Security authentication method based on MQTT, device and storage medium
A security authentication and electronic device technology, applied in the field of computer security, can solve the problems of attacking user equipment security authentication, communication network threats, etc., to ensure security and privacy, and improve security performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057]It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
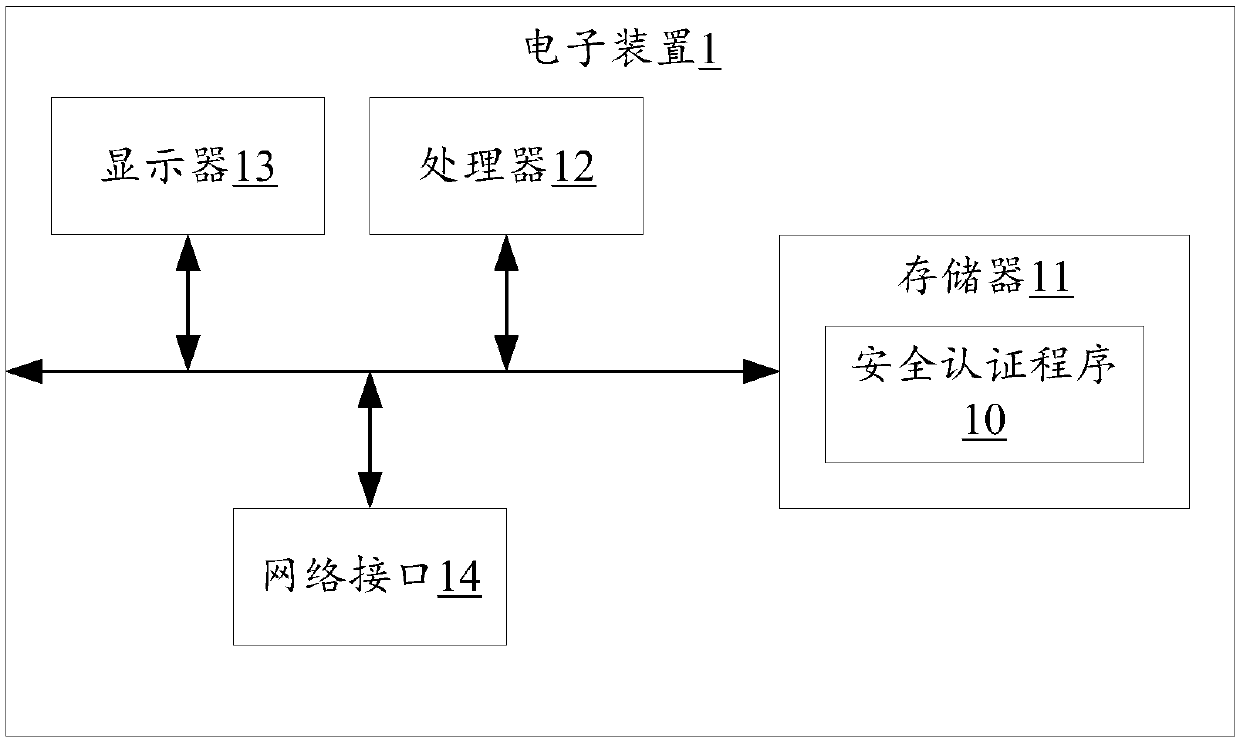
[0058] Such as figure 1 Shown is a schematic diagram of a preferred embodiment of the electronic device 1 of the present invention.
[0059] In this embodiment, the electronic device 1 may be a computing device such as a rack server, a blade server, a tower server, or a cabinet server, and the electronic device 1 may be an independent server, or may be composed of multiple servers server cluster.
[0060] The electronic device 1 includes but not limited to: a memory 11 , a processor 12 , a display 13 and a network interface 14 . The electronic device 1 is connected to the network through the network interface 14 to obtain raw data. Wherein, the network may be an intranet (Intranet), Internet (Internet), Global System of Mobile Communication (Global System of Mobilecommunication, GSM), Wideband Code Division Multiple...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com