The invention relates to a method for establishing and verifying a live broadcast link address and a corresponding device
A link address and verification method technology, which is applied in the field of construction and verification methods of live link addresses and corresponding devices, can solve the problems of low universality and adaptability, and the inability to use browsers, so as to prevent hijacking and tampering and improve the effectiveness of anti-theft sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
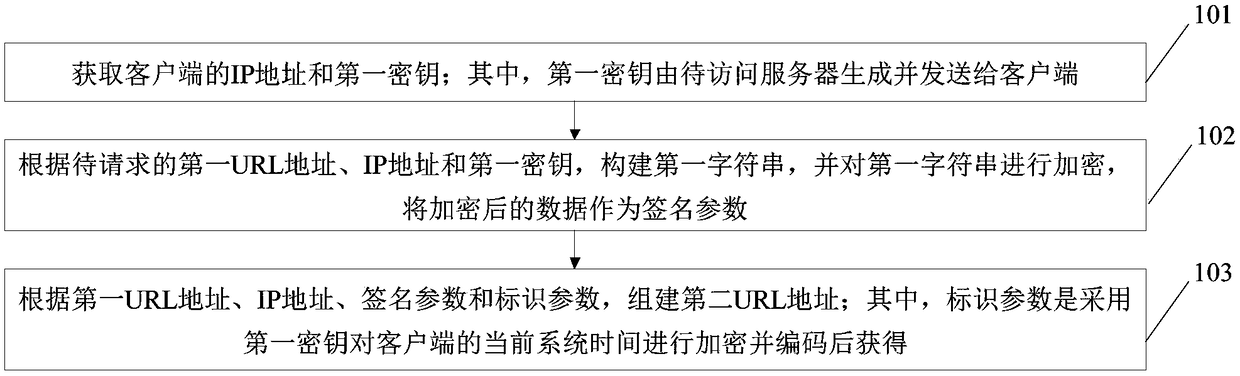
[0047] see figure 1 , is a flow diagram of an embodiment of a method for establishing a live link address provided by the present invention, the method includes steps 101 to 103, and each step is specifically as follows:
[0048] Step 101: Obtain the IP address of the client and a first key; wherein, the first key is generated by the server to be accessed and sent to the client.
[0049] In this embodiment, the first key is generated by the server to be accessed using a symmetric encryption algorithm and sent to the client. The first key may be generated using symmetric encryption and sent to the client in a secure manner in advance. Wherein, the symmetric encryption algorithm can adopt any one of DES, 3DES, Blowfish, IDEA, RC4, RC5, RC6 and AES, and the symmetric encryption algorithm is not a limitation of the present invention. Alternatively, an asymmetric encryption method is used to generate the public key, and the server sends the public key to the client for storage. Th...
Embodiment 2
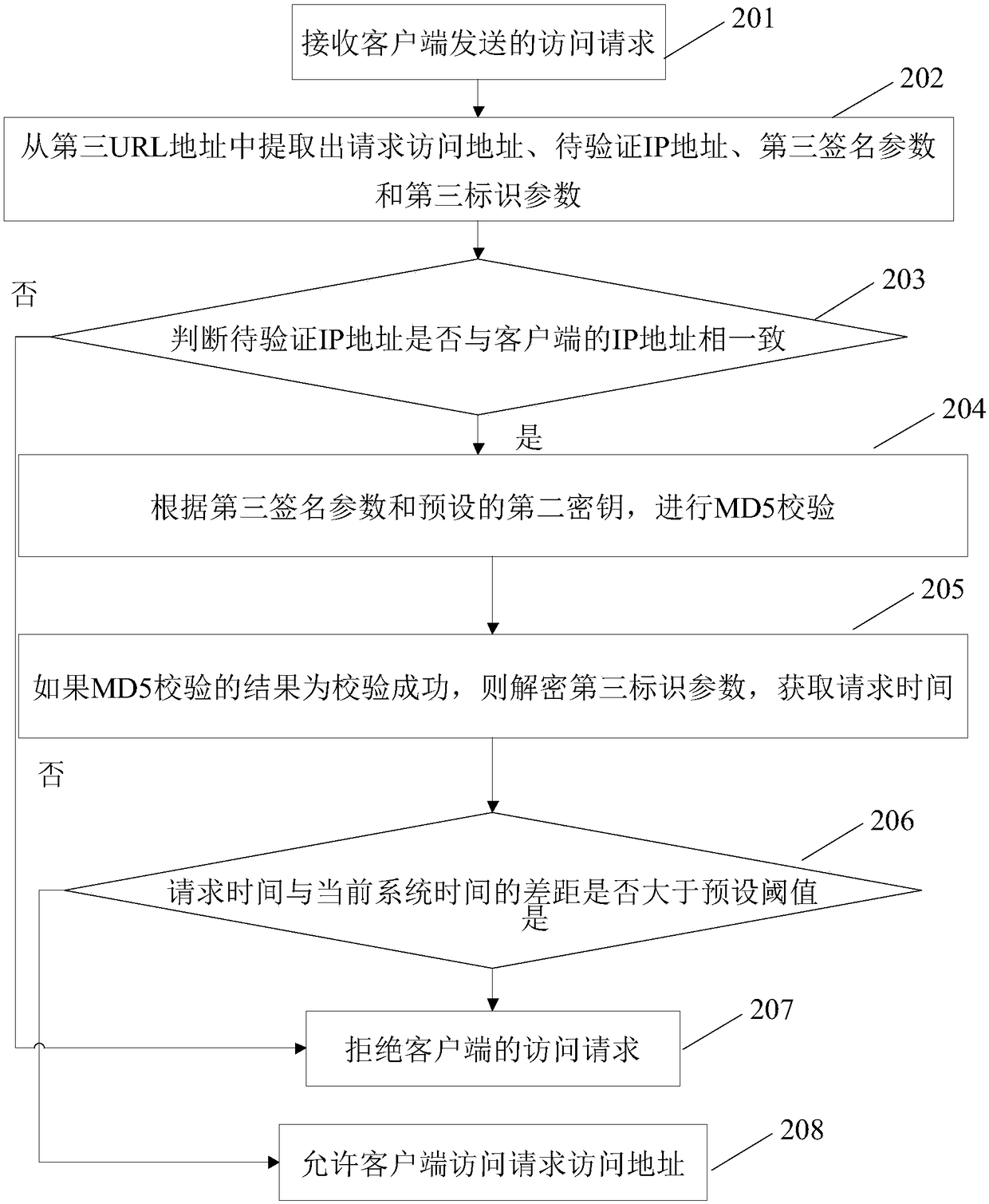
[0082] see figure 2 , figure 2 It is a schematic flowchart of an embodiment of the method for verifying the live link address provided by the present invention. like figure 2 As shown, the method includes steps 201 to 203:
[0083] Step 201: Receive an access request sent by a client.
[0084] In this embodiment, the access request includes the third URL address formed by the method for forming a live link address described in Embodiment 1.
[0085] Step 202: extract the requested access address, the IP address to be verified, the third signature parameter and the third identification parameter from the third URL address.
[0086] Step 203: Judging whether the IP address to be verified is consistent with the IP address of the client, if yes, execute step 204, otherwise, execute step 207.
[0087] Step 204: Perform MD5 verification according to the third signature parameter and the preset second key.
[0088] In this embodiment, step 204 specifically includes: after se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com