Data protection and data deprotection method, terminal, and computer readable storage medium
A data protection and data technology, applied in the information field, can solve the problems of low data security and high resource consumption, and achieve the effect of low computational complexity, optimized configuration, and simple process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
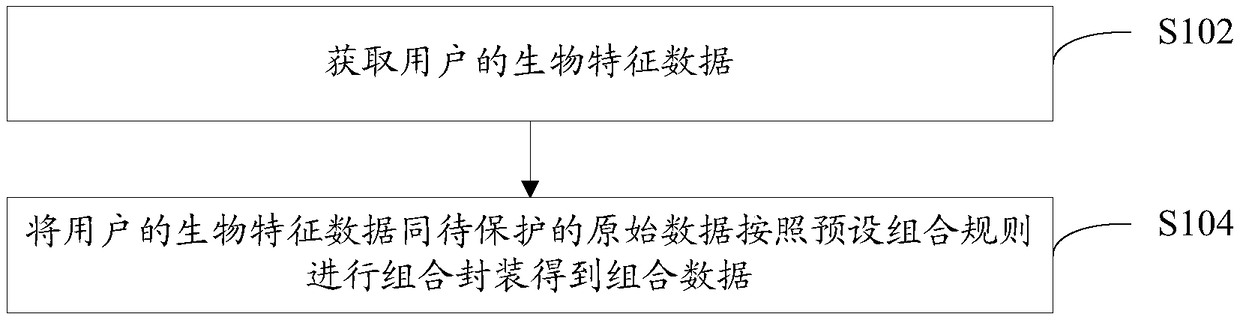
[0029] In order to solve the problem of low data security and high resource consumption in the prior art when data is encrypted by increasing the complexity of the encryption algorithm or using multiple encryption algorithms, this embodiment provides a data protection method. See figure 1 :
[0030] S102. Obtain biometric data of the user.
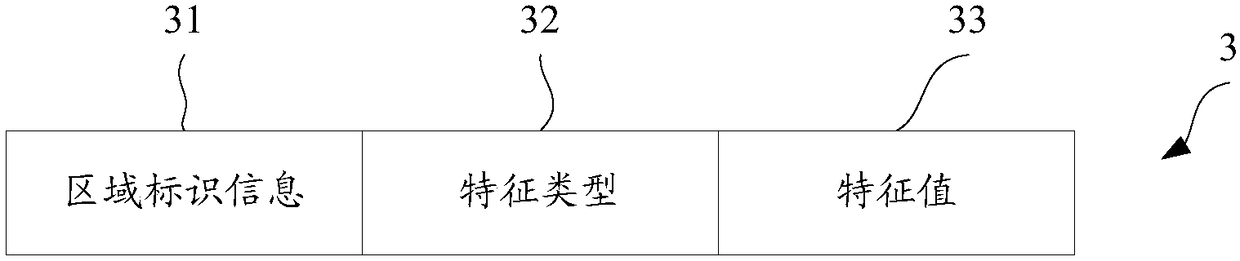
[0031] The biological characteristics described in this embodiment can be divided into two types. The first type is the inherent physiological characteristics of the human body, including palmprint features, iris features, facial features, etc., wherein the palm prints on the surface of the palm between the wrist and the fingers Various lines, therefore, palm prints include the fingerprints on the fingertips of the palm and the lines in the middle of the palm. The second type of biological characteristics is the behavioral characteristics of the human body, including voiceprint characteristics, gait characteristics, handwriting character...
Embodiment 2
[0058] This embodiment will continue to introduce the data protection method on the basis of the foregoing embodiments, please refer to Figure 6 :
[0059] S602. Acquire biometric data of the user.
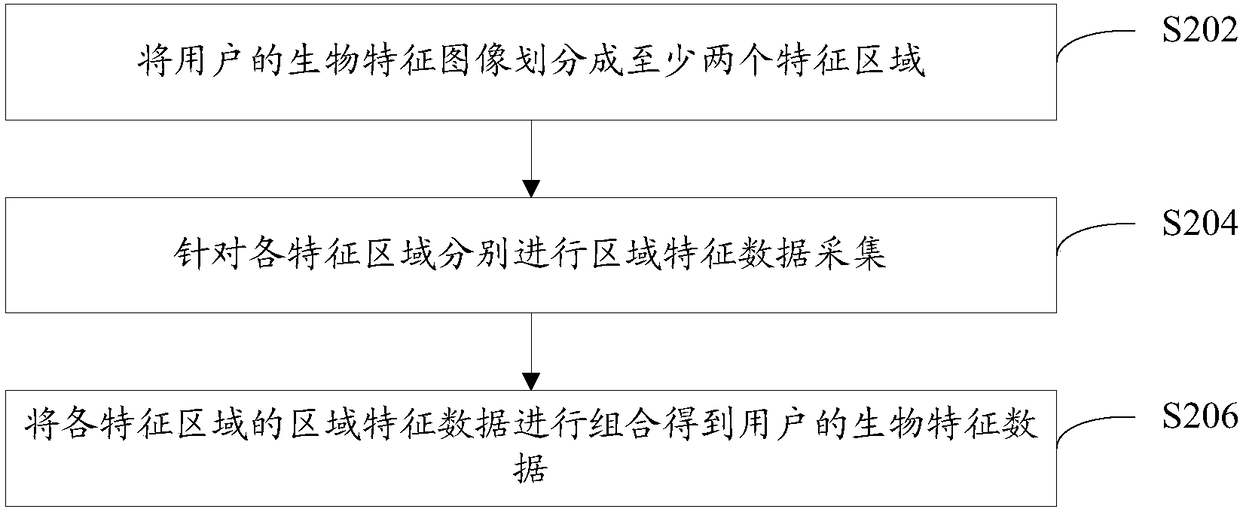
[0060] In the first embodiment, it has been introduced that for a biometric feature, the regional feature data collection process is performed in regions from the biometric image corresponding to the biometric feature. However, considering that human beings have more than one biological feature, it may be considered to combine two or more biological features to obtain biological feature data including multiple features. In this embodiment, a scheme for collecting image feature data for two or more biological feature images will be introduced.
[0061] Assuming that the biometric features in this embodiment include the user's palmprint feature and the user's iris feature, for these two biometric features, image acquisition can be performed separately to obtain the corresponding ...
Embodiment 3
[0077] This embodiment provides a computer-readable storage medium, and the computer-readable storage medium stores one or more computer programs that can be read, compiled, or executed by the memory, including a data protection program, which can be used for The processor executes so as to realize the data protection method provided in the first or second embodiment. Alternatively, the above-mentioned computer-readable storage medium may store a data unprotection program, and the data unprotection program can be executed by a processor so as to implement the data unprotection method provided in the first or second embodiment. Certainly, in an example of this embodiment, the computer-readable storage medium may simultaneously store a data protection program and a data unprotection program.
[0078] At the same time, this embodiment also provides a terminal, please refer to Figure 9 : the terminal 90 includes a processor 91, a memory 92, and a communication bus 93 for connect...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com