hard disk partition encryption method and system under a K-UX system
A technology of K-UX and hard disk partition, which is applied in the direction of program loading/starting, program control design, instrument, etc. It can solve the problems of low protection level of hard disk partition and high risk of data and file leakage in key partitions, and achieve flexible encryption methods, The effect of flexible authorization methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
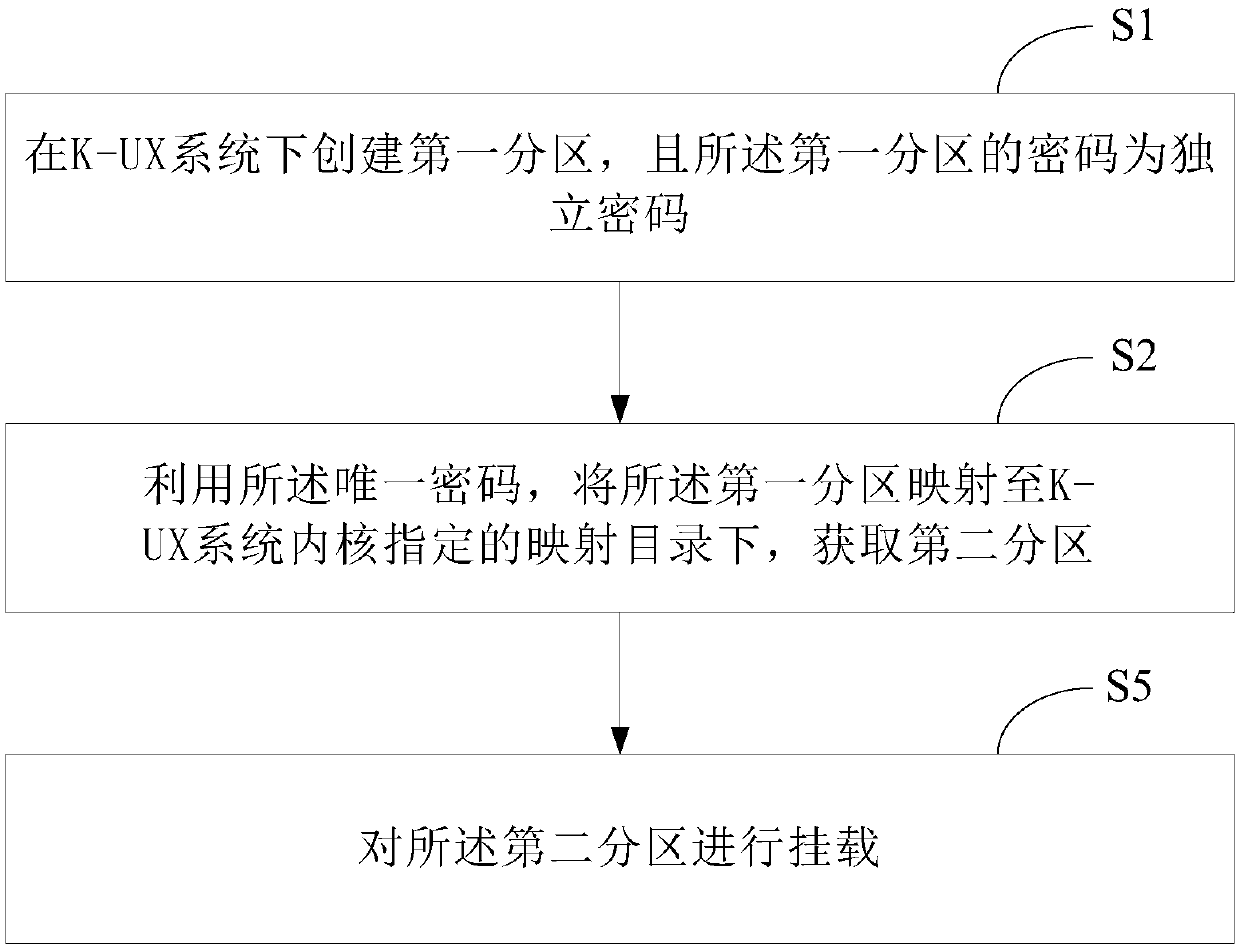
[0047] see figure 1 , figure 1 It is a schematic flowchart of a method for encrypting hard disk partitions under the K-UX system provided by the embodiment of the present application. Depend on figure 1 As can be seen, the method for hard disk partition encryption under the K-UX system in the present embodiment mainly includes the following processes:
[0048] S1: Create the first partition under the K-UX system, and the password of the first partition is an independent password.
[0049] Wherein, the first partition in this embodiment is an encrypted partition. Specifically, step S1 includes:
[0050] S11: Create a third partition under the K-UX system. Wherein, the third partition is the original blank partition.
[0051] S12: Encrypt the third partition to obtain the first partition.
[0052] It can be known from the above steps S11 and S12 that in this embodiment, a new partition is firstly created for the K-UX system, that is, the third partition, and is encrypted to...
Embodiment 2
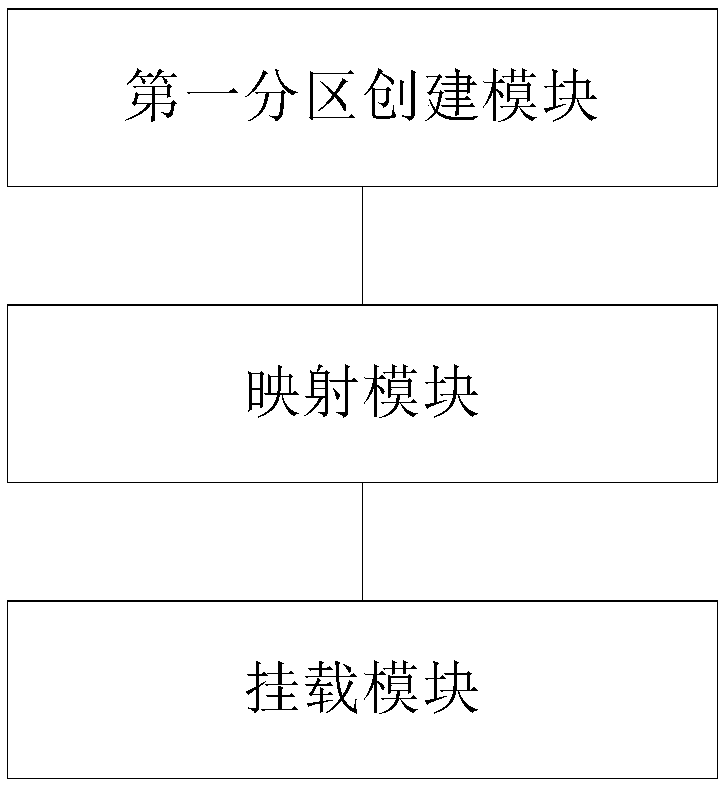
[0086] exist figure 1 On the basis of the illustrated embodiment see figure 2 , figure 2 It is a schematic structural diagram of a hard disk partition encryption system under the K-UX system provided by the embodiment of the present application. Depend on figure 2 It can be seen that the system mainly includes a first partition creation module, a mapping module and a mounting module. Wherein, the first partition creation module is used to create the first partition under the K-UX system, and the password of the first partition is an independent password, wherein, the first partition is an encrypted partition; the mapping module is used to utilize the independent password to convert the first The partition is mapped to the mapping directory specified by the K-UX system kernel to obtain the second partition, wherein the second partition is an encrypted partition after mapping; the mounting module is used to mount the second partition.
[0087] Further, the first partition...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com