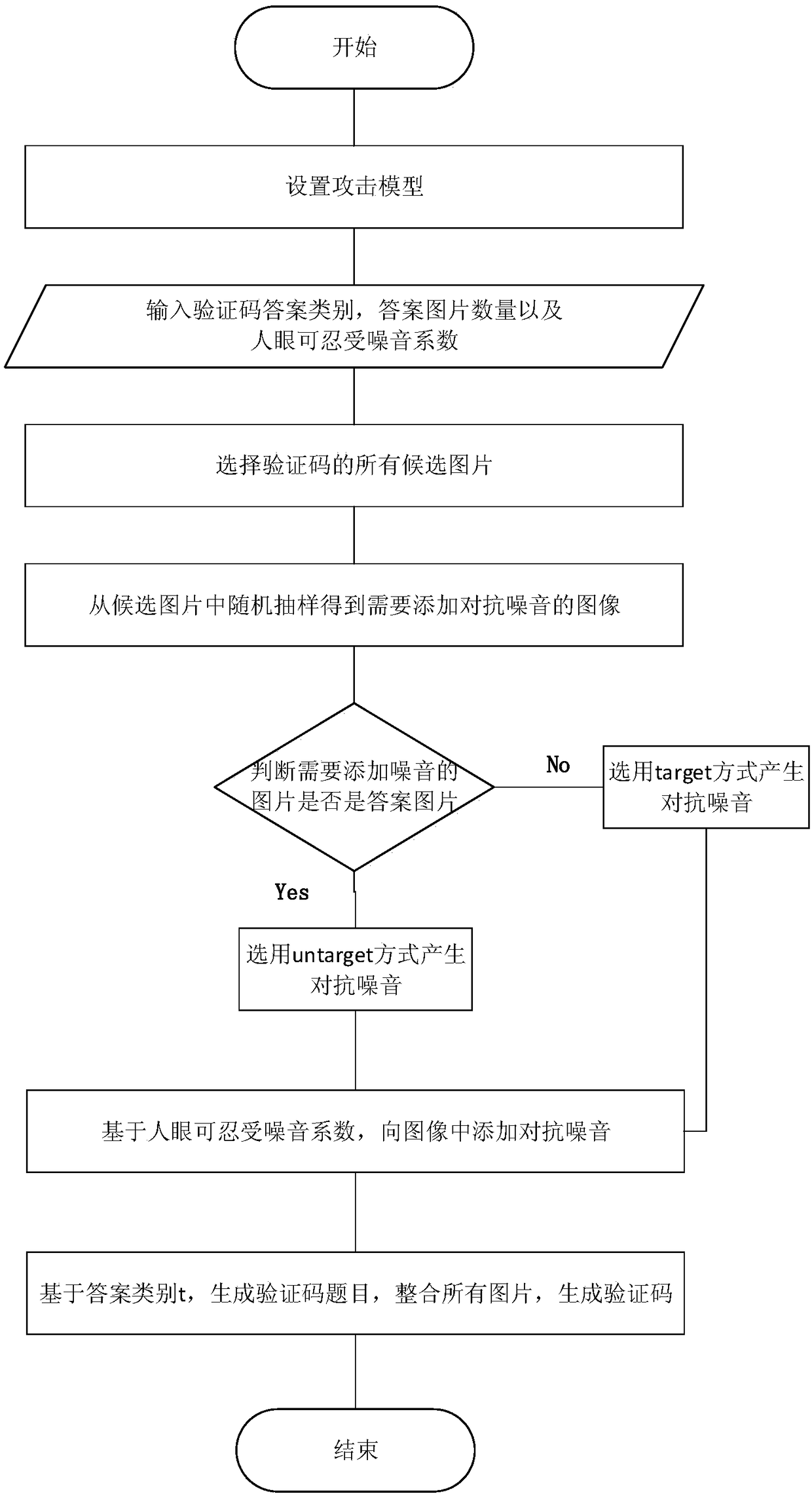
[0051] Such as figure 1 As shown, the image adversarial verification code generation system based on adversarial learning includes three modules: attack module, generation module and evaluation module. The attack module is used to provide image recognition models and attack methods to the generation module and evaluation module; the function of the generation module is to generate image confrontation verification codes according to user requests; the function of the evaluation module is to use the attack means provided by the attack module to simulate the confrontation generated by the production module Verification code, and finally evaluate the security against verification code by simulating ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com