Attribute revocation method
A technology of attributes and algorithms, applied in the field of data security, which can solve problems such as a large amount of computation, updating proxy keys, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
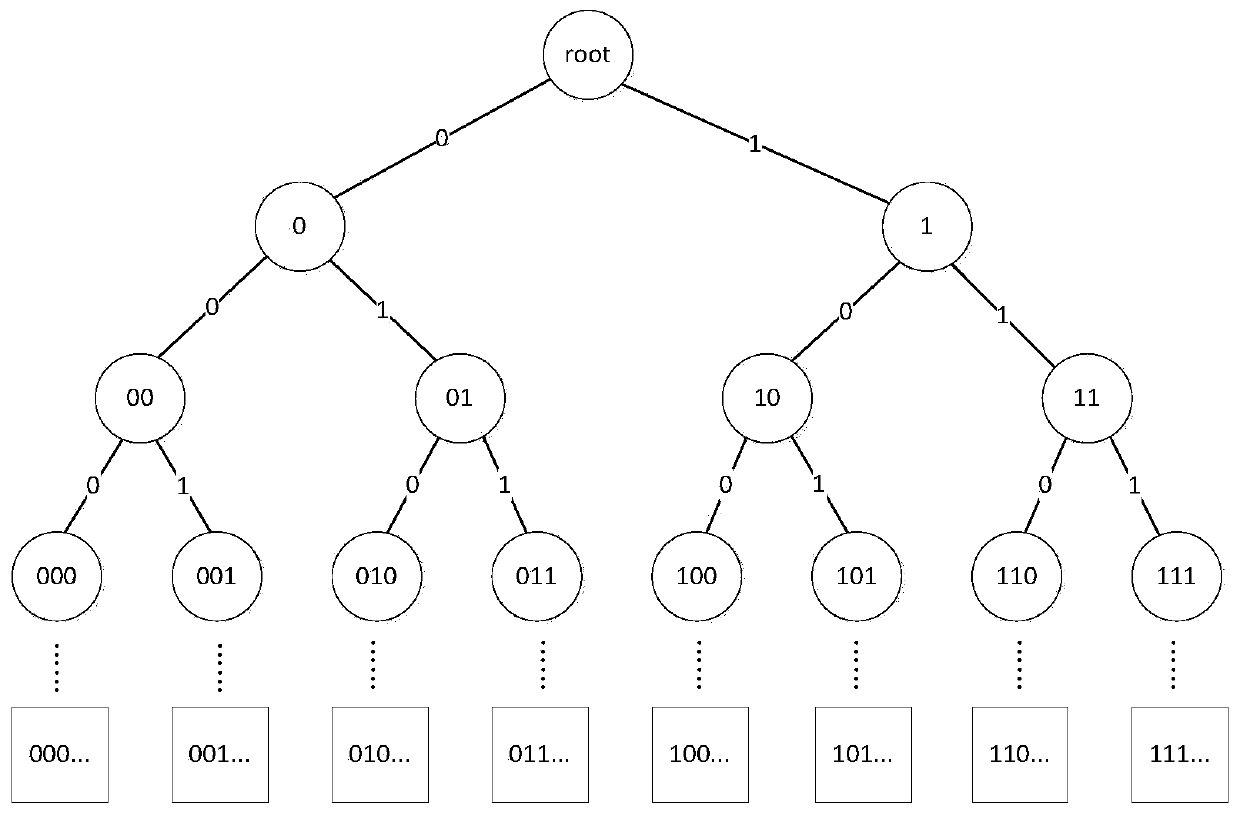
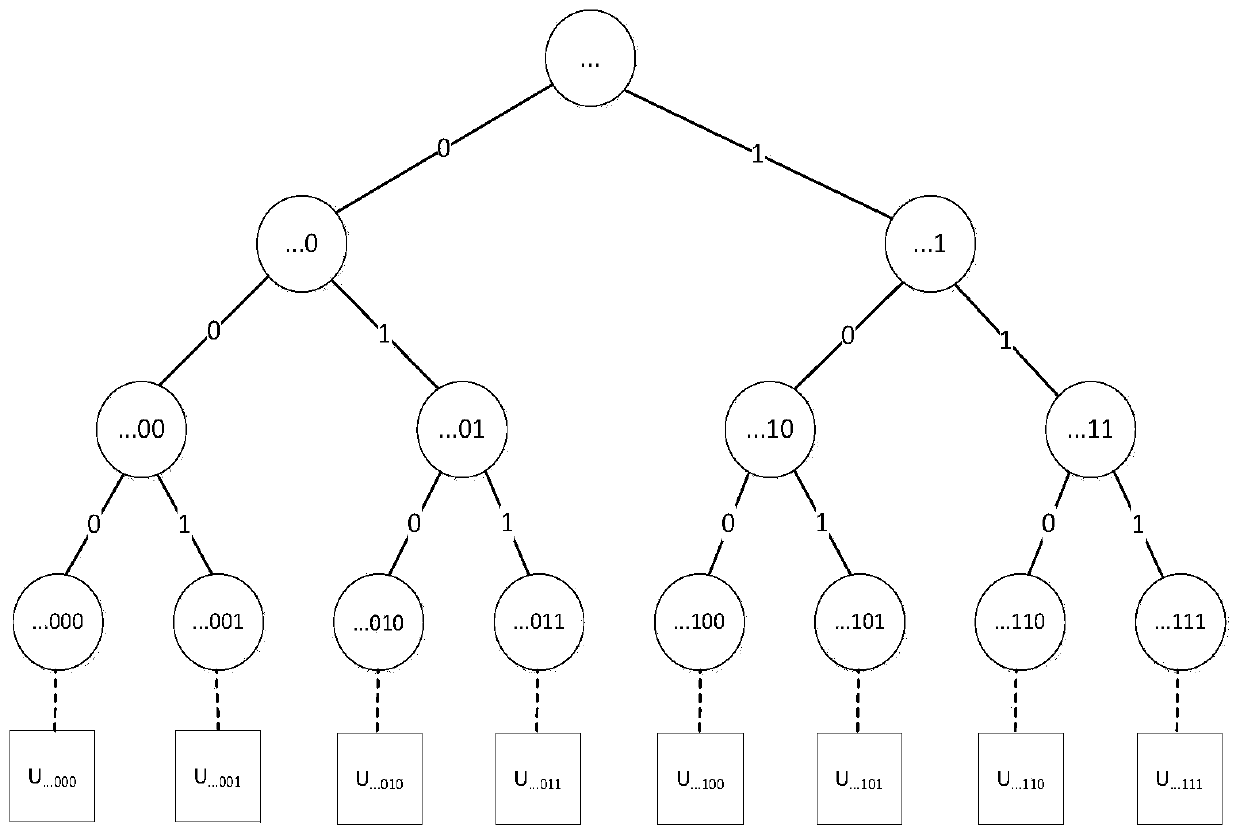
[0106] The invention provides a method for revocation of attributes. Firstly, a reasonable organization method of user space is proposed, and these users are randomly divided into irrelevant groups. The revocation of user rights only affects other users in the group. The number of affected users is the number of active users in the group. The more groups are divided, the fewer