An Industrial Network Border Protection System
A technology of protection system and industrial network, applied in the field of data application, can solve problems such as protection against malicious code attack of industrial protocols, harm of security defect industrial control system, etc., so as to reduce the risk of project implementation, improve security, and improve security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] In order to deepen the understanding of the present invention, the present invention will be further described below in conjunction with the examples, which are only used to explain the present invention, and do not constitute a limitation to the protection scope of the present invention.
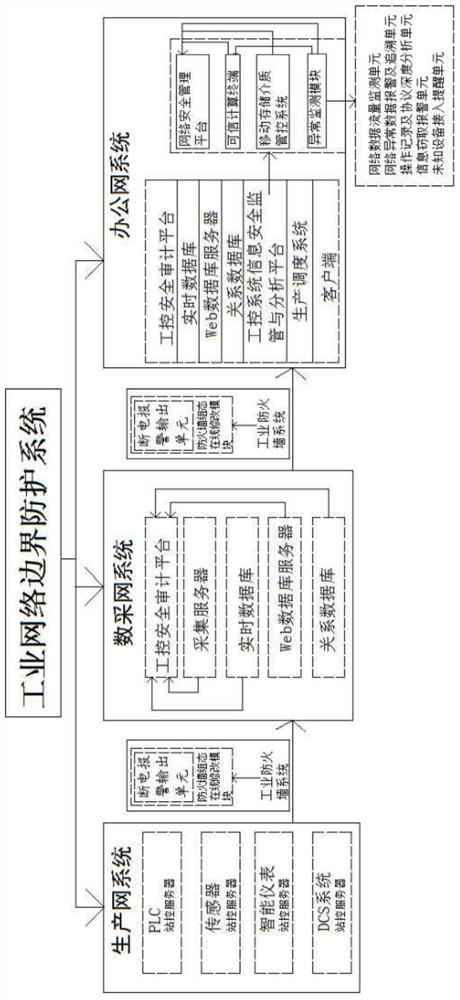
[0017] according to figure 1 As shown, this embodiment proposes an industrial network border protection system, including a production network system, a data collection network system, an office network system and an industrial firewall system, and the production network system includes PLC, sensors, smart meters and DCS systems, The PLC, sensor, smart meter and DCS system are all connected to the data acquisition network system through the industrial firewall system, and the PLC, sensor and smart meter are all connected to the station control server separately, and the production network system is connected to the data acquisition network system through the industrial firewall system...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com