Identity verification method, device and system
An identity verification and identity technology, applied in the direction of user identity/authority verification, transmission system, digital transmission system, etc., can solve the problem of low accuracy of identity verification methods, improve the level of security verification, improve accuracy, and improve favorability. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0038] According to an embodiment of the present application, an embodiment of an identity verification system is provided.
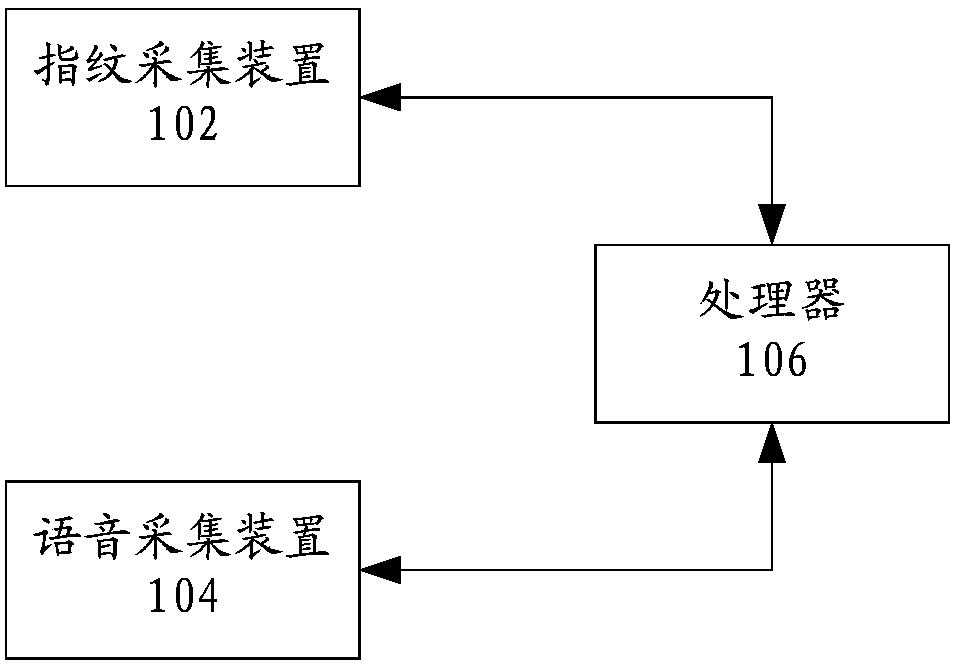
[0039] figure 1 is a schematic diagram of an identity verification system according to an embodiment of the present application, such as figure 1As shown, the system can include:
[0040] The fingerprint collection device 102 is configured to collect the fingerprint information of the target object entered in the fingerprint entry area in the current display interface.
[0041] Specifically, the above-mentioned fingerprint collection device can be set on a mobile device, and the setting position depends on the design of the mobile device manufacturer, including: a front-mounted fingerprint device and a rear-mounted fingerprint device. This application does not specifically limit this, and the mobile device may include: Smart phones (including Android mobile phones, IOS mobile phones), IPADs, tablet computers, handheld computers and other equipment; th...
Embodiment 2
[0153] According to the embodiment of the present application, an embodiment of an identity verification method is also provided. It should be noted that the steps shown in the flow chart of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and, Although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
[0154] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal, a computer terminal, or a similar computing device. Figure 10 It is a block diagram of a hardware structure of a mobile device for implementing an identity verification method according to an embodiment of the present application. Such as Figure 10 As shown, the mobile device 100 may include one or more (shown by 1002a, 1002b, ..., 1002n in the figure) processor 1002 (the processor ...
Embodiment 3
[0184] According to the embodiment of the present application, an embodiment of an identity verification method is also provided. It should be noted that the steps shown in the flow chart of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and, Although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
[0185] Figure 12 is a flow chart of another identity verification method according to an embodiment of the present application. Such as Figure 12 As shown, the above method may include the following steps:
[0186] Step S1202, enter the fingerprint information of the target object in the fingerprint entry area in the current display interface, and collect the currently entered voice information, wherein the currently entered voice information is the information entered by the target object while re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com