Office space authorization system and method based on QR code
An authorization system and two-dimensional code technology, applied in the field of access control processing in the office environment, can solve the problems of users not owning and inconvenient use of office space resources, and achieve the effect of improving office efficiency, being easy to implement, and reducing workload.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
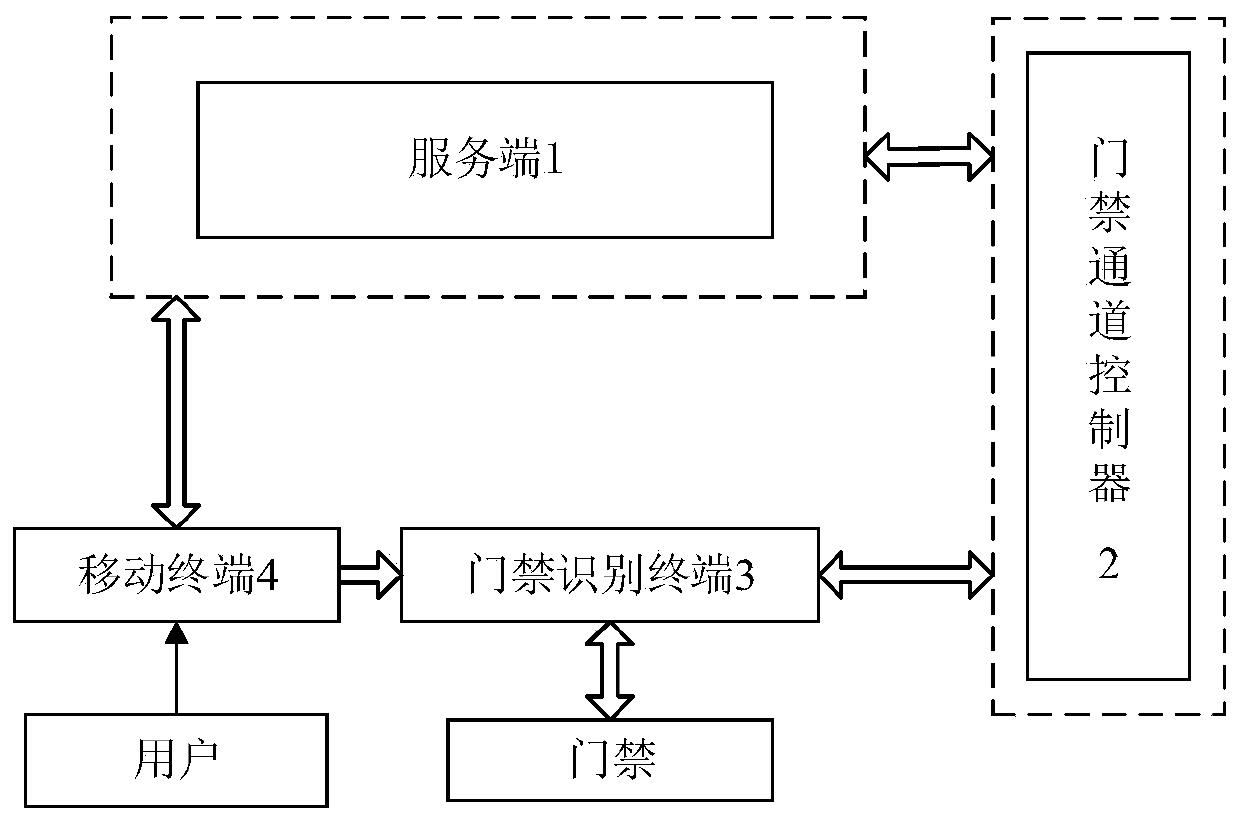
[0034] Such as figure 1 As shown, a QR code-based office space authorization system includes:
[0035] Server 1 is a WebService communication server based on C#.net technology. All application logic is encapsulated in it to process office space reservation requests and send processing results;
[0036] The access control channel controller 2 is connected to the server 1 for receiving the processing result, and centrally controls the access control switch based on the network communication authentication;
[0037] The access control identification terminal 3 is connected with the access control channel controller 2 for collecting two-dimensional codes;
[0038] The mobile terminal 4 is used for submitting an office space reservation request and presenting a two-dimensional code containing user information.
