A bgv-type multi-key fully homomorphic encryption method
A fully homomorphic encryption and homomorphic encryption technology, which is applied in the fields of information security and privacy protection, can solve the problems of large public parameters and large amount of computation in the process of calculating keys, and reduce the amount of data, size and quantity, and size Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The present invention will be described in further detail below in conjunction with specific examples, but the embodiments of the present invention are not limited thereto.
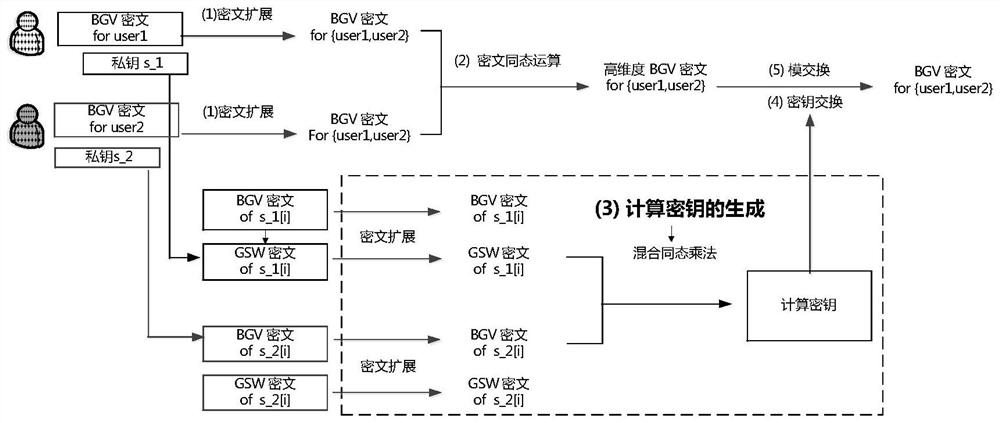
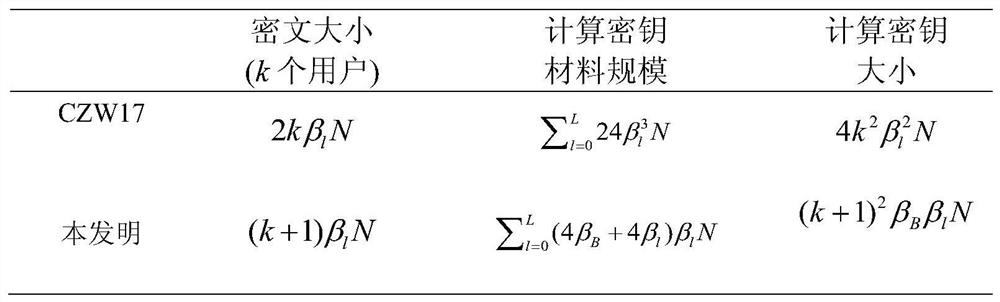
[0049] This embodiment provides an efficient BGV-type multi-key fully homomorphic encryption method, which uses ciphertext expansion technology to convert single-user ciphertext into multi-user ciphertext, thereby converting a multi-key fully homomorphic encryption scheme It is a single-key fully homomorphic encryption scheme, and uses key transformation technology and mold change technology to process ciphertext and reduce the dimension and noise of ciphertext. The BGV-type multi-key fully homomorphic encryption method can be effectively applied to secure multi-party computing among multi-users in a cloud computing environment, and has excellent characteristics such as confidentiality, ciphertext availability, anti-collusion attack, and anti-quantum attack. Compared with the BGV type multi-key ful...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com