Anti-quantum-computing key negotiation method based on asymmetric key pools
A technology of key agreement and quantum computing, which is applied in the field of key exchange algorithms, can solve the problems that asymmetric key encryption algorithms are no longer safe and asymmetric keys are vulnerable
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
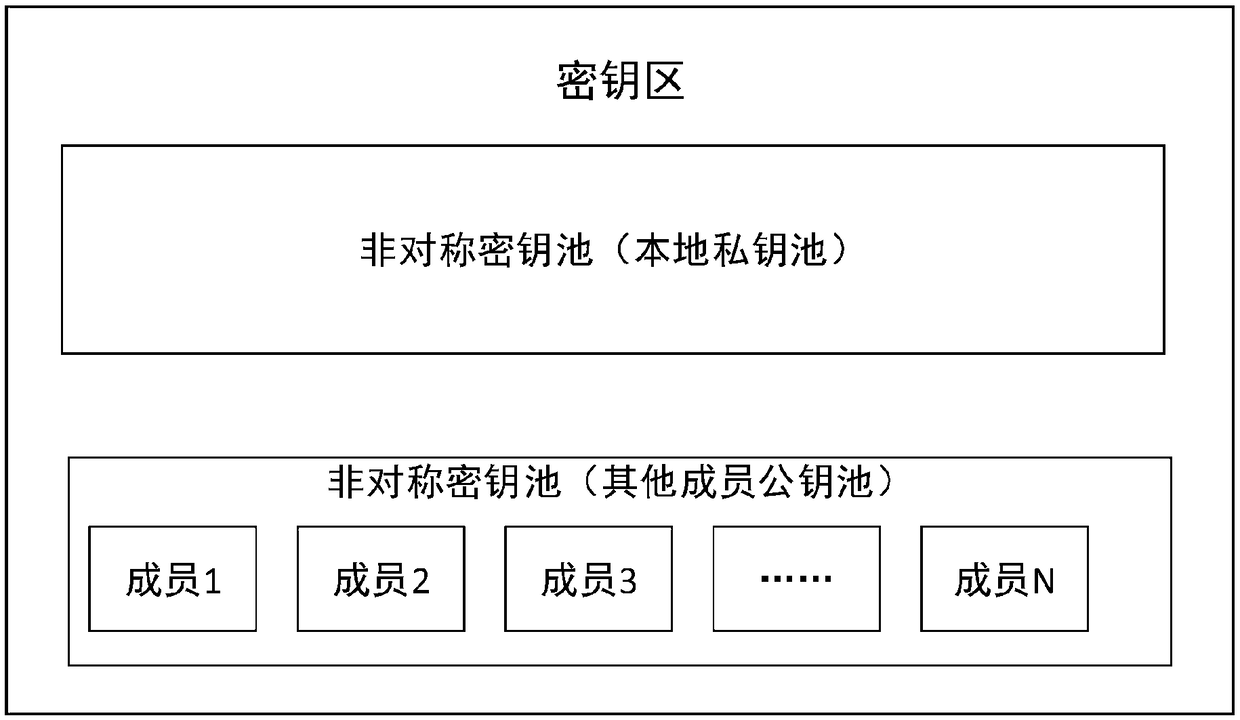
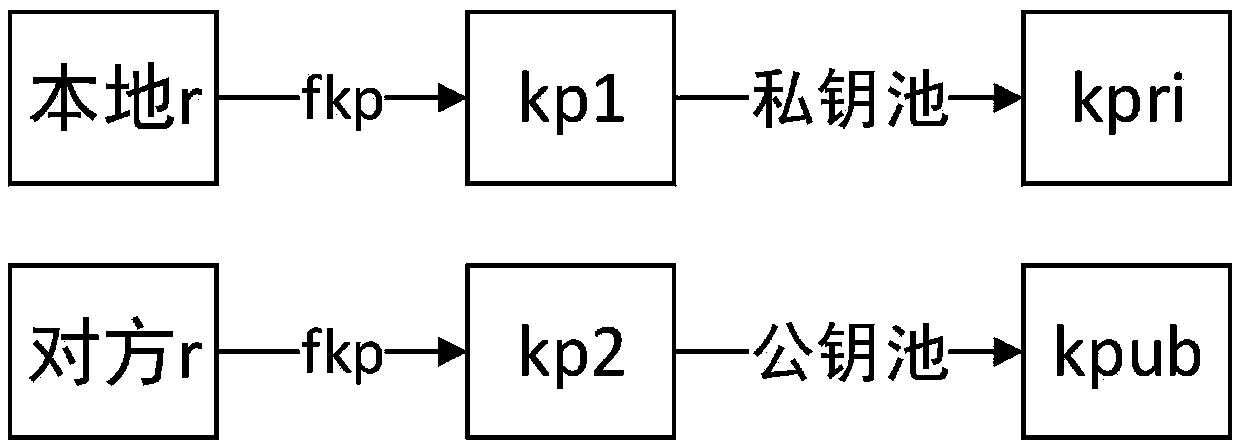
[0034] When the key card is recharging the key pool, the key management server will assign a group identity to the key card and give it an ID within the group. The key fob will be written into its own private key key pool and the public key key pools of other groups within the group. When the key management server establishes a group of an asymmetric key pool system, it will generate a corresponding number of private key key pools according to the number of members, and at the same time generate a public key key pool corresponding to the private key key pool one-to-one . The private key key pool is composed of true random numbers of a specified length. The public key key pool is composed of public key data, corresponding to the private key in the corresponding private key key pool.
