Network traffic anomaly detection method based on historical time point taking method
A technology of network traffic and historical time, which is applied in the field of network traffic anomaly detection based on historical time point method, can solve the problems of high false positive rate, high computing cost, and difficult training samples, and reduce computing cost and storage cost , Solve the huge amount of calculation, solve the effect of contour mutation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described below with reference to the accompanying drawings and embodiments, and the mode of the present invention includes but not limited to the following embodiments.
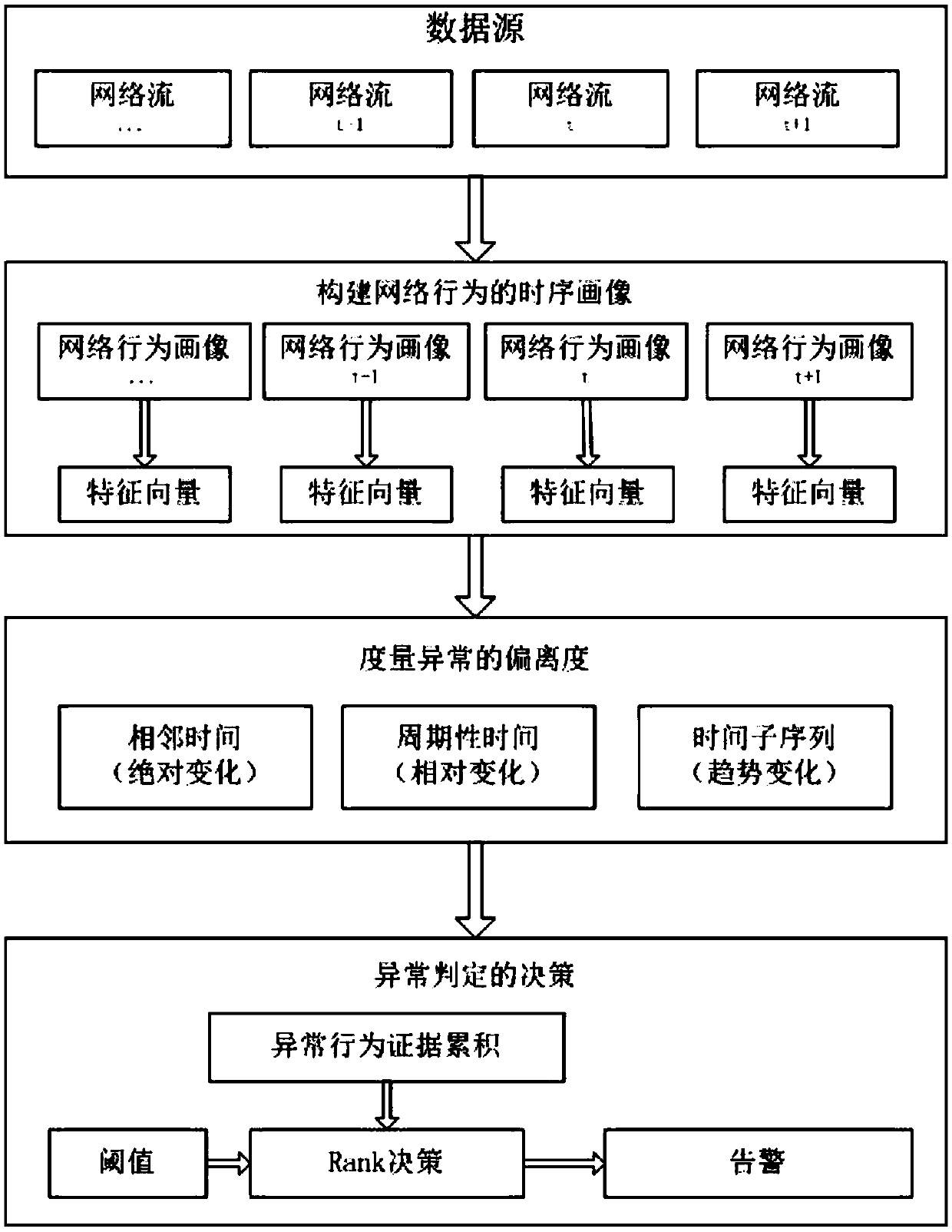
