Industrial control system terminal security protection system
A terminal security and protection system technology, applied in the field of industrial control system terminal security protection system, can solve the problems of destroying confidential data of the system, inconsistent application scenarios, and lack of a centralized and unified management platform for configuration and management.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
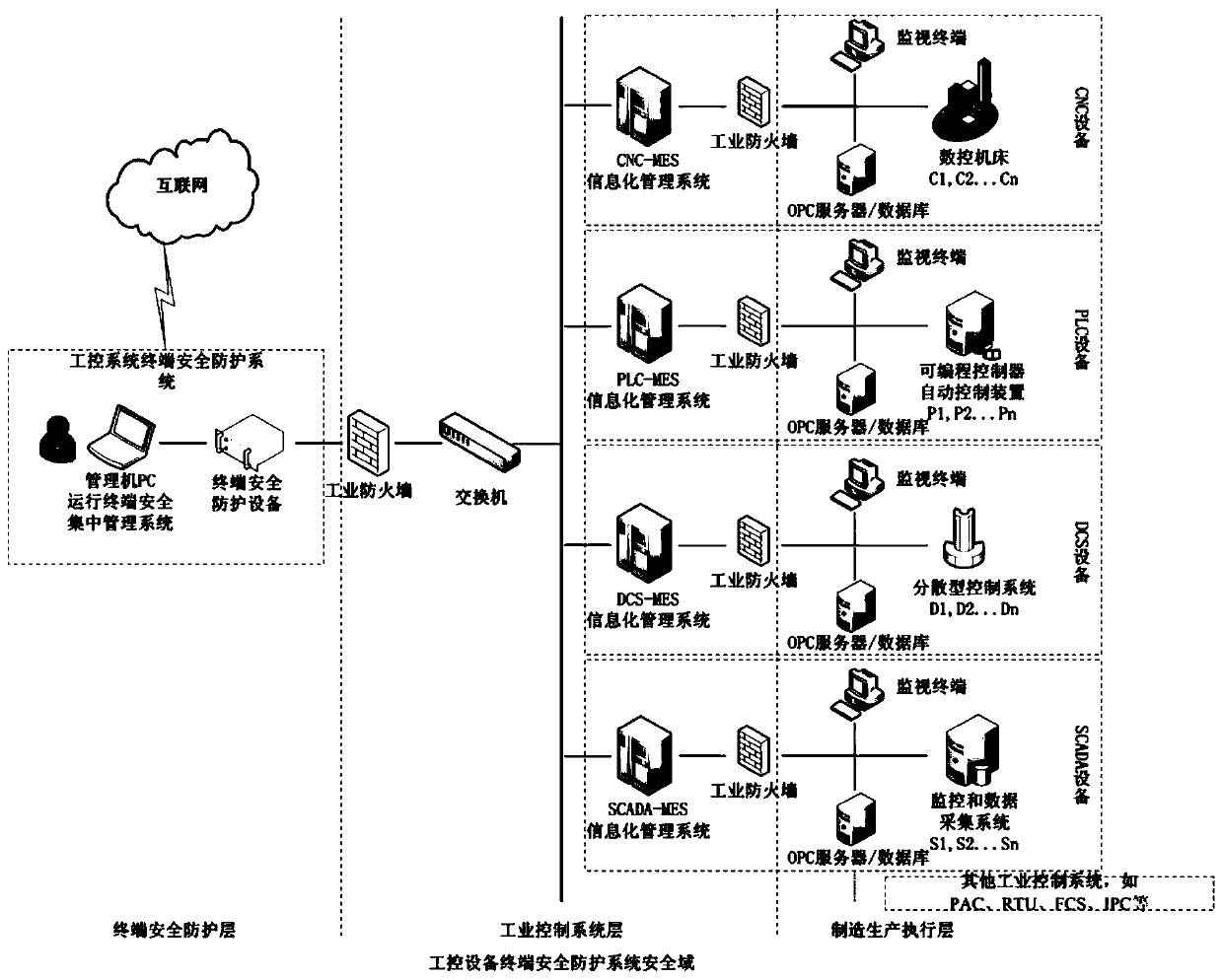
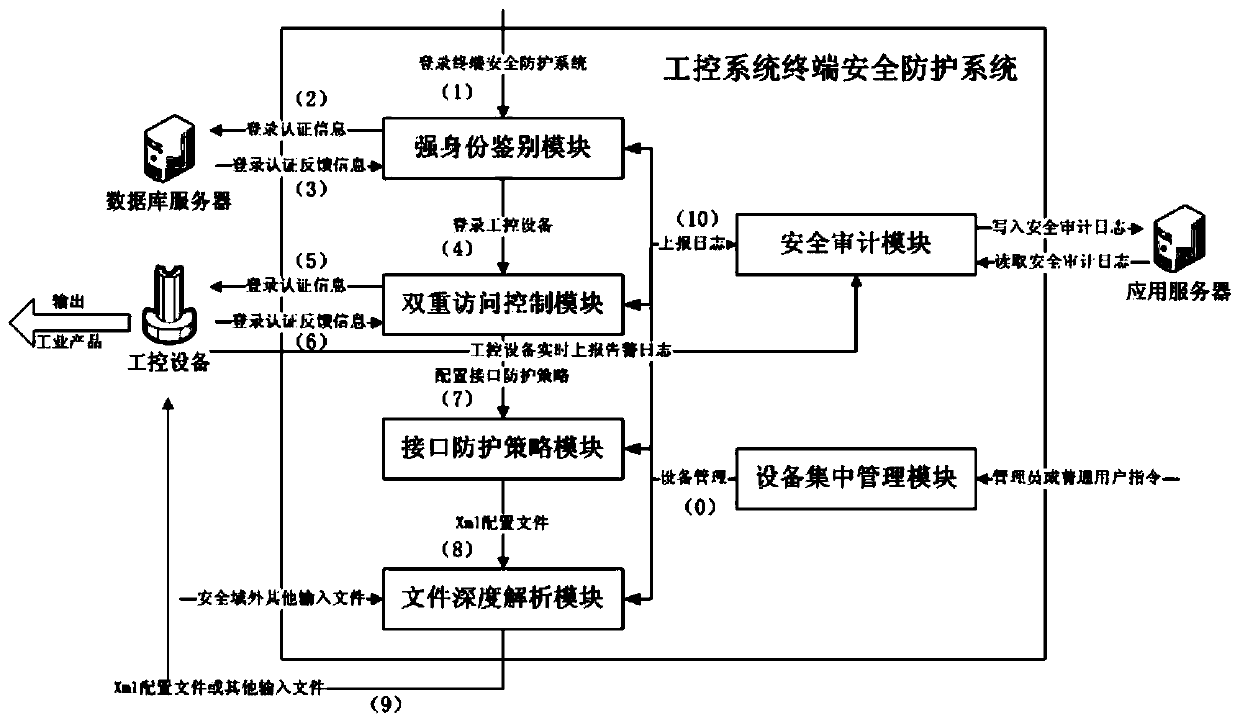
