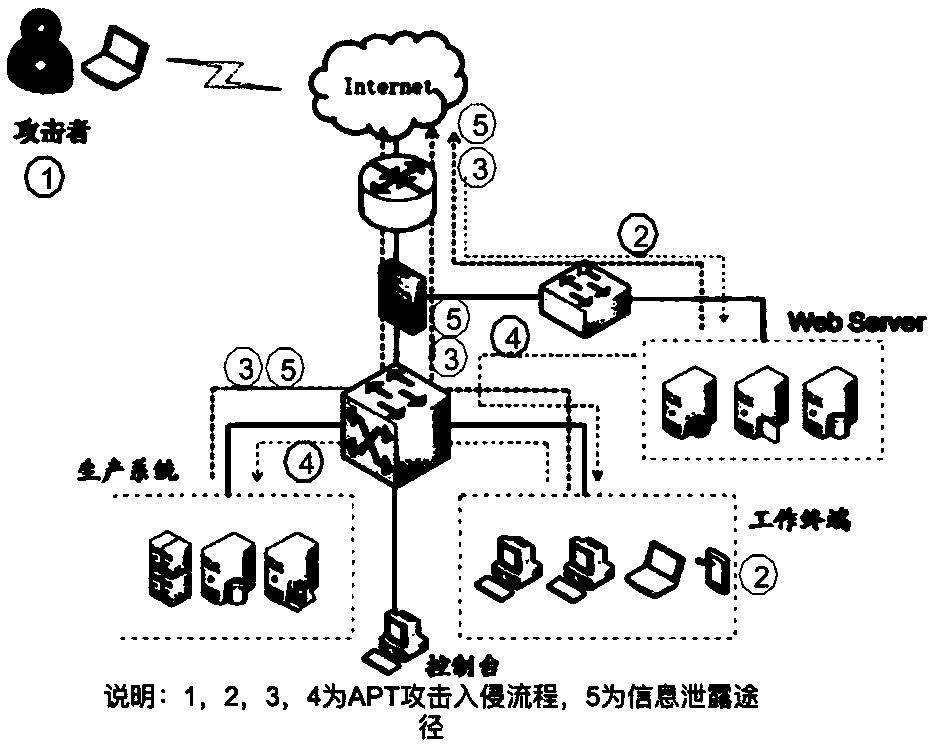
APT attack defense method and system adopting mimetic technology
An attack defense system and technology, which is applied in the field of APT attack defense method and system using mimic technology, can solve problems such as inflexibility, complex strategies, and false positives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0053] The overall idea of this embodiment is to provide a method for defending against APT attacks using mimic technology, including:
[0054] Virtualize the mimicry services of different forms of business and the mimicry files of sensitive files, when the mimicry business and / or the mimicry files are accessed, access log information obtained in real time, analyze the access log information, and analyze according to the analysis results , send alarm information, and take appropriate measures according to the alarm information. This defense method effectively solves the shortcomings of several previous APT defense methods, and at the same time achieves accurate discovery and location of APT attack behaviors that have infiltrated into the enterprise without affecting the normal use of users.
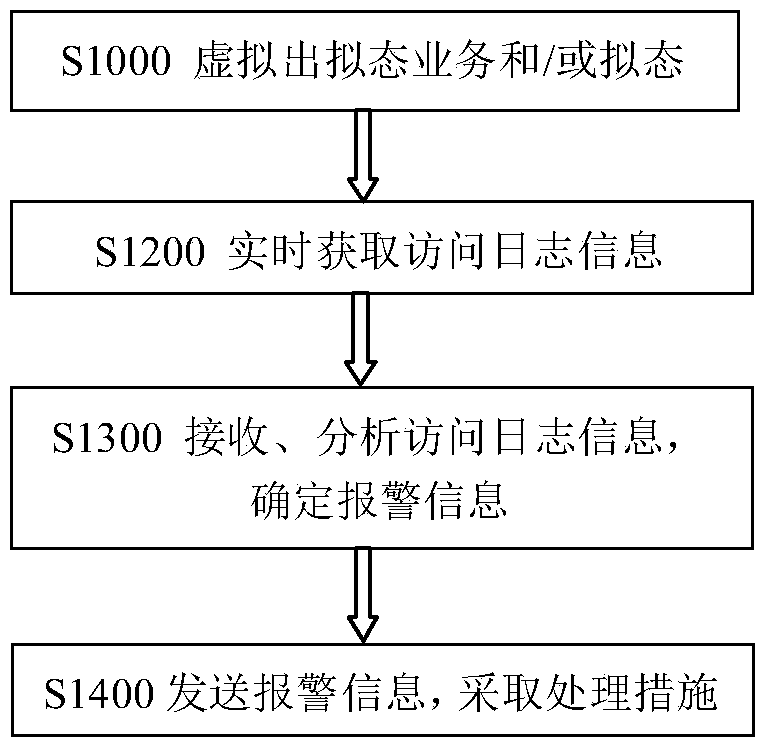
[0055] Specifically, in the APT attack defense method using mimicry technology in this embodiment, such as figure 2 Shown:
[0056] Step S1100 is to virtualize the imitation business...