[0030] Such as figure 1 As shown, the present invention discloses a network traffic anomaly detection method based on the historical time point method, and the method includes the following steps:
[0031] (1) Deploy port mirroring routing at the network traffic collection point to capture full-flow data packets and form a network flow timing data source;
[0032] (2) Use a fixed time window to perform statistics on network traffic behavior characteristics of network flow time series data sources, form a network behavior time series feature vector, describe the network behavior portrait of the current time window, and construct network behavior time series feature vectors through multiple time windows Time series portrait of network behavior;
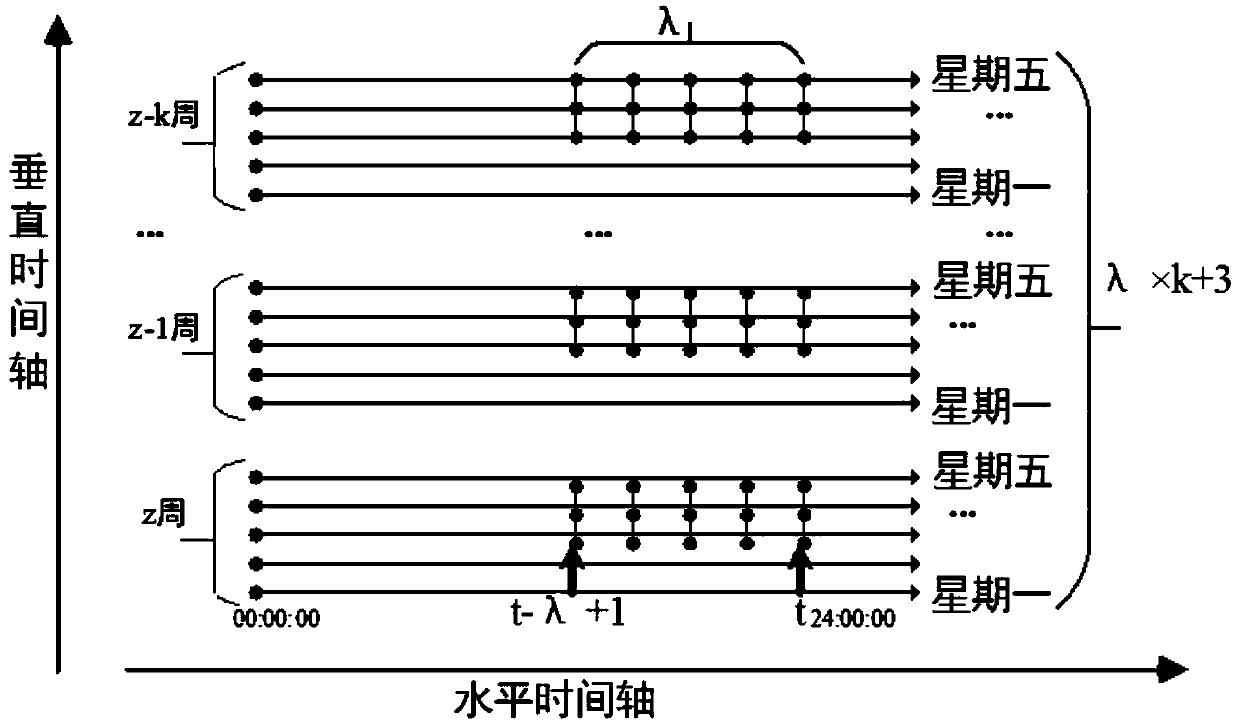
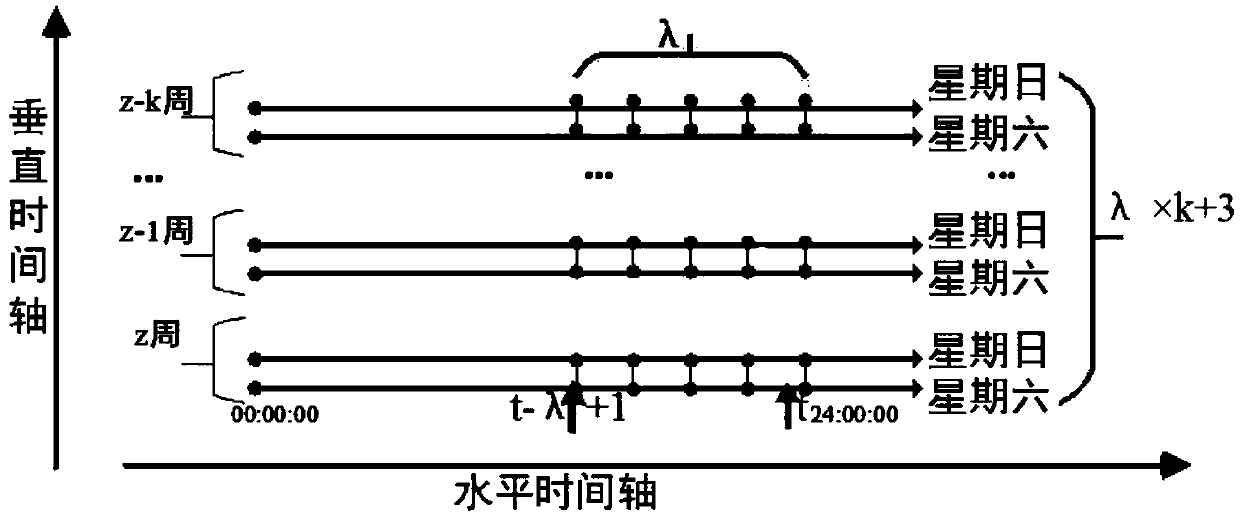
[0033] Here, the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com