Identity authentication method and device, agent server and storage medium
A technology of identity authentication and proxy service, applied in the data processing field of master-slave architecture, it can solve the problems of no verification function, illegal verification, no verification or storage information, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
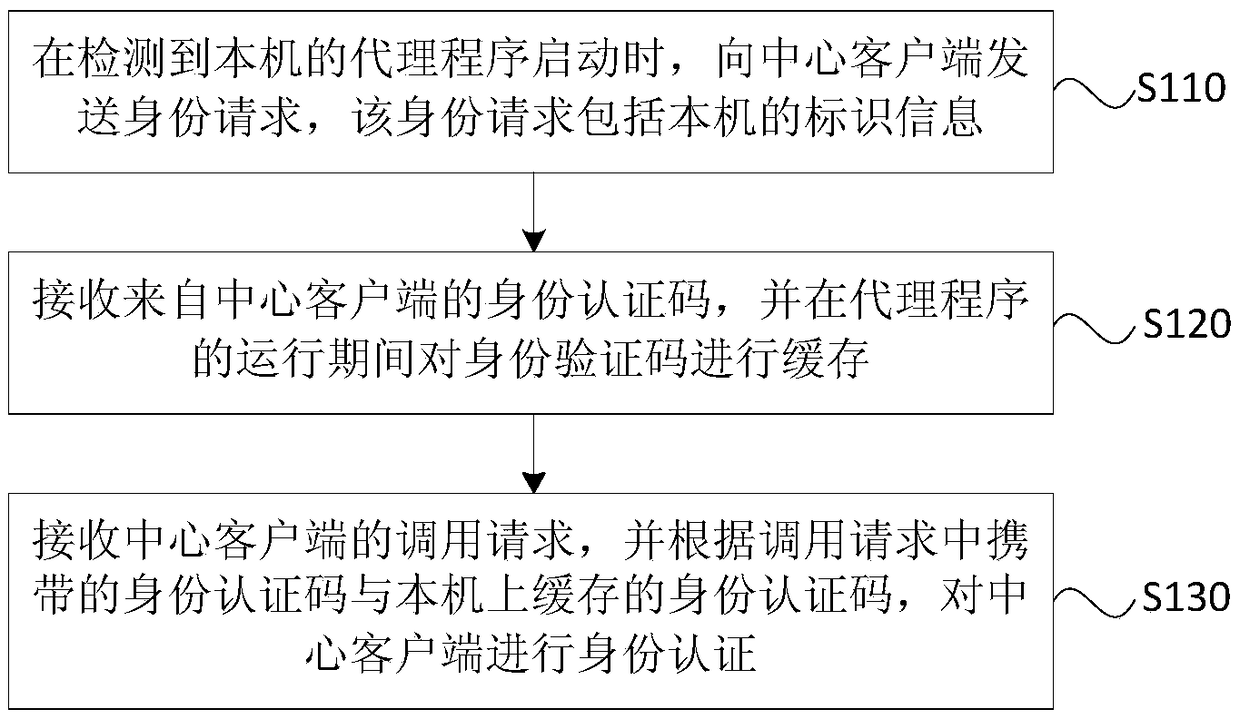
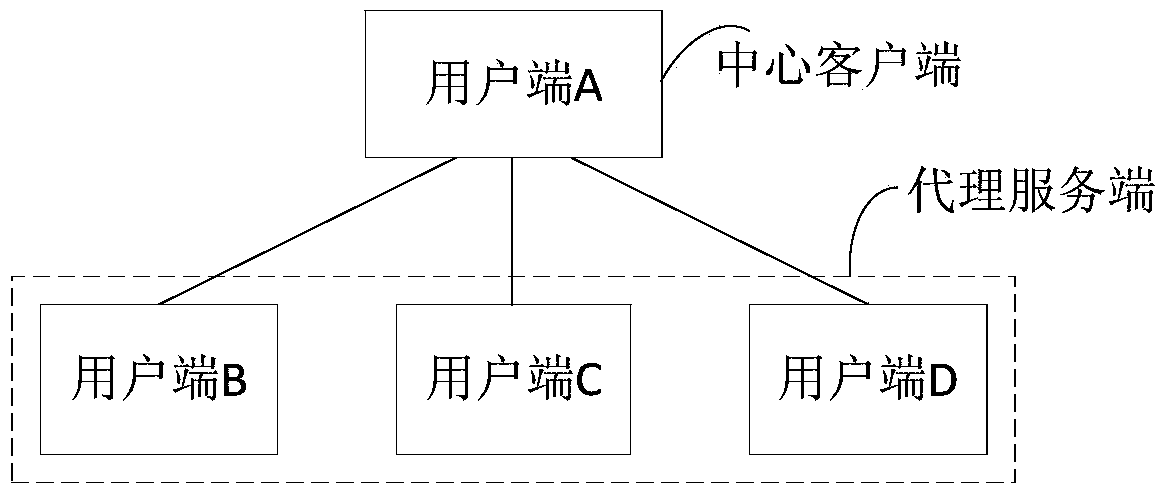
[0037] Figure 1A It is a flow chart of an identity authentication method provided by Embodiment 1 of the present invention. This embodiment is applicable to applications such as unified monitoring and deployment of user equipment through a single central client-multiple proxy server mode. An identity authentication method provided in this embodiment can be executed by an identity authentication device provided in an embodiment of the present invention. The device can be realized by means of software and / or hardware, and integrated in the proxy server executing the method. In this embodiment, the proxy server executing the method may be any terminal that requires unified monitoring and deployment, such as a tablet computer, a desktop computer, and a notebook. Specifically, refer to Figure 1A , the method may include the following steps:
[0038] S110, when it is detected that the agent program of the local machine starts, an identity request is sent to the central client, whe...