Embodiment 2
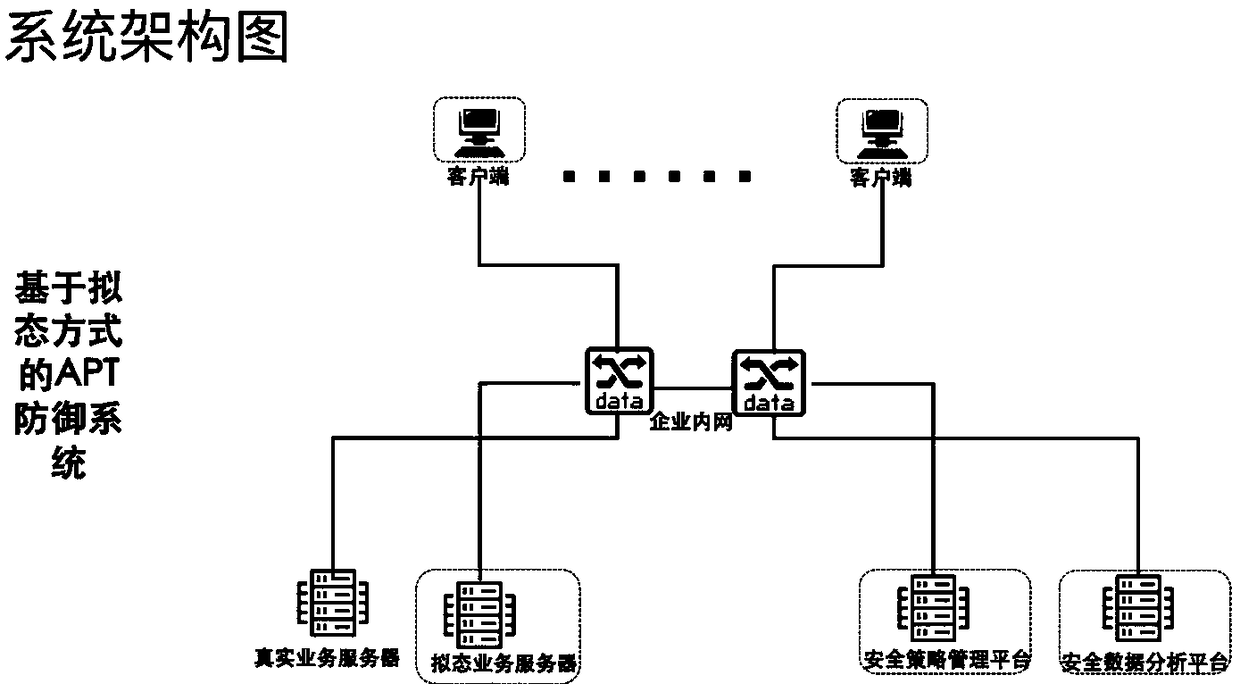
[0078] The overall concept of this embodiment is to provide an APT attack defense system using mimicry technology, the system architecture is as follows image 3 As shown, it includes: mimic module, client module and security data analysis module.
[0079] The mimicry module is used to virtualize the corresponding virtual business of different forms of business, and virtualize the mimicry files of different types of sensitive files;
[0080] The client module is used to accept the virtual service data packet sent by the mimic module and cooperate with the mimic module to form a mimic service and / or accept the mimic file data packet sent by the mimic module, and send a virtual request of mimic file and / or mimic service to the mimic module;
[0081] The mimetic service is composed of corresponding virtual services of different forms of services and service ports matched with the virtual service, and the sensitive file is a file in which warning codes are implanted in virtual fil...
Embodiment 3
[0096] Such as Figure 4 It is a schematic flow diagram of the method for APT attack defense using mimic technology in this application:
[0097] A. According to the actual business status inside the client, deploy the corresponding business on the mimic module such as the mimic business server, such as database service, web service and decoy file.
[0098] B. Configure the mimicry policy on the security policy management platform according to the user's internal network conditions, business conditions and related information. For example, mimic database services are deployed on certain computers, web services are simulated on certain computers, and some mimic “sensitive files” are placed on certain computers.
[0099] C. After the client module establishes a network communication connection with the security policy management platform, the security policy management module will push a virtual data packet to the client module on the target client, and after the target client ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com