A network security event visualization method based on text processing
A network security and security event technology, applied in the field of network security event visualization based on text processing, can solve the problems of no internal correlation mechanism and principles of security events, and the lack of a complete set of processing solutions for network security events, etc., to achieve the model Strong innovation, strong applicability, and high classification accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings, so that the advantages and features of the present invention can be more easily understood by those skilled in the art, and the protection scope of the present invention can be more clearly defined.
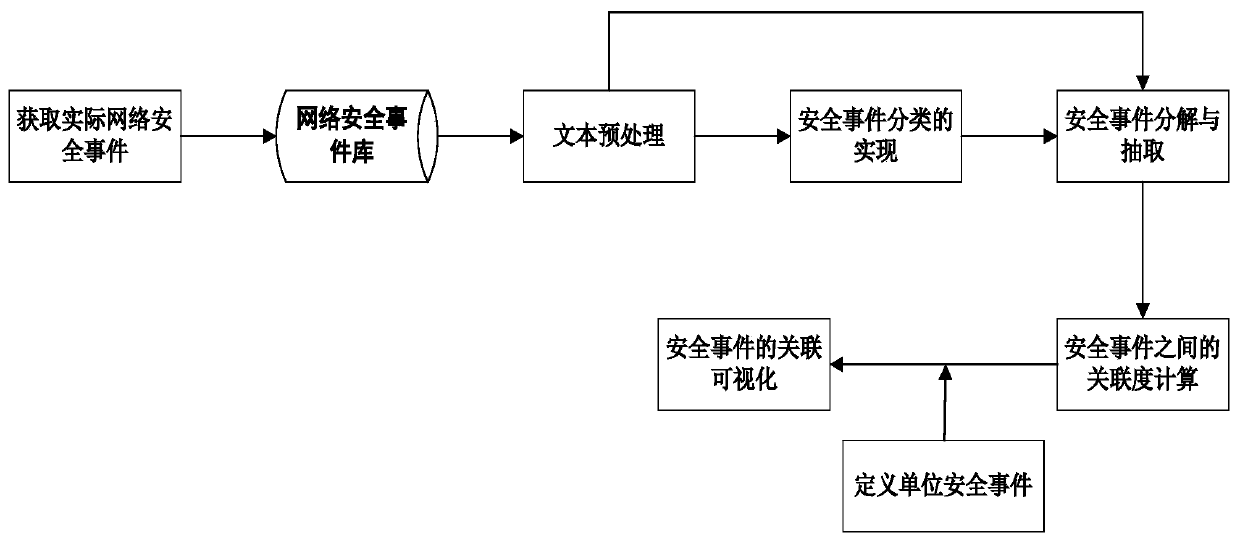
[0034] see figure 1 , the embodiments of the present invention include:
[0035] A method for visualizing network security events based on text processing, comprising the following steps:
[0036] 1) Obtain actual network security incidents: By investigating well-known security information websites at home and abroad, certain security information websites with high reliability, strong professionalism and timely information update are identified. Using the Python-based Scrapy framework to obtain text information, and using selenium to simulate the browser environment to complete the information crawling of the website built by Ajax and the page ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com