A verifiable outsourcing computing method, client and cloud computing system for efficiently solving large-scale matrix determinants
A calculation method, determinant technology, applied in the field of cloud computing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
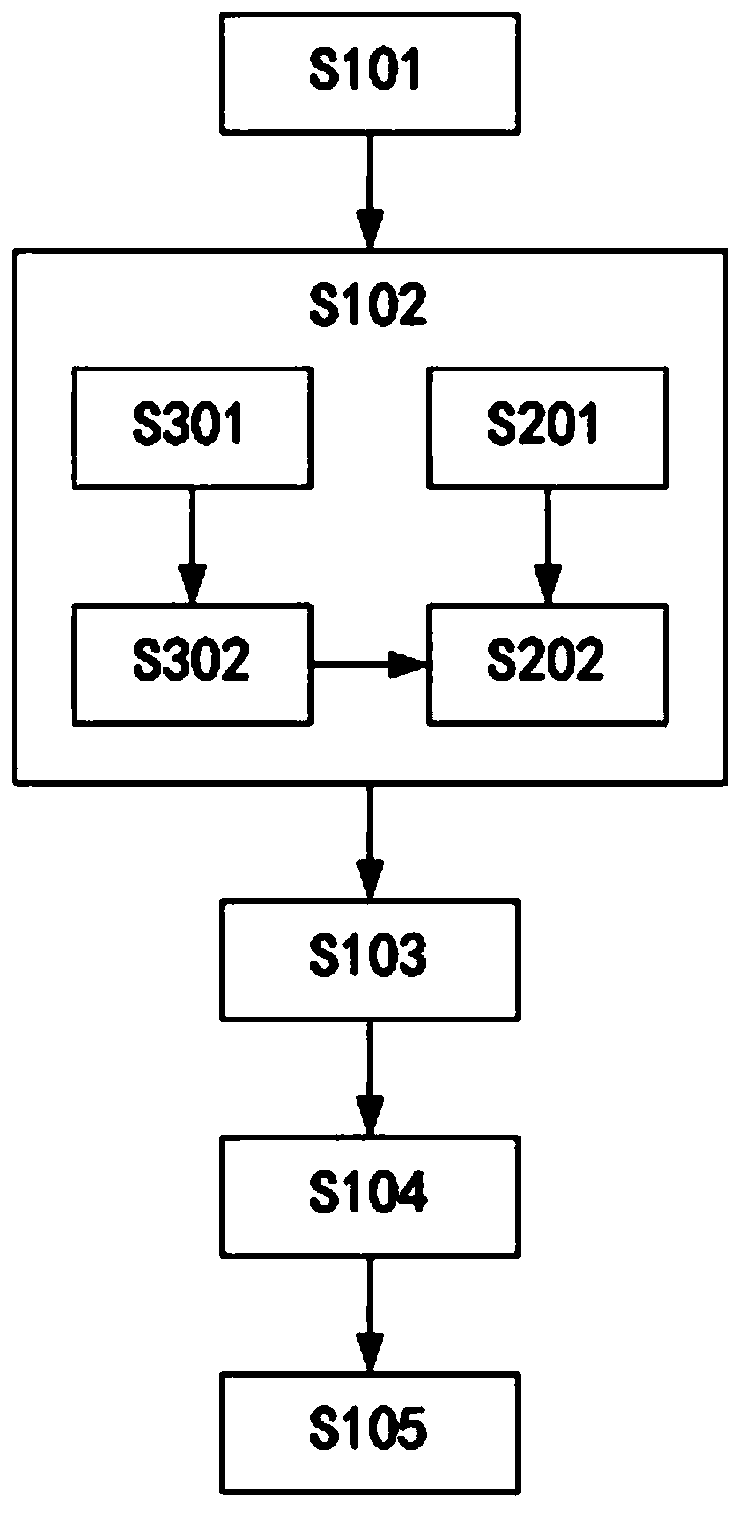
[0090] Such as figure 1 As shown, the verifiable outsourcing calculation method for efficiently solving the determinant of a large-scale matrix provided in this embodiment includes the following steps.
[0091] S101. Generate key matrix set {A 1 ,A 2 ,...,A x ,...,A ξ} and {B 1 ,B 2 ,...,B x ,...,B ξ}, where the key matrix A x and B x Respectively non-singular square matrix with n*n elements, key matrix A x The main diagonal elements or subdiagonal elements in are random positive integers, and the key matrix B x The main diagonal elements or subdiagonal elements in are random positive integers, and the key matrix A x The d-th column element and key matrix B in x The elements of row d in are random non-zero real numbers, key matrix A x and B x The other elements in are zero, n is a positive integer not less than 1000, ξ is a positive integer not less than 3, x is a positive integer not greater than ξ, and d is a random positive integer not greater than n.
[0092...