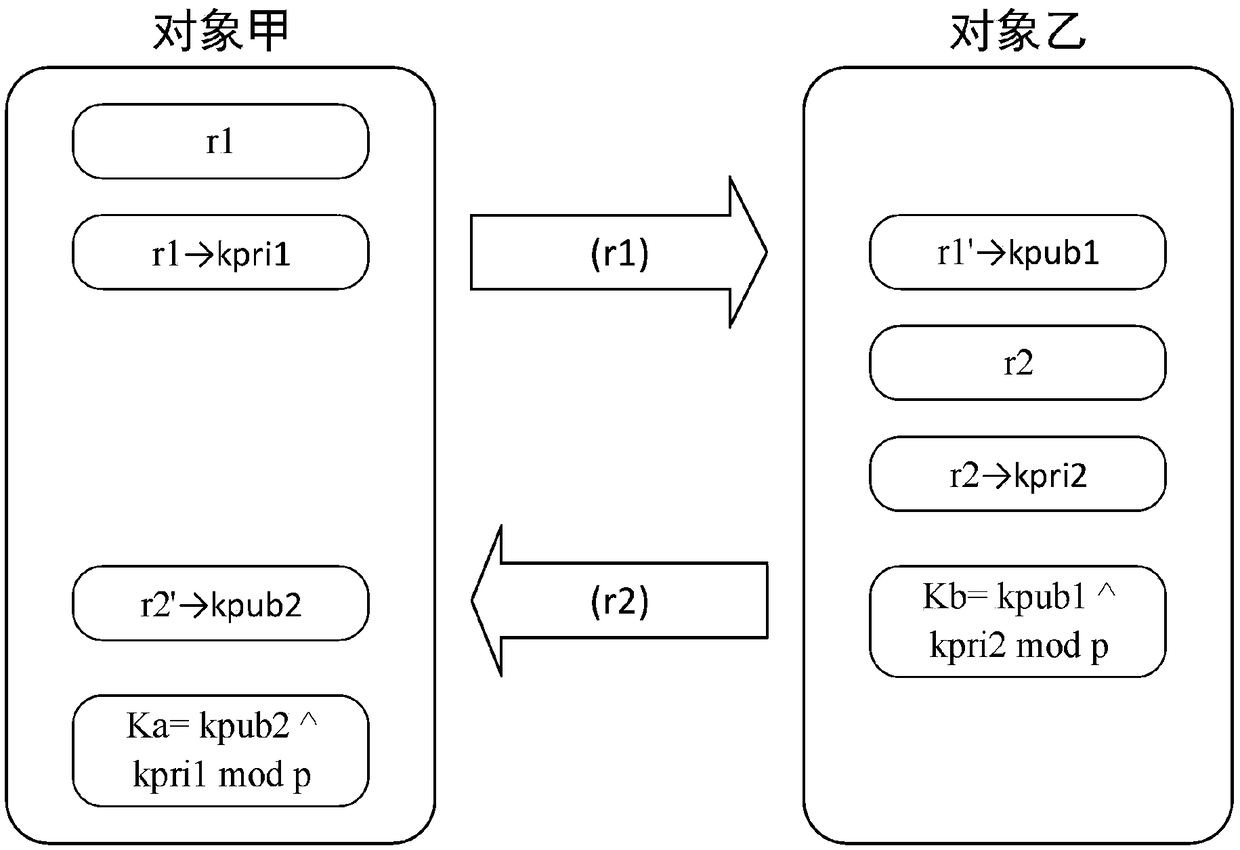
[0035] The method of generating the public key is the calculation method in the DH key exchange algorithm. The key management server defines a large prime number p and a number g, and g is the ...
Embodiment 2
[0050] When the key card is recharging the key pool, the key management server will assign a group identity to the key card and give it an ID within the group. The key fob will be written into its own private key key pool and the public key key pools of other groups within the group. When the key management server establishes a group of an asymmetric key pool system, it will generate a corresponding number of private key key pools according to the number of members, and at the same time generate a public key key pool corresponding to the private key key pool one-to-one . The private key key pool is composed of true random numbers of a specified length. The public key key pool is composed of public key data, corresponding to the private key in the corresponding private key key pool.
[0051] The method of generating the public key is the calculation method in the ECDH key exchange algorithm. The key management server definition defines a prime number p > 3 and chooses two no...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com