[0039] Server 1.
[0040] The functions of the mobile terminal 4 are realized based on H5 technology, and can be embedded into WeChat enterprise applications, small prog...
Embodiment 2
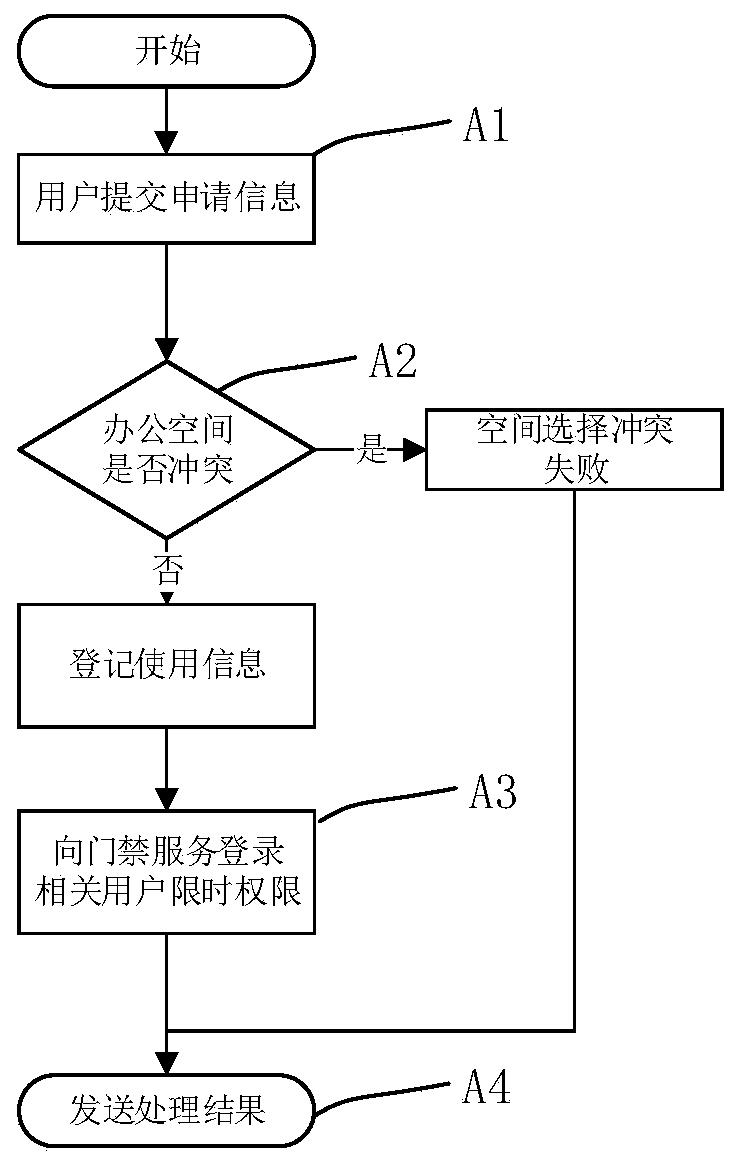
[0043] Such as figure 2 As shown, a method of using the system described in Embodiment 1 to perform authority entry includes the following process:
[0044] A1, the mobile terminal 4 submits an office space reservation request to the server 1;
[0045] A2, server 1 judges whether the office space conflicts, if yes, the processing result is failure, and proceeds to step A4, if not, registers the office space usage information, and proceeds to step A3;
[0046] A3, server 1 updates the user's time-limited authority;
[0047] A4, the server 1 sends the processing result to the mobile terminal.
