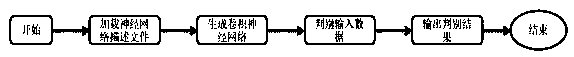Method for identifying network abnormal behavior based on deep neural network
A deep neural network and network anomaly technology, applied in the field of identification, abnormal network behavior recognition based on deep neural network, can solve problems such as failure to find abnormal behavior, small traffic, difficult to locate, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
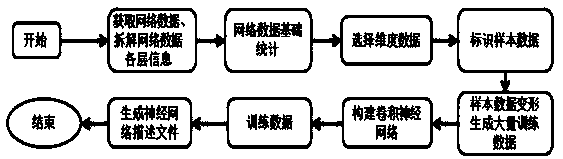
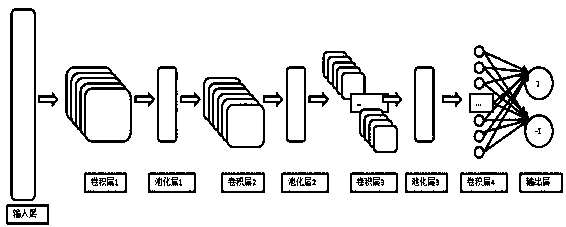
[0109] Example 1: see figure 1 , in actual implementation, a distributed deployment method is adopted (distributed deployment is conducive to accelerating data training), the operating system used is CentOS6.9 (kernel is 2.6.32-696), Intel 64-bit hardware architecture is adopted, network card Using Intel e1000e, the network packet capture adopts the Netmap high-speed network packet acquisition architecture, as follows,
[0110] A method for identifying network abnormal behavior based on a deep neural network, said method comprising the following steps:
[0111] Step 1: Standardize the information of each layer and the session information mark of the network-related data packets (only analyze the network based on the Ethernet type);
[0112] Step 2: Filter the relevant network connection session data that needs to be processed;
[0113] Step 3: Perform feature pre-extraction on various protocol data;
[0114] Step 4: Normalize the above characteristic data;
[0115] Step 5:...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com