Quantum key wireless-distribution method and system used for secure communication of terminal equipment
A quantum key and terminal equipment technology, applied in the field of quantum communication, can solve the problems of low security level of wireless distribution of quantum keys, security dependence of wired distribution of quantum keys, complex project deployment, etc., to achieve simple distribution and easy deployment Convenience, enhanced safety and security level effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
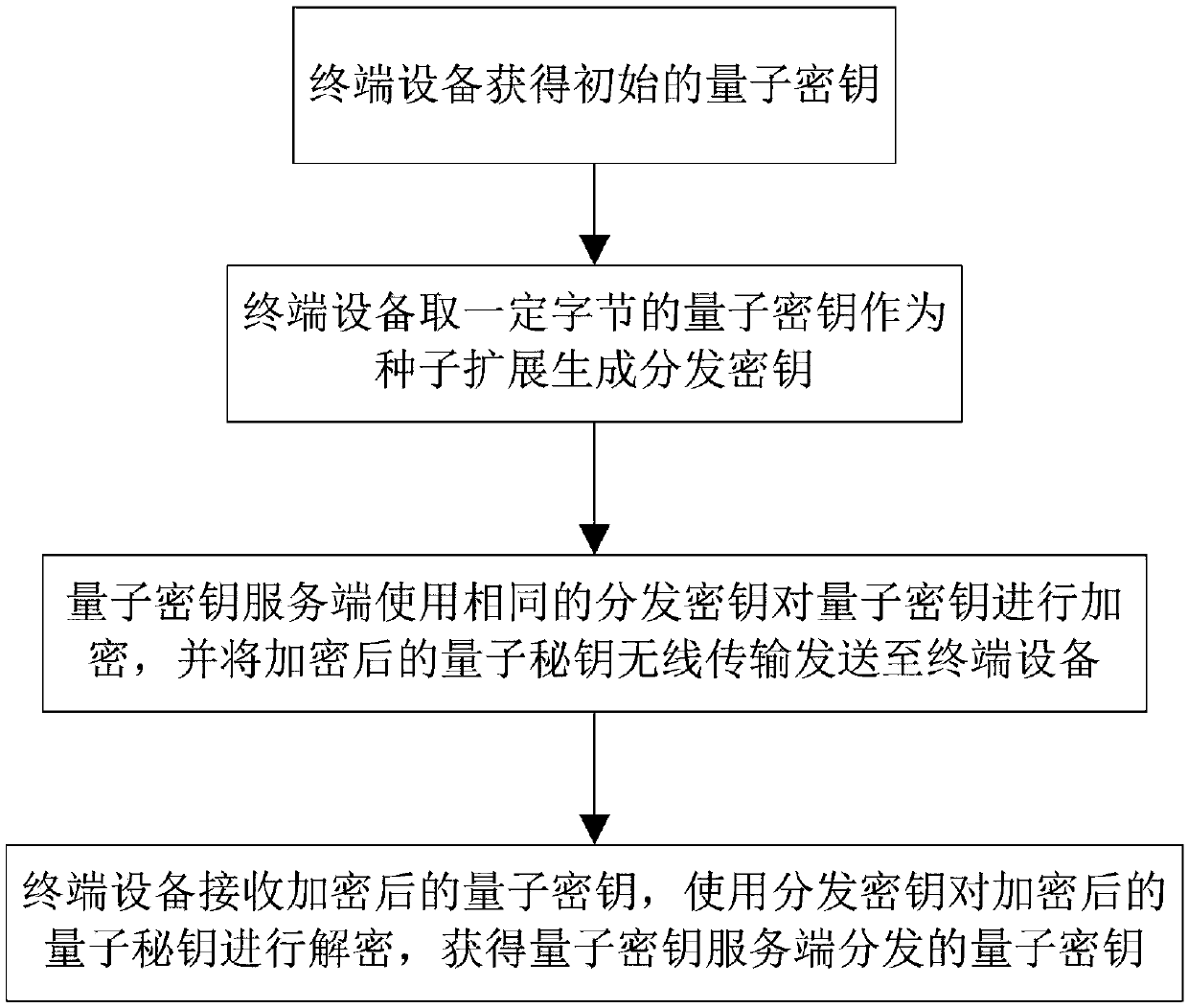
[0050] This embodiment discloses a quantum key wireless distribution method, and the quantum key obtained through distribution is used for secure communication of services by terminal equipment.
