Key-destroying circuit structure
A circuit structure and key destruction technology, applied in the field of security encryption, can solve the problems of ineffective protection measures and information security, and achieve the effect of solving key destruction and ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
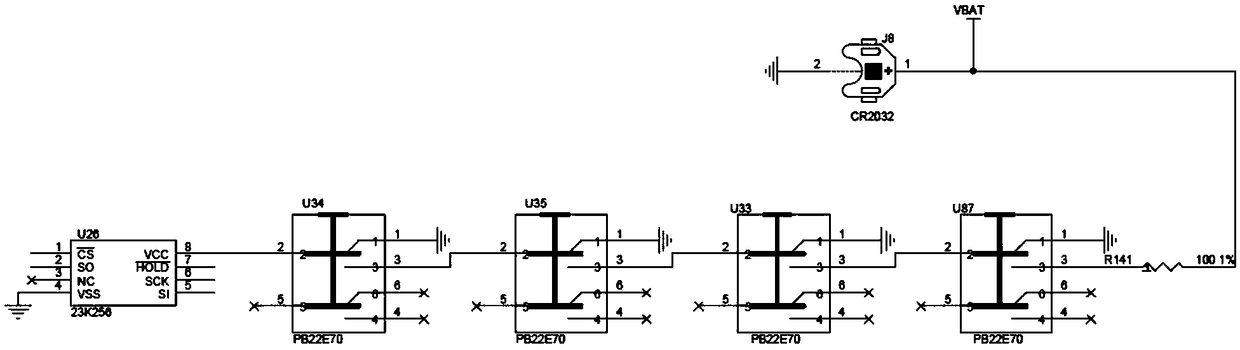
[0022] Such as figure 1 As shown, a key destroying circuit structure is mainly used in information security equipment. The chassis of the information security equipment is a 1U standard structure with a square shape, which is used to prevent the key stored in it from being illegally stolen. Including PCB substrate, said PCB substrate is installed in the case of information security equipment, said PCB substrate is equipped with 4 micro switches (U34, U35, U33, U87), battery holder J8, button battery and storage key Module U26.
[0023] The model of the button battery is CR2032, the voltage is 3.3V, it is directly installed on the battery holder J8, and is used to provide working power for the storage key module U26. Specifically: the button battery is connected to the pin 3 of the micro switch U87 through the current limiting resistor R141 through the pin 1 of the battery holder J8, the pin 2 of the micro switch U87 is connected to the pin 3 of the micro switch U33, and the m...
Embodiment 2
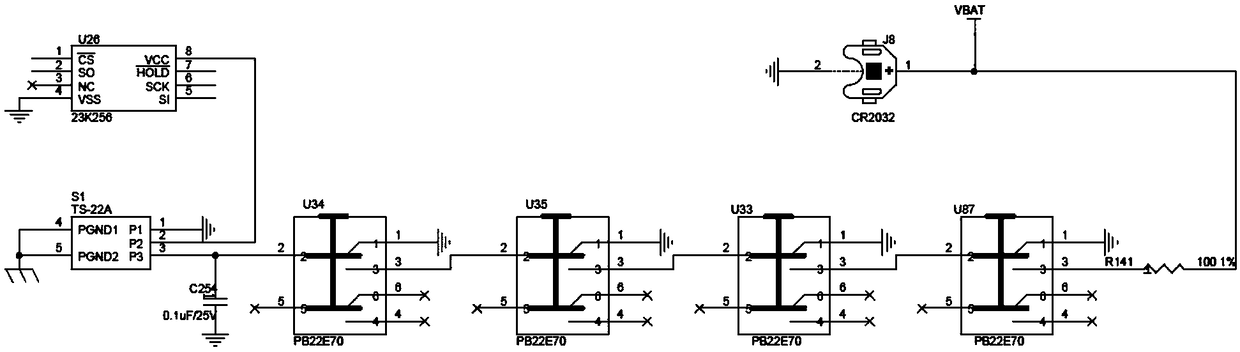
[0026] In the first embodiment above, four micro switches (U34, U35, U33, U87) are used to automatically detect whether there is an external action of opening the cover. Once an action of opening the cover is detected, the storage key module U26 is triggered to destroy the key. However, the machine cover is generally tightly installed on the chassis with screws, so that if an outsider needs to open the cover, all the screws must be unscrewed before the machine cover can be opened. In this way, the key cannot be destroyed quickly. It is also inconvenient and needs to be equipped with corresponding tools. Therefore, the technical solution of the first embodiment above is optimized so that the operator can quickly and conveniently destroy the key. Such as figure 2 As shown, the difference from the first embodiment above is that the present invention also includes a self-locking push-button key-killing switch S1, the model of which is TS-22A, and the self-locking push-button key...
Embodiment 3
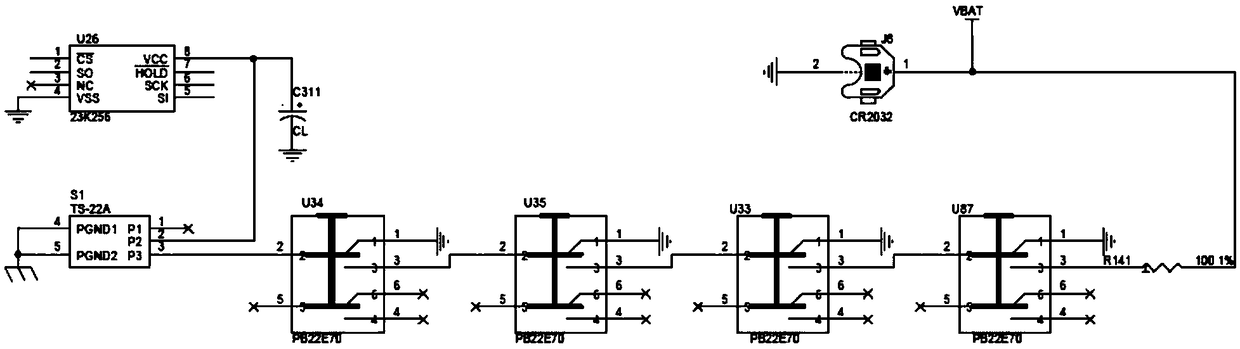
[0028] Although the technical solution of the above-mentioned embodiment 2 can realize active, fast and convenient destruction of keys, since the self-locking push-button key destroying switch S1 is installed on the chassis, it is easy for external operators to accidentally misuse the self-locking push-button destroying key Switch S1, for example, if you accidentally touch the self-locking key-type destroying switch S1, the storage key module U26 will also destroy the key immediately, that is, there is a technical problem that the key is destroyed due to misoperation. In order to solve this problem, this embodiment three has carried out technical optimization on the basis of the technical solution of embodiment two, such as image 3 As shown, that is, a large capacitance storage charge C311 is provided between the self-locking push-button key destroying switch S1 and the storage key module U26 circuit. That is, the pin 2 of the self-locking push-button key destroying switch S1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com