Decentralized Internet of Things security authentication system, equipment registration and identity authentication method
A security authentication and decentralization technology, applied in user identity/authority verification, transmission system, electrical components, etc., can solve problems such as time delay, reduce resource consumption and processing time, realize dynamic change of topology structure, good business Effects of processing responses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
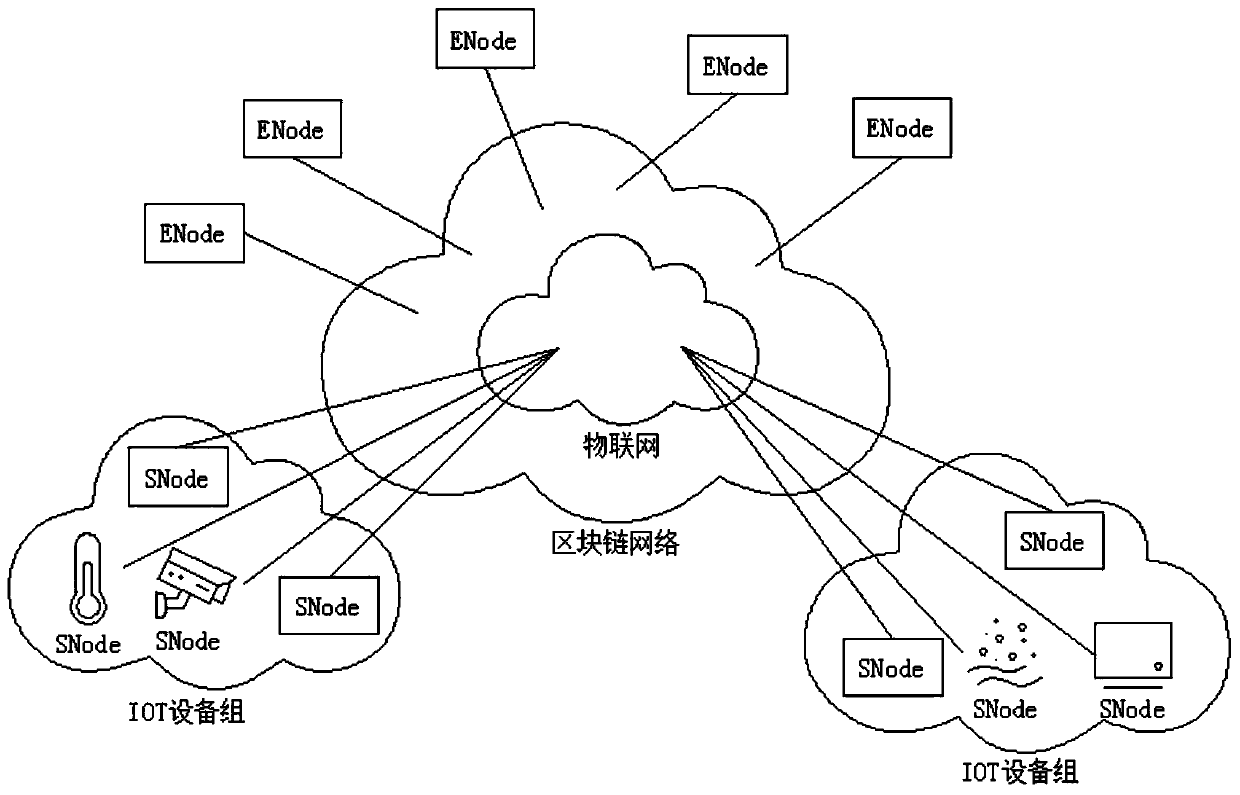
[0038] like figure 1 In the network deployment model shown, ENode (traditional gateway) builds a blockchain network responsible for maintaining the consistency of the ledger. The accounting node maintains the ledger through the following smart contracts, including: device management smart contracts, identity authentication service smart contracts and access control services Smart contract, SNode (Internet of Things equipment, user equipment) belongs to the P2P network responsible for specific production business; bookkeeping node ENode and light node SNode, product features: the operating system kernel running the blockchain node runs the modified IoT-oriented security Certified protocol stack; ENode is a general-purpose computer in the Internet, and these nodes jointly maintain the ledger; the difference between SNode and ENode is that it does not participate in the maintenance of the ledger, and only synchronizes some blocks to the local. IoT devices are light nodes in this s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com