[0051] The main hardware devices involved in wireless quantum key distribution in this embodiment include:
[0052] (1) Terminal equipment
[0053] Terminal devices can be mobile terminals such as smartphones, tablet computers, laptops, PDAs (Personal Digital Assistants), or other terminal devices such as set-top boxes and PCs, which are the requesting and receiving ends of quantum key distribution.
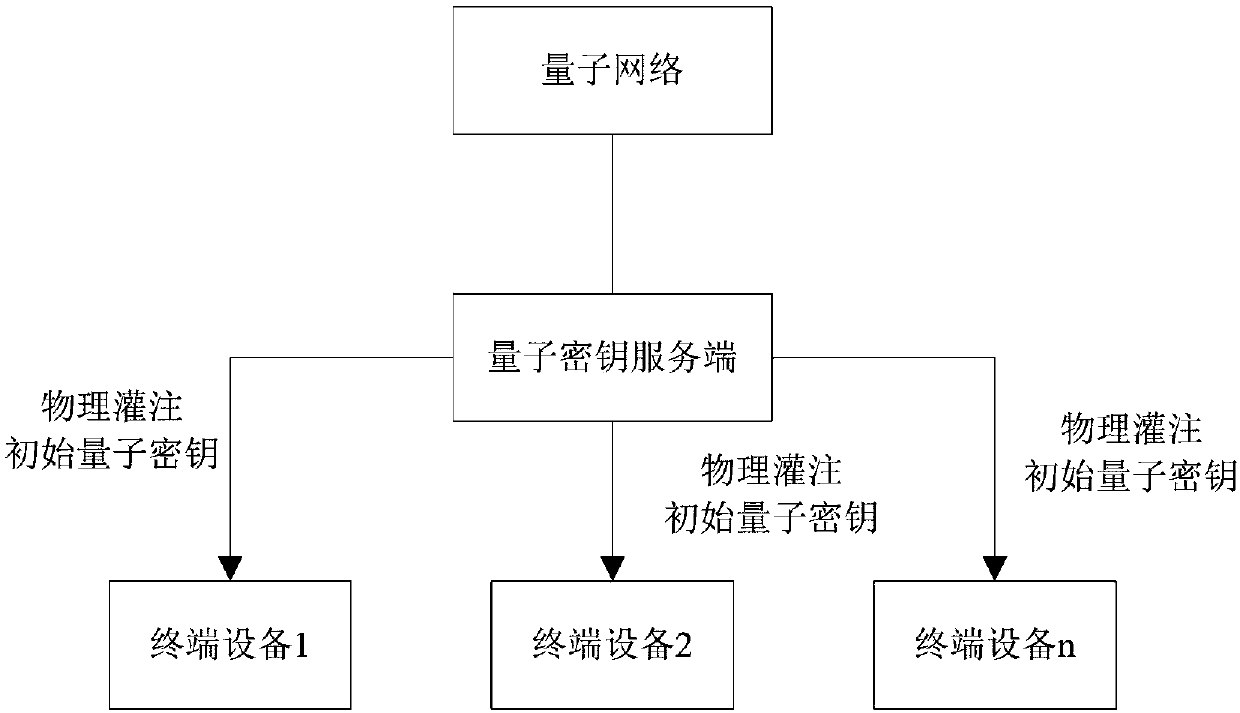
[0054] The terminal device is equipped with storage devices and common data interfaces such as USB and Type-C. The terminal device pours the initial quantum key into the internal storage device through common data interfaces such as USB and Type-C.
