The invention relates to a transaction security control method and a system based on subject portrait
A security control and transaction technology, applied in the field of transaction security, to achieve good real-time performance, fast analysis, and strong recognition capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
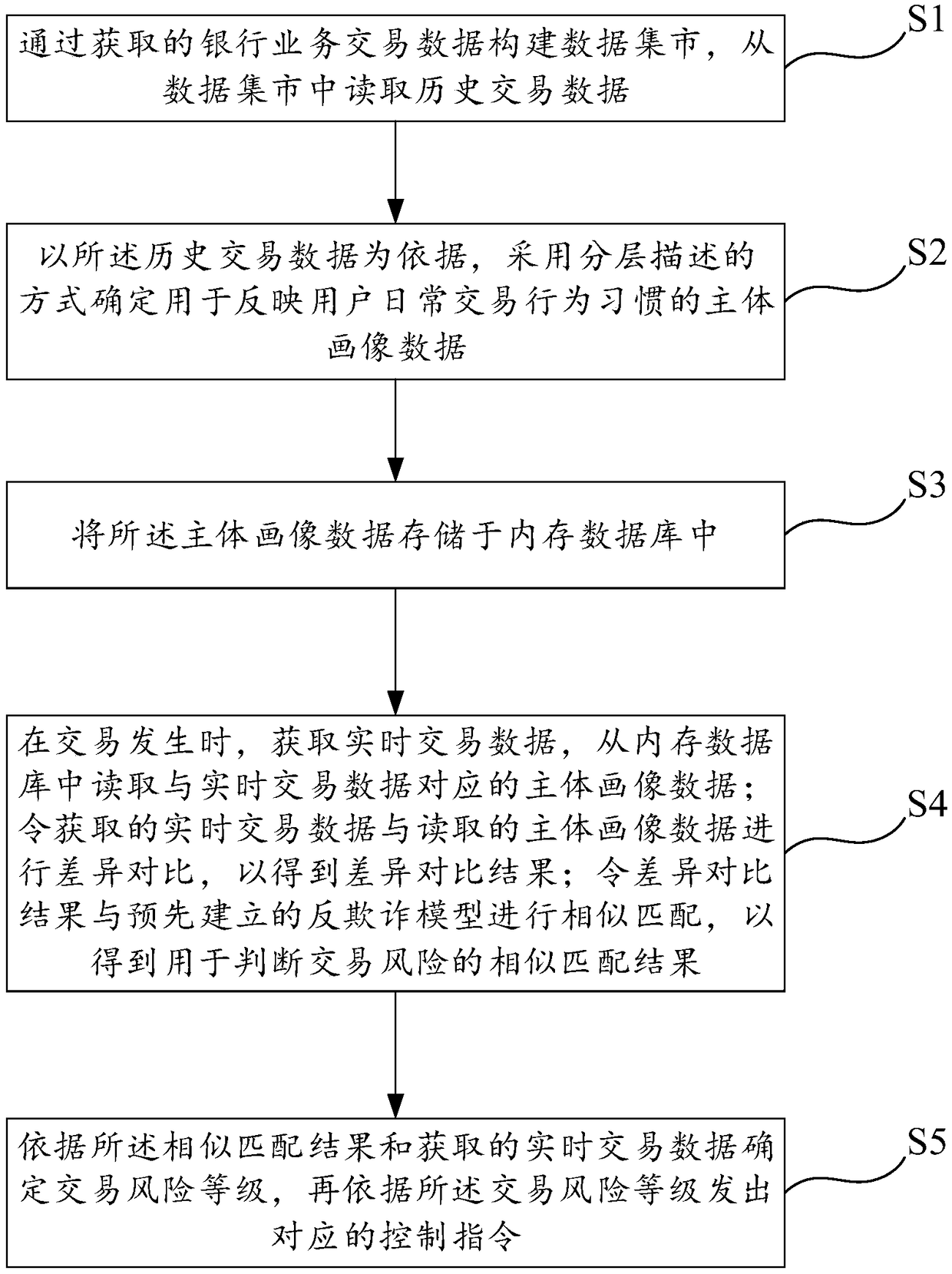
[0065] Such as figure 1 As shown, this embodiment specifically discloses a transaction security control method based on subject portraits, so that transaction security can be effectively protected under emerging transaction methods and transaction channels, and the occurrence of fraudulent behavior can be reduced or even avoided. Specifically, the transaction The security control method includes the following steps.