Embodiment 2
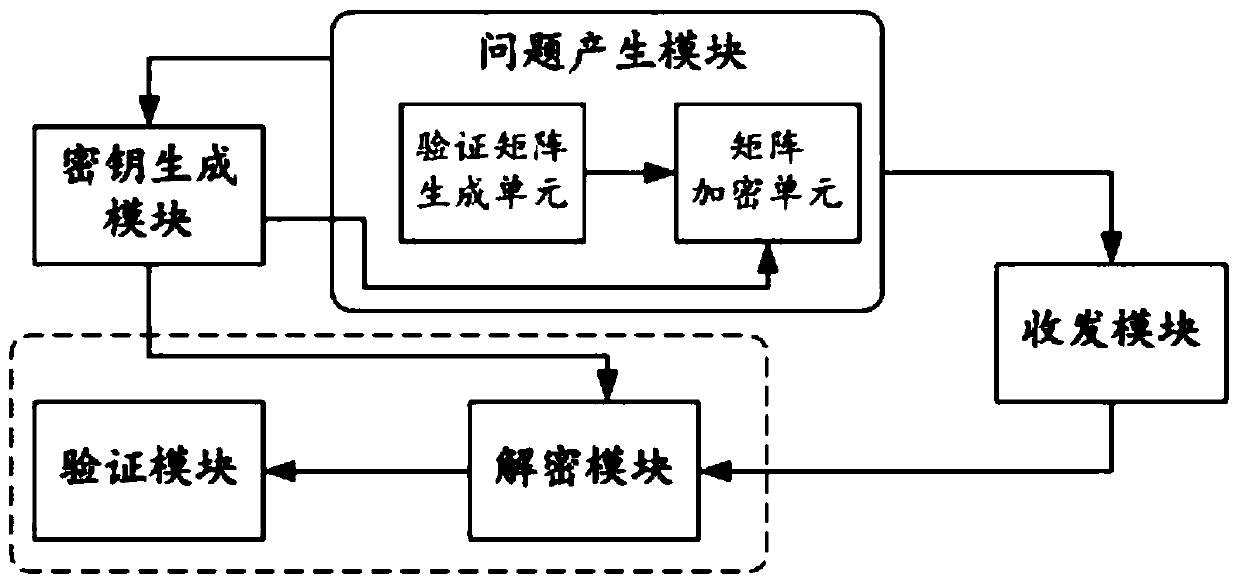
[0148] Such as figure 2 As shown, this embodiment provides a client that implements the first embodiment, including a key generation module, a question generation module, a transceiver module, a decryption module, and a verification module, wherein the question generation module includes a verification matrix generation unit and matrix encryption unit;
[0149] The key generation module is used to generate the key matrix set {A 1 ,A 2 ,...,A x ,...,A ξ} and {B 1 ,B 2 ,...,B x ,...,B ξ}, where the key matrix A x and B x Respectively non-singular square matrix with n*n elements, key matrix A x The main diagonal elements or subdiagonal elements in are random positive integers, and the key matrix B x The main diagonal elements or subdiagonal elements in are random positive integers, and the key matrix A x The d-th column element and key matrix B in x The elements of row d in are random non-zero real numbers, key matrix A x and B x The remaining elements in are zero...
Embodiment 3
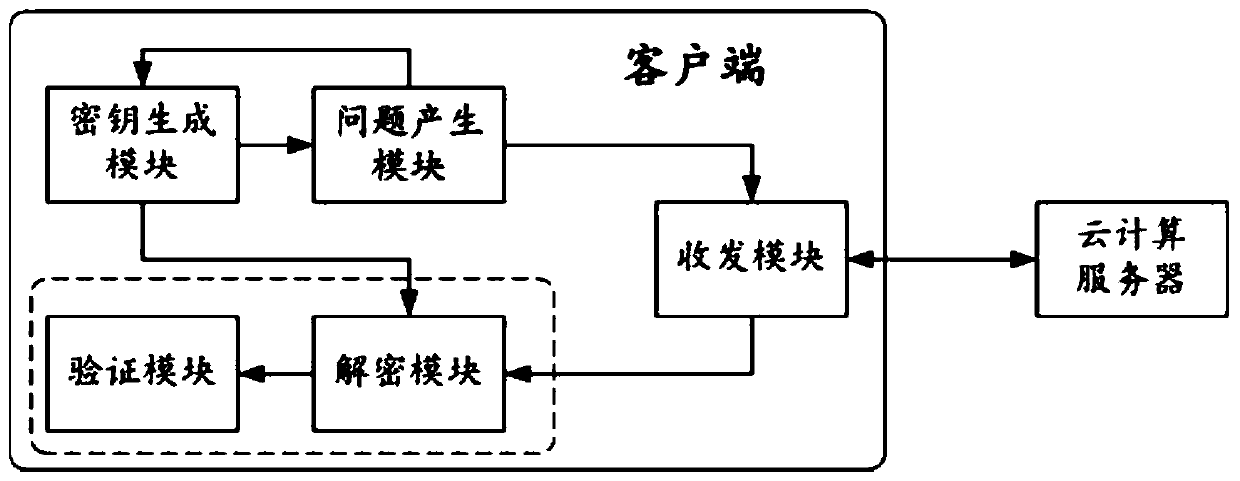
[0160] Such as image 3 As shown, this embodiment provides a cloud computing system including the foregoing embodiment two, including a cloud computing server and a client as described in embodiment two; the cloud computing server is connected to the transceiver module of the client through communication After receiving the encrypted matrix set {Y 1 ,Y 2 ,...,Y y ,...,Y ξ}, through outsourcing computing, cloud computing gets the corresponding determinant value set {det(Y 1 ),det(Y 2 ),…,det(Y z ),…,det(Y ξ )}, and feed back the cloud computing result to the transceiver module. The working process and technical effects of this embodiment can also be deduced undoubtedly with reference to Embodiment 1, and will not be repeated here.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com