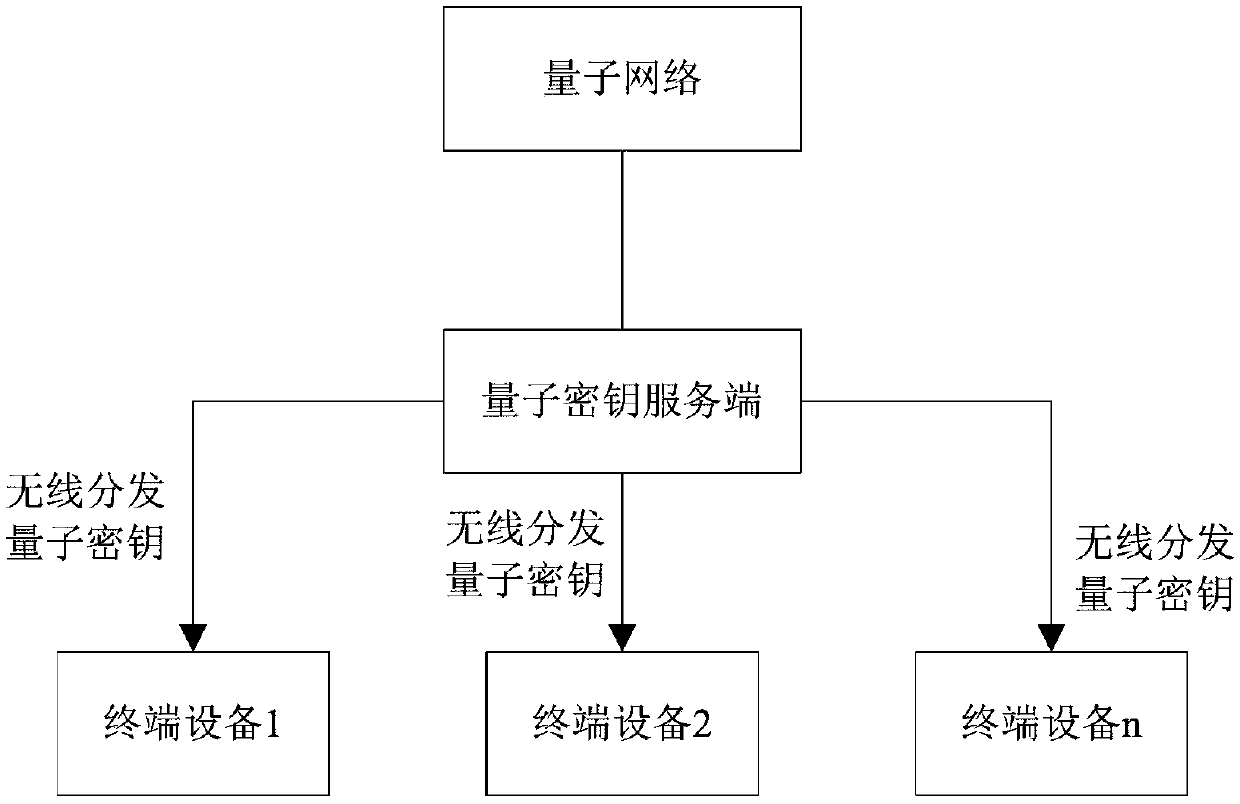
[0056] The quantum key server is the sender of quantum key distribution. The above-mentioned initial q...
Embodiment 2
[0092] This embodiment discloses a quantum key wireless distribution system for secure communication of terminal equipment, including a terminal equipment and a quantum key server.
[0093] Among them, the terminal device can be a mobile terminal such as a smart phone, a tablet computer, a notebook computer, a PDA (Personal Digital Assistant), or other terminal devices such as a set-top box and a PC, which are the requesting end and the receiving end of quantum key distribution.
[0094] The terminal device is equipped with storage devices and common data interfaces such as USB and Type-C. The terminal device pours the initial quantum key into the internal storage device through common data interfaces such as USB and Type-C.
[0095] The quantum key server is the sender of quantum key distribution. The above-mentioned initial quantum key is shared between the quantum key server and the authenticated terminal device. Wherein, the initial quantum key acquired by the terminal d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com