[0066] Step S1, build a data mart through the acquired banking transaction data, such as analysis of bank user and account data and ETL (extract, transform, load) to build a data mart , is used to calculate the historical behavior of the subject. The time span of the subject data is often long, and more historical data is required to be accumulated. After the data mart is built, the historical transaction data is read from the data mart.
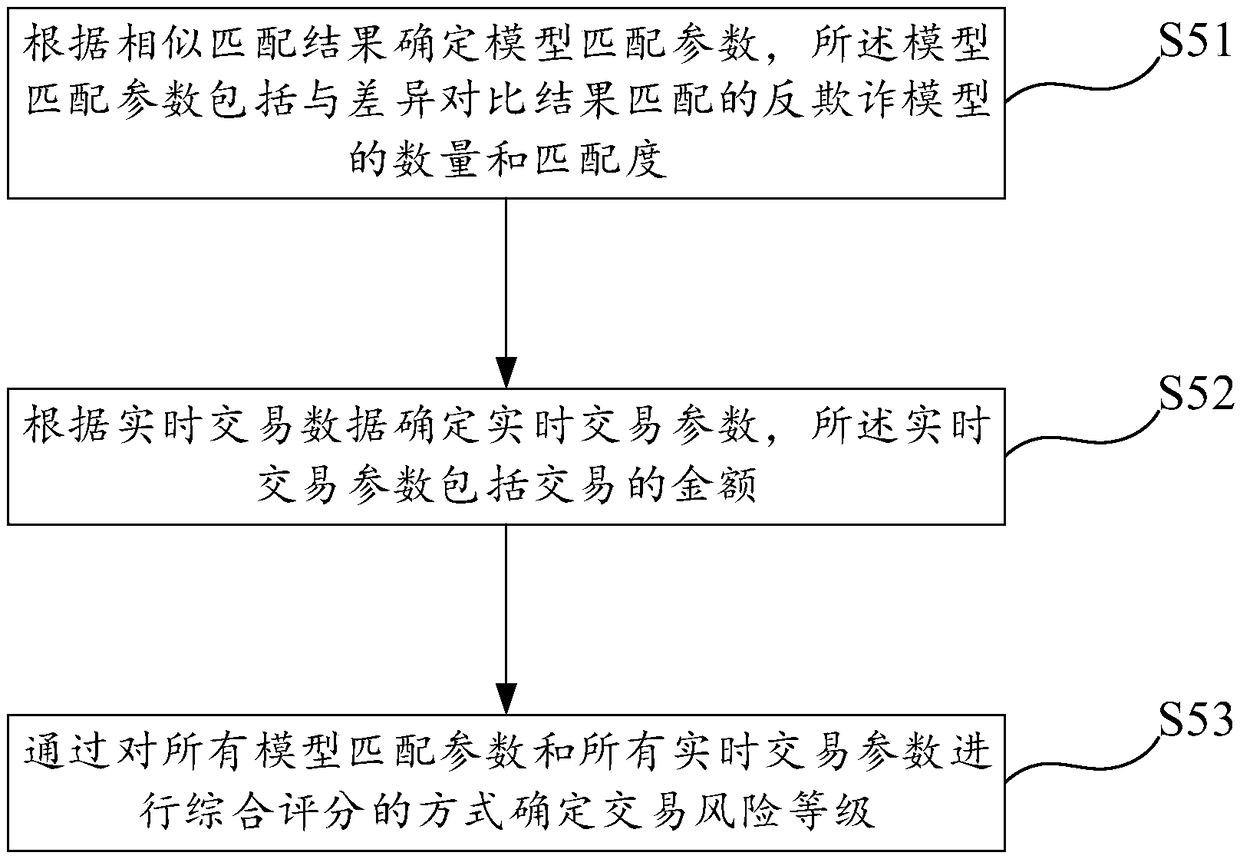
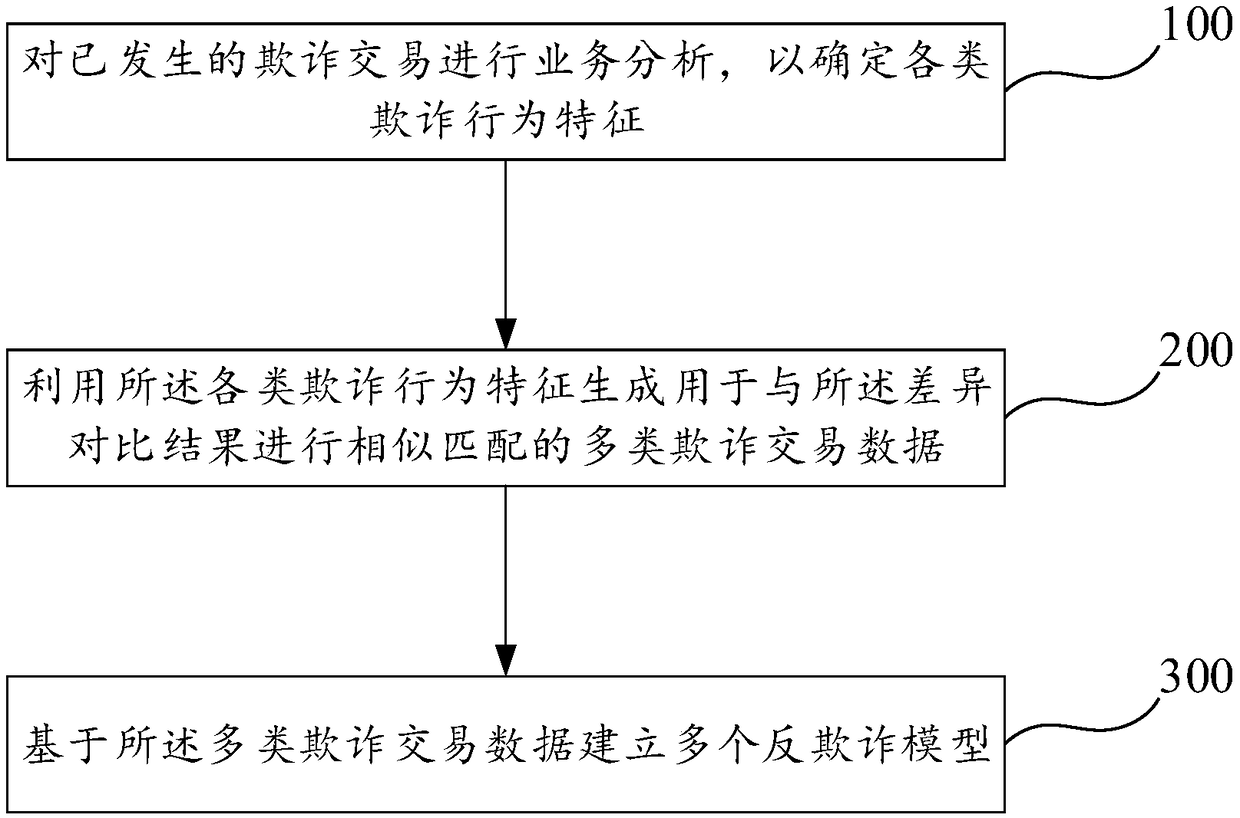
[0067] Step S2, based on the read historical transaction data, determine the subject portrait data to reflect the user's dai...
Embodiment 2
[0094] Based on the same inventive concept as Embodiment 1, this embodiment specifically discloses a transaction security control system based on subject portraits, which can effectively protect transaction security under emerging transaction methods and transaction channels, and reduce or even avoid the occurrence of fraudulent behavior ,Such as Figure 5 As shown, the transaction security control system includes a data mart building module, a subject portrait generation module, an in-memory database, a matching result calculation module, and a transaction risk decision-making module.
[0095] The data mart building module is used to construct a data mart through the acquired banking transaction data, which is used to calculate the historical behavior of the subject, and the data mart is used to provide historical transaction data.
[0096] The subject portrait generation module is used to determine the subject portrait data to reflect the user's daily transaction behavior ha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com