Embodiment 3
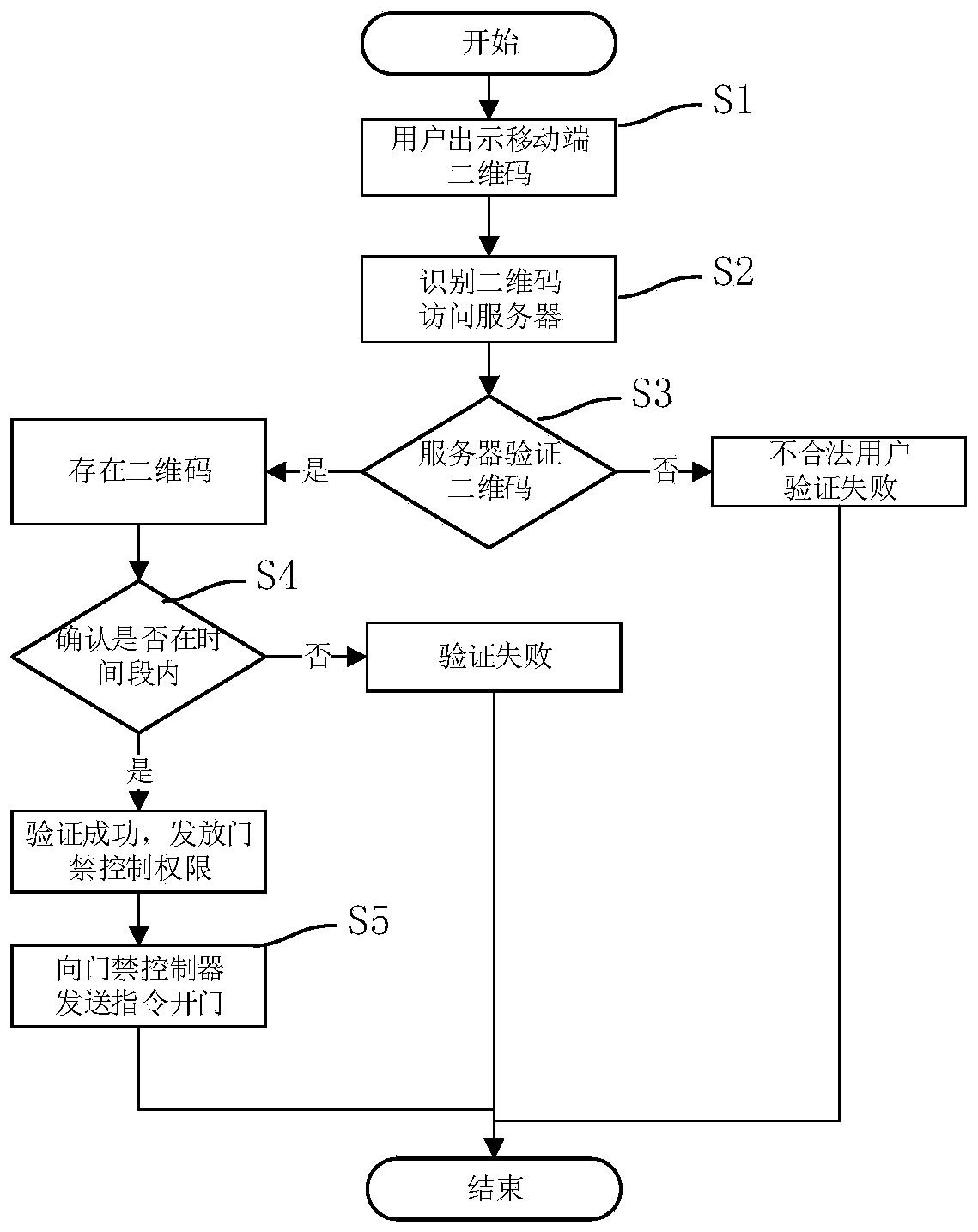
[0049] Such as image 3 As shown, a method of using the system described in Embodiment 1 to carry out access control verification includes the following processes:
[0050] S1, the mobile terminal 4 displays a two-dimensional code to the access control identification terminal 3;
[0051] S2, the access control identification terminal 3 identifies the two-dimensional code and sends it to the server 1;
[0052] S3, the server 1 reads the information in the two-dimensional code, if a valid user is verified, then enter step S4, otherwise end;
[0053] S4, the server 1 confirms whether the authority of the user is within the effective period, if so, then sends information to the access control channel controller 2, if not, then ends;
[0054] S5, the access control channel controller 2 controls the corresponding access control switch to open.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com