Embodiment 2
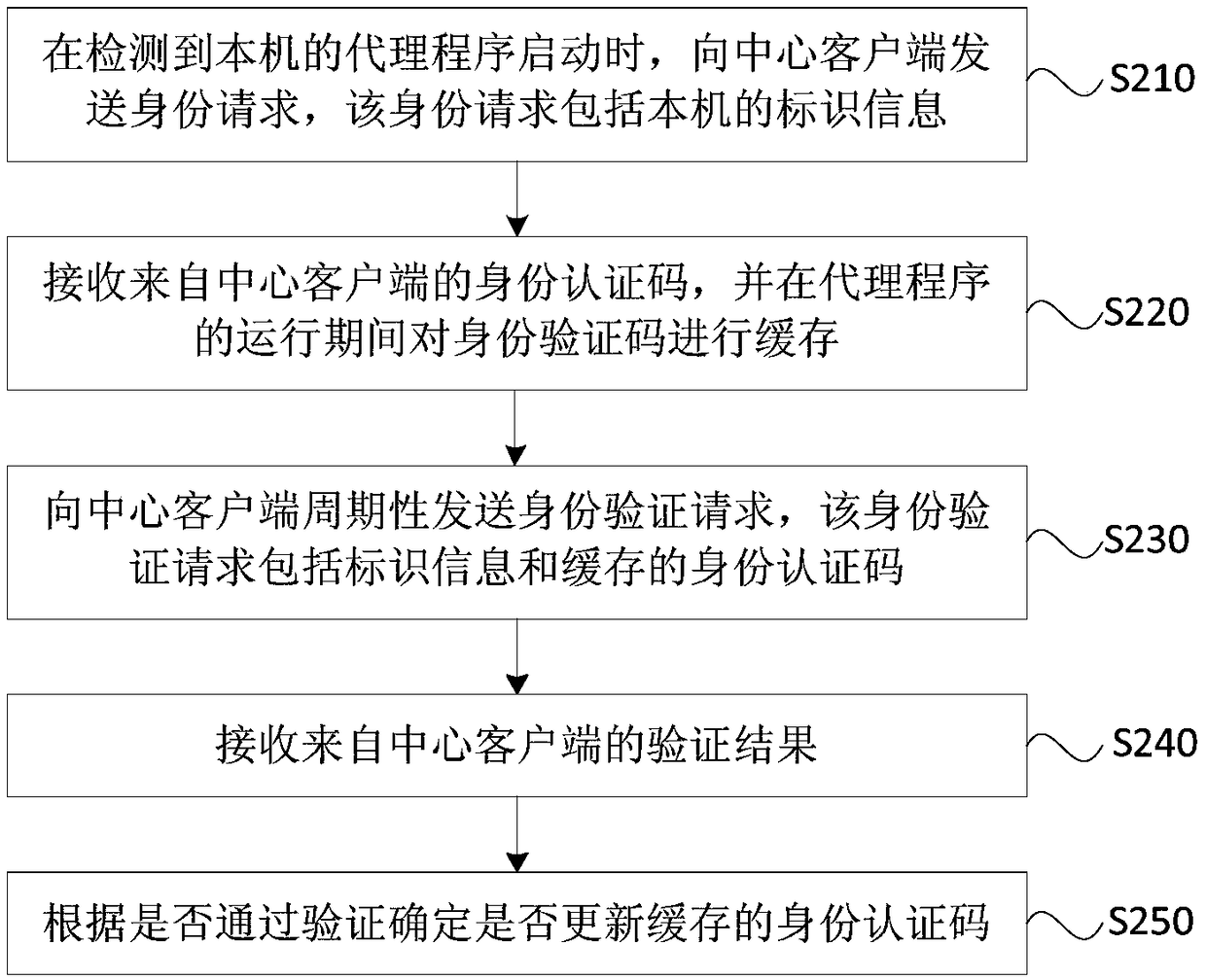
[0054] Figure 2A It is a flow chart of an identity authentication method provided by Embodiment 2 of the present invention. This embodiment is optimized on the basis of the foregoing embodiments. Since the identity authentication code cached on the central client and proxy server is only valid at runtime, if the central client is closed or restarted, the identity authentication code on it will be automatically destroyed, and in order to maintain the identity of the central client and proxy server The consistency of the authentication code ensures data security. At this time, the identity authentication code cached by the proxy server needs to be regenerated by the central client to update the cache. Specifically, such as Figure 2A As shown, the following steps may be included in this embodiment:
[0055] S210, when it is detected that the agent program of the local machine starts, an identity request is sent to the central client, where the identity request includes the id...
Embodiment 3
[0075] Figure 3A It is a flow chart of an identity authentication method provided by Embodiment 3 of the present invention. This embodiment is based on the above-mentioned embodiments, an interactive process for identity authentication between the central client and the proxy server. The specific interactive process is as follows: Figure 3B shown. refer to Figure 3A , the method of this embodiment may specifically include the following steps:
[0076] S310, when the proxy server detects that the proxy program is started, it sends an identity request to the central client, where the identity request includes identification information of the proxy server.
[0077] S311. The central client receives the identity request sent by the proxy server, generates an identity authentication code of the proxy server according to the identification information, and sends it to the proxy server.
[0078] Optionally, when the central client receives the identity request sent by the pro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com