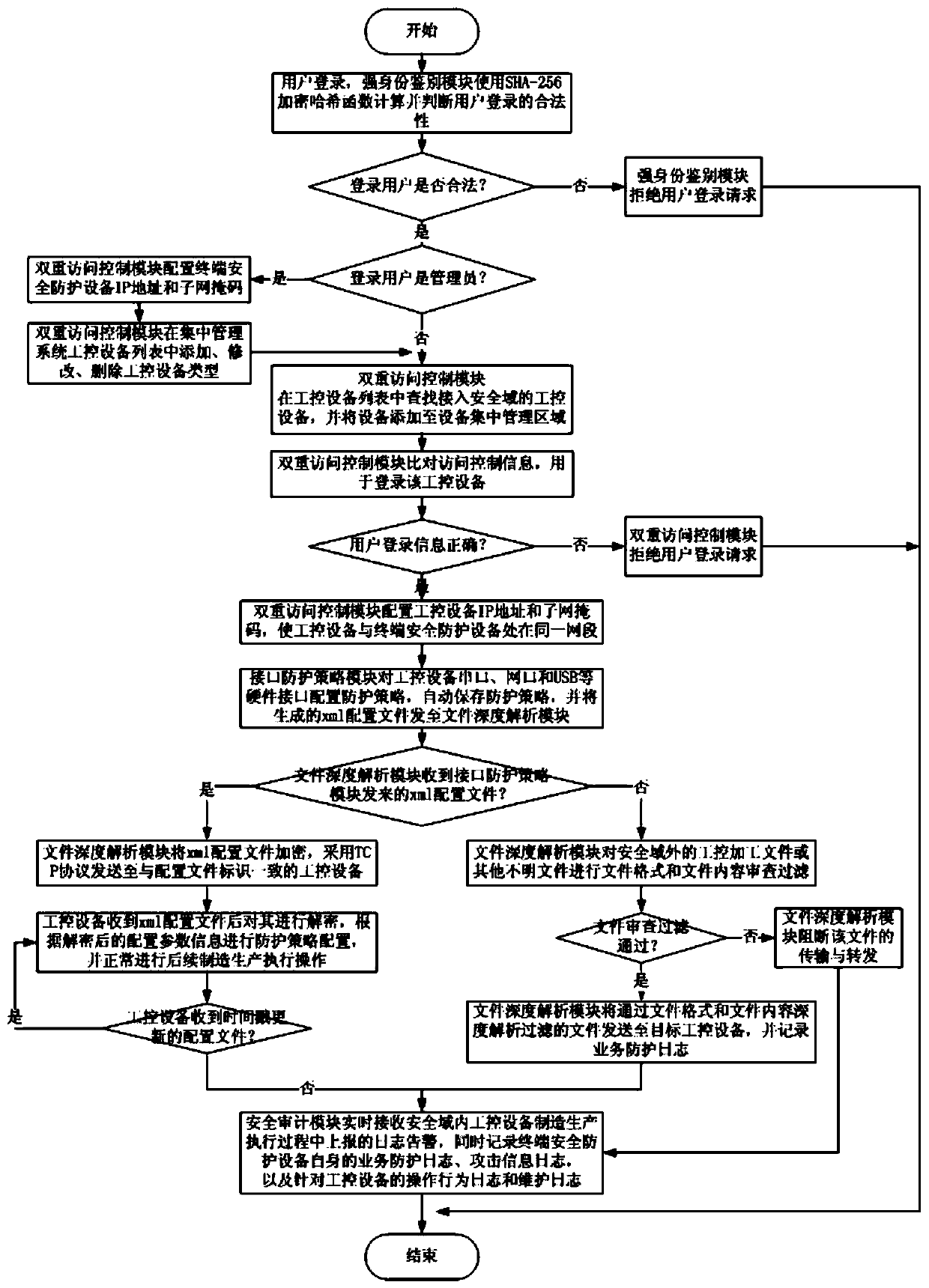
[0125] This embodiment comprehensively uses a series of technical means such as strong identity authentication, dual access control, interface protection strategy, file in-depth analysis, security audit, and centralized equipment management to provide an industrial control system terminal security protection method and system that is more suitable for simultaneous Multiple same type or different types of industrial control system equipment terminal security protection strategy for centralized and unified protection.
[0126] The method and system of the present invention are used to protect the terminal security of the industrial control system in detail below in conjunction with specific embodiments. This can be extended to a wider range of industrial control system terminal security protection applications.
[0127] Firstly, set up the security domain of industrial control equipment terminal security protection, and establish a security domain consisting of industrial contro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com