A kind of anti-duplication and anti-tampering method of IC card
An anti-tampering and anti-copying technology, which is applied in the direction of electromagnetic radiation induction, can solve the problems of high deployment costs and high requirements for networking of business systems, and achieve the effect of improving the anti-tampering level
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0025] An anti-copy and tamper-proof method for an IC card in this embodiment relates to an IC card and a reader / writer.
[0026] The first code book and the second code book are stored in the reader-writer.
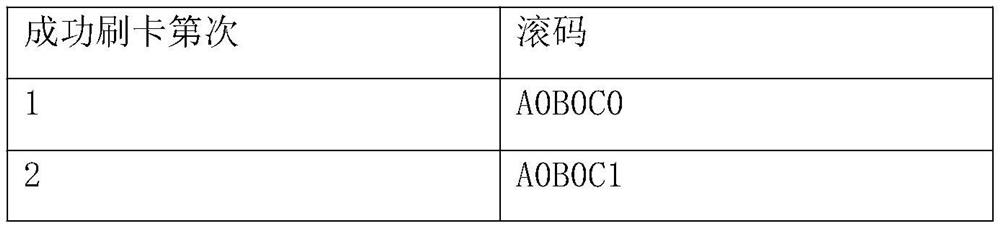
[0027] As shown in Table 1, the first password book is a binding form of "successful card swiping number" and "rolling code", which is a piece of electronic data.
[0028] Table 1:
[0029]
[0030]
[0031] In this embodiment, n is a number reaching tens of millions, and the rolling code is randomly generated by a computer and does not repeat each other. The number of n is sufficient to meet the requirements of the business system to be used for 30 years under normal card swiping frequency.
[0032] As shown in Table 2, the second codebook is a binding form of "calculation result" and "encryption code", which is a piece of electronic data.
[0033] Table 2:
[0034] Calculation results encryption code 001 C2A0F0 002 A9C3E0 003 E4B7...
Embodiment 2
[0045] An anti-copy and tamper-proof method for an IC card in this embodiment relates to an IC card and a reader / writer. The main difference between it and Embodiment 1 is that the method of this embodiment does not write the number of times of successful card swiping to the IC card.
[0046] The first code book and the second code book are stored in the reader-writer.
[0047] As shown in Table 3, the first password book is a binding form of "successful card swiping number" and "rolling code", which is a piece of electronic data.
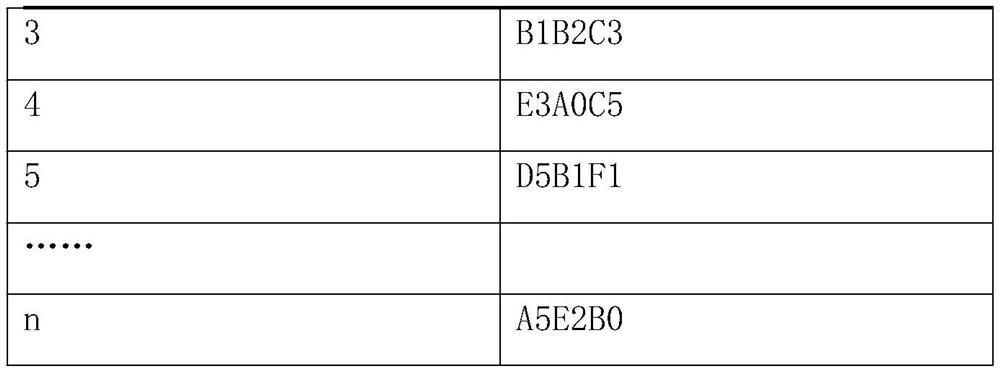
[0048] table 3:
[0049] Successfully swipe the card for the first time rolling code 1 A0B0C0 2 A0B0C1 3 B1B2C3 4 E3A0C5 5 D5B1F1 …… n A5E2B0
[0050] In this embodiment, n is a number reaching tens of millions, and the rolling code is randomly generated by a computer and does not repeat each other. The number of n is sufficient to meet the requirements of the business system to be used f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com