active users are assigned to each group, and the fewer other users are affected. However, the smaller the group size, the larger the storage overhead required. Therefore, the division of groups depends on the specific circumstances of the use of attributes.
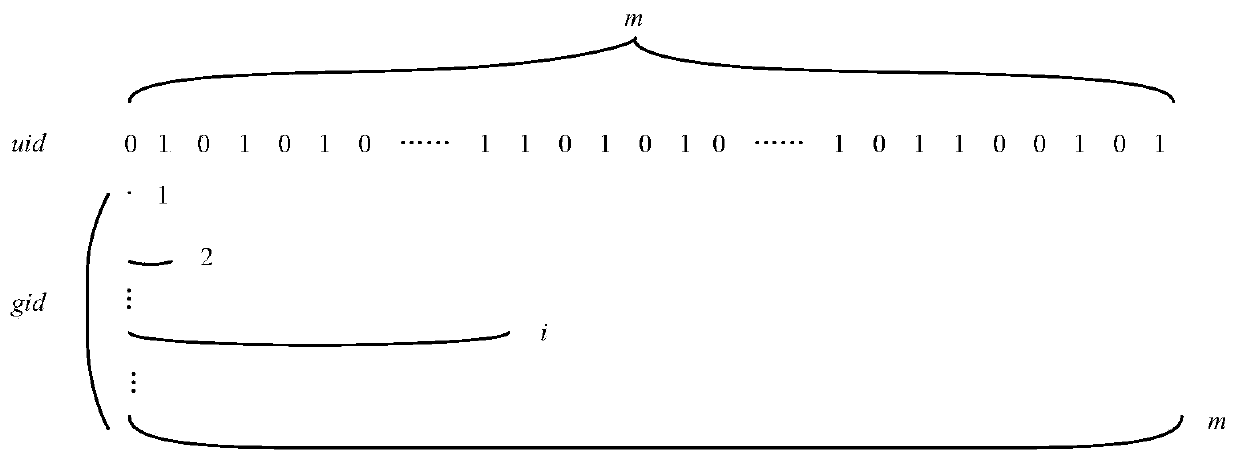
[0107] On the other hand, with the increase of attribute usage time, the proportion of the number of users in the depleted user set in the group it belongs to is on the rise. The present invention introduces a minimum coverage mechanism. What is stored in the revoked user group is a group identification code that can represent a user group instead ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com